At present, many computers are connected via numerous networks. Monitoring all traffic and having something to filter out good and harmful traffic is critical, and we achieve this with an application or service known as a firewall.
Early firewalls were essential software that filtered data traffic based on the sender’s IP address, port number, domain name, etc. However, newer firewalls can now read the data supplied and filter it accordingly.
As we all know, many servers are built only on Linux machines, and proper firewalls are required to control traffic on such servers. Numerous providers are in the market for this purpose, and we will discuss the top ten.
One comes pre-installed, and other utilities can be installed on your system/distribution, while the other is independent of all pre-installed firewalls; these firewalls come in the form of a hardened OS that you must install before it can provide you with 360-degree visibility and security.
Should You Use A Firewall In Linux?
In a time when hackers have the best technology, you must not leave any gap, no matter how little.
Linux servers are widely used, making utilizing a firewall to prevent DDOS and DOS attacks even more vital. Thus, data monitoring and filtering are crucial, and a firewall reduces server and machine load if attacked. They are filtering unnecessary data packets.
New firewalls can improve data filtering, and machine learning models can teach the system to increase data filtering over time.
Do Hackers Use Firewalls?
Hackers Mostly Bypass The Firewall Instead Of Using It.
From a hacker’s perspective, a firewall is useless in any attack. Still, if we look at it from another perspective, even the hacker has to protect his/her system, and for that, they might need a firewall to implement it on their system.
This was for a black hat hacker, but an ethical hacker needs to use a firewall to protect their organization from malicious requests coming to their servers.
In conclusion, whether a hacker is ethical or non-ethical, a firewall will be required to prevent them or their organization from being hacked.
What Is The Strongest Element In Network Security?
Before implementing network security, you must understand the network elements, such as routers, switches, bridges, etc…
Among all the elements that can provide network security, an IPS is one of the most powerful and is equipped with a firewall in the front line.
IPS is the most vital element of network security because it not only monitors all the malicious activities or requests coming to the server but it also automatically tries to mitigate the problem that has arisen or that might arise in the system/network due to the malicious request
Here Are Our Picks For 10 Best Linux Firewalls In 2025
- OPNsense – Feature-rich, easy-to-use firewall with a web-based interface and extensive plugins.
- Shorewall – Flexible and robust firewall configuration tool for complex networking setups.
- Iptables – Powerful command-line firewall utility for managing Linux kernel packet filtering rules.
- pfSense – Highly customizable firewall and routing platform with a web-based interface.
- Endian Firewall – Comprehensive UTM solution combining firewall, antivirus, and VPN functionalities.
- Smoothwall Express – User-friendly, open-source firewall with intuitive web-based management.
- Vuurmuur – Graphical front-end for managing Netfilter/iptables with real-time monitoring.
- IPCop Firewall – Easy-to-use firewall distribution aimed at small and home office networks.
- ClearOS – Unified threat management and network gateway solution with a simple web interface.
- OpenWRT – Versatile, open-source firmware providing advanced firewall and routing capabilities.
Best Linux Firewalls And It’s Features
| Best Linux Firewalls 2025 | Features | Stand-alone feature | Pricing | Free Trial / Demo |
|---|---|---|---|---|
| 1. OPNsense | 1. Firewall 2. MultiWan 3. Virtual Private Network 4. Hardware Failware 5. Intuitive User Interface 6. Intrusion Detection & Prevention 7. Two-Factor Authentication |
1. High-level firewall configuration 2. Configuration based on zones 3. Help with several interfaces 4. Versatile use 5. Easy Installation |
Free, open-source software | Yes |
| 2. Shorewall | 1. High-level firewall configuration 2. Configuration based on zones 3. Help with several interfaces 4. Versatile use 5. Easy Installation |
Flexible and powerful firewall management | Free, open-source software | No |
| 3. Iptable | 1. Easily accessible 2. Fast 3. User-defined Chain 4. Simple Use 5. Customization in rules |
Command-line interface for packet filtering | Free, built into Linux | No |
| 4. pfSense | 1. Load balancer 2. Firewall 3. Hardware failover 4. Web Interface 5. Easy configuration 6. Traffic Shaper |
Comprehensive features and customization options | Free, open-source software | Yes |
| 5. Endian Firewall | 1. Free open-source a software solution 2. Hardware solution 3. Virtual solution 4. Powerful yet simple to use 5. Mail and Web security 6. Secure Remote access |
Integrated security and network services | Free community edition available | Yes |
| 6. Smoothwall Express | 1. Stable and Secure Linux Firewall Distribution. 2. Developed Linux and Opensource movements for the user base. 3. Highly configurable functions 4. Reliable Support to the IPCop Linux user base. 5. User-friendly environment for the Public to discuss 6. Easy access to request assistance. |
User-friendly with robust filtering | Free, open-source software | No |
| 7. Vuurmuur | 1. No knowledge of IP Table is required 2. Supports Ipv6 3. Ncurses GUI, no X required. 4. Simple port forwarding 5. Easier NAT Setup 6. secure default policy |
GUI for Iptables management | Free, open-source software | No |
| 8. IPCop Firewall | 1. Installation and setup is made easy 2. Intrusion Detection 3. Custom Firewall 4. Content Filter Black 5. Bandwidth Management 6. Domain Controller |
Easy-to-use with basic features | Free, open-source software | No |
| 9. ClearOS | 1. Installation and setup is made easy 2. Intrution Detection 3. Custom Firewall 4. Content Filter Black 5. Bandwidth Management 6. Domain Controller |
Unified threat management system | Free, subscription for extras | Yes |
| 10. OpenWRT | 1. Extensibility 2. 3000+ application packages standardized 3. Utilize native dual-stack connectivity 4. IPv4/IPv6 transitioning. 5. Block ads on your router 6. Smart Queue Management |
Customizable router firmware with firewall | Free, open-source software | No |
1. OPNsense
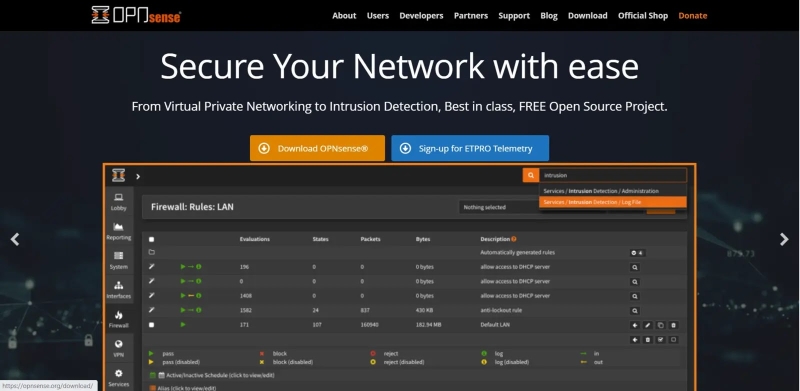
OPNsense
Year: 2014
Location: Netherlands
Open-source and free OPNsense provides all the essentials for Linux system protection. Multi-wan in OPNsense Linux Firewall helps balance network load and supports failover. OPNsense setup is straightforward using plugins like zero tiers.
The complete setup takes minutes. This plugin covers monitoring. Using common address redundancy technology, OPNsense Linux Firewall provides smooth failover service with maximum availability. Free Range Router provides pluggable OSPF and BGP capabilities.
They have the most uncomplicated user interface and an integrated search feature among open-source firewalls—comprehensive web proxy with access control and external blacklists to filter undesirable traffic.
Other solutions are firewall aliases and DNS blacklisting. Adblocking made easy!
Why Do We Recommend It?
- Linux firewalls like OPNsense may filter and regulate network traffic by IP addresses, ports, protocols, etc.
- Linux-based firewalls use NAT to translate private IP addresses to public IP addresses and vice versa.
- Linux firewalls support OpenVPN, IPsec, and others.
- Linux firewalls can detect and prevent network attacks with IDS/IPS.
- Web filtering lets administrators regulate web traffic by categories, URLs, or content on Linux firewalls.
- Linux firewalls monitor network traffic, log events, and generate reports.
- QoS lets Linux firewall administrators prioritize network traffic.
- Linux-based firewalls with high availability settings provide redundant network operation in case of hardware or software failure.
| What is Good ? | What Could Be Better? |
|---|---|
| 1. Proper Documentation | 1. Logging can be improved |
| 2. It is Easy to setup | 2. More shell-based configuration is required rather than command shell-based |
| 3. Easily Scalable | |
| 4. Easy Implementation |
Price
You can get a free trial and personalized demo from here
2. Shorewall
Shorewall
Year: 2020
Location: Boston, USA
Shorewell Linux Firewall is a lightweight firewall configuration and traffic management utility for Linux. It can be used as a dedicated firewall, multi-function gateway/router/server, or standalone GNU/Linux system.
The Shorewall firewall was designed to abstract firewall configuration to a higher level than ordinary tables. Because it doesn’t employ chained compatibility mode, Shorewall can use Netfilter’s connection status tracking.
This approach allows users to operate on a set of computers connected to an interface instead of addresses by dividing interfaces into zones with varying access levels.
The two-interface documentation on the Shorewall website is used to configure the Shorewell Firewall for Linux on the leading site. In Shorewall, users can quickly and comprehensively deploy zone policies.
Why Do We Recommend It?
- Using a sophisticated configuration vocabulary, Shorewall simplifies defining and managing firewall rules.
- Shorewall is compatible with NAT, a protocol that translates IP addresses from the private to the public sphere.
- With QoS rules, Shorewall can prioritize and regulate network traffic.
- Shorewall works with a variety of VPN protocols.
- Shorewall uses connection monitoring and stateful inspection to monitor and control all network connections.
- Shorewall records the firewall and network activity.
- Advanced users can modify the firewall’s behavior using scripting and extensions for Shorewall.
- Firewall rules for IPv6 can be set up and managed with Shorewall by administrators.
- Shorewall partitions network interfaces into logical zones to facilitate segment- or interface-level firewall policy administration.
| What is Good? | What Could Be Better? |
|---|---|
| 1. Provides simple configuration syntax. | 1. Needs Better support system |
| 2. Controls firewall rules precisely, making it configurable. | 2. Needs GUI |
| 3. Provides thorough network traffic logging for troubleshooting. |
Price
You can get a free trial and personalized demo from here
3. iptables
iptables
Year: 1998
IPTables (Linux Firewalls) can be used for personal computing or the entire network. Using IPTables, we will define a set of rules to monitor, allow, or block incoming or outgoing network packets.
Iptables uses four types of by-default tables, and those tables contain different chains (5 types in total); let’s start understanding the use of these tables and chains
1. Filter
This table is responsible for the entrance of any packet and deciding which packets to allow; this table uses these three different chains
- Input – the rules in this chain control the packets the server receives.
- Output – this chain controls the packets for outbound traffic.
- Forward – this set of rules controls the packets routed through the server.
2. Network Address Translation (NAT)
This table is used when a network can not be accessed directly, and NAT (Network Address Translation) is required. When the destination or source of the packet has to be altered, the NAT table is used.
It includes the following chains:
- Prerouting – this chain assigns packets as soon as the server receives them.
- Output
- Postrouting – the rules in this chain allow packet changes to be made after they leave the output chain.
3. Mangle
The Mangle table adjusts the IP header properties of packets. The table has all the following chains we described above:
- Prerouting
- Postrouting
- Output
- Input
- Forward
4. Raw
The raw table has two of the chains we previously mentioned:
The Raw table is used to exempt packets from connection tracking.
- . Prerouting
- Output
5. Security (Optional)
Some versions of Linux also use a Security table to manage special access rules. This table includes input, output, and forward chains, much like the filter table.
Why Do We Recommend It?
- With iptables, administrators can filter network traffic using IP address ranges, ports, protocols, and packet properties.
- IPtables supports Network Address Translation for IP address and port translation.
- Iptables perform stateful packet inspection by monitoring network connections and implementing rules.
- Monitoring connections are incorporated into iptables.
- Iptables lets administrators monitor firewalls and network traffic.
- NAPT is an iptables functionality. She is also known as port forwarding or destination NAT.
- The QoS capabilities of iptables allow network managers to prioritize specific traffic.
| What is Good? | What Could Be Better? |
|---|---|
| 1. Cheap open source firewall with decent performance | 1. Packets can be seen through different chains |
| 2. very versatile controller tool for the command line. | 2. Hard to manage high-packet rates of small UDP packets |
| 3. The concept is easy to understand. |
Price
You can get a free trial and personalized demo from here
4. pfSense
pfSense
Year: 2006
Location: Austin, Texas, United States.
pfSense firewall is an independent operating system, so you can either virtual host it on your system (running OS) or install it on a dedicated workstation. It is possibly the most feature-rich firewall available, but this makes it difficult to use.
While the interface strives to make things easy to grasp, there is a learning curve. You can install the preferred ISO file from the main page based on your needs. Then, you will set up the entire virtual machine or dedicated system correctly.
That will serve as your control center for operating the tool. Enter the username admin and the password pfSense, then click SIGN IN. When using this program for the first time, making some basic adjustments and changes would be best.
After adjusting, your Linux Firewall will be ready to use. You can also install a pre-installed and modified VM, eliminating the need to change and configure it. If you choose to employ this strategy, it is ready to go.
Why Do We Recommend It?
- Administrators can build and administer firewall rules in pfSense to regulate network traffic and prevent unauthorized access.
- Network Address Translation lets pfSense convert private IP addresses to public ones and vice versa.
- pfSense supports IPsec, OpenVPN, L2TP, and PPTP VPNs.
- Snort and Suricata can integrate with pfSense to operate as an IDS/IPS.
- pfSense administrators may shape and prioritize network traffic using QoS rules.
- Web filtering lets administrators manage and monitor web traffic using pfSense.
- The captive portal in pfSense offers guest network access with user verification.
| What is Good ? | What Could Be Better? |
|---|---|
| 1. A web-based GUI simplifies setup and management. | 1. No centralized management system |
| 2. Very versatile as a firewall, router, VPN gateway, and more. | 2. Early configuration is difficult |
| 3. A large, active user community with extensive documentation and support | |
| 4. Description Supports packages and add-ons for customized functionality. |
5. Endian Firewall
Endian Firewall
Year: 2005
Location: Italy
The Endian Linux Firewall is a complete Unified Threat Management (UTM) solution for your Linux security solutions. Endian was created to be the most accessible security product to install, configure, and use. Everything is recorded so that you can read and understand each step.
Endian UTM will filter introductory emails and give online security to help protect your home network. The professional edition of Edian Linux Firewall offers real-time web and email filtering with Advanced Content Security (ACS), supported by CYREN and Bitdefender Anti-malware Engine.
Edina Linux Firewall also includes a VPN to help you establish a secure connection while keeping your identity disguised.
A professional version of It provides increased scalability and features like Active Directory/LDAP authentication, two-factor authentication, and top-tier support for mobile platforms (SSL, L2TP, XAuth).
With live monitoring and reporting, you’ll have real-time data in front of you. To receive features like graphs and a detailed historical view of the data, you must purchase the professional version of the Edian Linux Firewall.
Why Do We Recommend It?
- The powerful Endian Firewall engine allows admins to build and manage firewall rules to control network traffic entering and leaving the system.
- The Endian Firewall supports Network Address Translation, converting private IP addresses to public ones.
- VPN capability in the Endian Firewall encrypts site-to-site and remote access communications.
- Snort and Suricata, popular IDS/IPS systems, work with I Endian Firewall.
- Web filtering helped the Endian Firewall control and monitor network traffic.
- Endian Firewall protects emails from viruses and spam.
- Endian Firewall administrators can prioritize network traffic using QoS rules.
- The Endian Firewall logging and monitoring tools analyze network traffic and firewall events.
| What is Good? | What Could Be Better? |
|---|---|
| 1. Not many integration options available | 1. Not many integration options are available |
| 2. Reliable and faster solution | 2. Fewer documentation to support |
| 3. Implementation is very fast | |
| 4. Nomenclature of network interfaces is impressive |
6. Smoothwall Express
Smoothwall Express
Year: 2000
Location: Yarfort, with a USA office in Charlotte, North Carolina
Smoothwall Express is a network Linux firewall developed by the Smoothwall Open Source Project Team. It is a free firewall with a security-hardened GNU/Linux operating system and a user-friendly web interface.
This firewall is designed for both home users and small enterprises. Despite being free of charge, Smooth Wall Express The Linux firewall uses the same research and functionality as other commercial solutions, making it a reliable solution.
This Linux firewall can be an alternative to EFW because it requires a virtualized shell or hardware environment. Smooth Wall also offers a fine-tuned corporate solution for several industries, including education, the public sector, and business use cases.
Installation is also fairly straightforward due to the documentation supplied, and if you get stuck, you can seek assistance from the large community. SmoothWall reformats the hard drive during installation and does not allow you to store any data or create custom partitions.
You must select which network interfaces you will use: Ethernet, ISDN, or USB ADSL. Smoothwall Ltd’s security products are geared toward commercial customers and include support packages. Smoothwall Express is a free, open-source firewall for small and home office customers.
Why Do We Recommend It?
- Smoothwall Express’s robust firewall engine lets administrators set and manage firewall rules to restrict network traffic.
- Smoothwall Express supports VPN for secure remote access and site-to-site connectivity.
- Smoothwall Express controls and monitors web traffic with web content filtering.
- Smoothwall Express works with Snort and Suricata, which are open-source IDS/IPS systems.
- Smoothwall Express lets managers prioritize network traffic by QoS.
- Bandwidth monitoring in Smoothwall Express tracks network consumption and traffic trends.
- DHCP and DNS ease network deployment and management in Smoothwall Express.
| What is Good? | What Could Be Better? |
|---|---|
| 1. Low-end maintenance. | 1. Does not support SSD. |
| 2. Often free, making it cost-effective for small businesses. | 2. Users without IT knowledge may struggle to configure. |
| 3. Has an active user community for support and add-ons. |
7. Vuurmuur
Vuurmuur
Vuurmuur Linux Firewall is a robust iptables-based firewall management. The Linux configuration process is basic and easy to learn, yet sophisticated settings are possible. Setup with Ncurses GUI offers secure administration via SSH or PUTTY shell.
This enables easy firewall control and administration from any system. Vuurmuur offers traffic shaping (packet shaping) and extensive monitoring facilities that let administrators view logs, connections, and bandwidth utilization in real-time.
Vuurmuur Linux Firewall is open-source software licensed under the GNU GPL. Check out the Features and Screenshots. Linux-based IPCop Firewall protects networks. The architecture focuses on running more firewall code in attack-prone areas.
Sendmail and FTP daemon requests are also monitored. The lengthy instructions for tool installation include updated setup and other parameters. During setup with PXE boot, you must boot from a CDROM, Floppy, USB key, or network.
It controls features granularly for multi-facet web traffic installation. IPCop 2.1.9, released 2019-02-23, is the newest stable version.
IPCop v2 hardware requirements include a 486 CPU, 512 MiB disk space, 64 MiB RAM, 2 or 1 network card, analog modem, ISDN card, GSM, UMTS, and internet connectivity. Home and SOHO users are targeted.
Why Do We Recommend It?
- A simple interface makes firewall rule generation and management easy with Vuurmuur.
- Network Address Translation lets Vuurmuur convert private IP addresses to public ones.
- Vuurmuur lets managers shape network traffic depending on different factors.
- Vuurmuur tracks network connections.
- Vuurmuur logs firewall and network events.
- Vuurmuur lets the firewall understand and handle application-layer network protocols via application-level gateways.
- Vuurmuur lets administrators specify destination NAT (port forwarding).
| What is Good? | What Could Be Better? |
|---|---|
| 1. It protects computers/networks via secure programming. | 1. Old PCs only boot from CDROM, while network boot requires a net card with a boot ROM. |
| 2. Its web interface is very user-friendly and makes usage easy. | 2. User-created rules take longer to configure because none are added by default. |
| 3. Benefits from user community and development. | |
| 4. Automates and scripts firewall rules. |
8. IPCop Firewall
IPCop Firewall
Year: 2001
Location: Bengaluru, State of Karnataka
Linux-based IPCop Firewall protects networks. The architecture focuses on running more firewall code in attack-prone areas. Sendmail and FTP daemon requests are also monitored. Long and extensive instructions for tool installation include updated setup and other parameters.
During setup with PXE boot, you must boot from a CDROM, Floppy, USB key, or network. It controls features granularly for multi-facet web traffic installation. IPCop 2.1.9, released 2019-02-23, is the newest stable version.
IPCop v2 hardware requirements include a 486 CPU, 512 MiB disk space, 64 MiB RAM, 2 or 1 network card, analog modem, ISDN card, GSM, UMTS, and internet connectivity. Home and SOHO users are targeted.
Why Do We Recommend It?
- The sophisticated IPCop Firewall engine allows admins to build and maintain firewall rules to control network traffic entering and leaving the system.
- IPCop Firewall supports NAT, so you can quickly convert private to public IPs and vice versa.
- IPCop Firewall supports IPsec and OpenVPN natively.
- IPCop Firewall, an open-source IDS/IPS, works with Snort.
- IPCop Firewall’s web proxy and content screening simplify web traffic management.
- QoS rules can prioritize network traffic with IPCop Firewall.
- IPCop Firewall streamlines network deployment and maintenance with DHCP, DNS, and bandwidth monitoring.
| What is Good? | What Could Be Better? |
|---|---|
| 1. The latest version supports multiple architectures | 1. It protects computers/networks via secure programming. |
| 2. Has an active user community for support and add-ons. | 2. Potential for outdated software and limited commercial support. |
| 3. Allows internet access control using web proxy and URL filtering. | |
9. ClearOS
ClearOS
Year: 2009
Location: Milwaukee, Wisconsin
HPE deploys ClearOS, a Linux-based open-source operations system partnered with ClearCenter, to redefine SMBs. Gateway and networking are part of Next Generation Small Business Server. The graphical web-based user interface lets users choose and pay for programs and support.
It runs on servers, network devices, and virtual machines as the host OS. One can download ClearOS as software, acquire ClearBox as hardware, or virtualize with ClearVM. HPE ProLiant ML110, ML30, and DL20 servers support it.
Its configurable, easy-to-use software platform increases corporate results and decreases expenses. HPE Intelligent Provisioning allows download and installation on all ProLiant servers 300 series and below.
It offers a variety of subscriptions for mobile, business, home, and distributed environments, as well as ClearOS solutions for education, non-profit, business, and government. ClearOS 5 and 6, and the latest ClearOS 7, have distinct documentation and support.
Why Do We Recommend It?
- Using a powerful firewall engine, ClearOS administrators may create and manage firewall rules to control network traffic.
- Network Address Translation in ClearOS converts private IP addresses to public IP addresses and vice versa.
- ClearOS’s VPN includes PPTP, OpenVPN, and IPsec.
- ClearOS supports open-source IDS/IPS like Snort and Suricata.
- ClearOS blocks dangerous websites and intercepts keystrokes.
- ClearOS supports QoS and bandwidth management.
- In addition to viruses and spam, ClearOS disables malicious websites and infiltration efforts.
- Due to its dynamic DNS and DHCP services, ClearOS simplifies network management.
- ClearOS has good logging and reporting.
| What is Good? | What Could Be Better? |
|---|---|
| 1. future updates and patches are provided at no additional cost. | 1. You cannot replicate Microsoft Small Business Server or Windows Server feature-for-feature. |
| 2. Markets apps and add-ons to extend functionality | 2. ClearOS might be resource-intensive on older hardware, affecting performance. |
| 3. Includes antivirus and web content filtering for internet security. |
10. OpenWRT
OpenWRT
Year: 2004
OpenWrt, a Linux-embedded operating system, includes an entirely writable filesystem and package management. Without application selection and configuration, the vendor uses packages to adapt the device to the application.
Building an app without firmware works better than stock firmware. This can make the router central for home automation and access more DDNS providers than vendor firmware via ddns-scripts. Wi-Fi is deactivated, and the default secure installation has no weak passwords or backdoors.
The developer and volunteer community communicates via OpenWrt Forum, OpenWrt Developer, and OpenWrt Admin mailing lists. It offers command-line (SSH) and web-based configuration, giving users complete control over their router/device.
Custom firmware images, such as pre-defined passwords, WiFi, etc., are created using the OpenWrt Image Generator. Packages localize WebUI in over 20 languages. As networking research evolves from experimental to practical, Open Wrt provides production-quality code.
The OpenWrt teams continuously develop fq_codel and cake algorithms to reduce buffer bloat, Wi-Fi stack queueing, and latency and provide service discovery for home networks with multiple routers and ISPs, prefix assignment, and zero conf IPv6/IPv4 routing.
OpenWrt 22.03.3, released on 9 January 2023, is accessible under the GPL without subscription or licensing.
Why Do We Recommend It?
- OpenWRT allows users complete control over the device by customizing the operating system.
- OpenWRT supports various embedded systems, wireless routers, and access points.
- OpenWRT provides IPv4 and IPv6 routing, NAT, DHCP, DNS, VLAN, firewalling, QoS, and VPN services.
- OpenWRT supports Wi-Fi, Bluetooth, and wireless mesh networking.
- OpenWRT’s LuCI web interface makes graphic device control and configuration easier.
- OpenWRT prioritizes security, supporting firewalling, port forwarding, NAT, and VPN.
- OpenWRT supports IPv6, the successor to IPv4.
| What is Good? | What Could Be Better? |
|---|---|
| 1. Not as user-friendly as other firmware | 1. Not as user-friendly as other firmware |
| 2. Software components are always updated. | 2. Getting the program running takes more time |
| 3. Configuration information is documented in plain-text files for easy editing and copying. |
Conclusion
After reading this article, you will better understand all the different Linux firewalls that can be implemented in your workplace and what kind of work they specialize in. Knowing this will help you choose which firewall is appropriate for your workplace.
Because data will flow so fast in the future, the use of firewalls to monitor and block malicious data is increasing daily.
To do all this, you must know what the different firewalls available in the market are, and I hope that through this article you have got that information and it will help you choose the right option for your requirement
Frequently Asked Questions
Which firewall is Best for Linux?
In my view, if you want to choose one firewall among all the top 10, then you must go with Vuurmuur as it is one of the lightest and most potent firewalls, with a feature-rich solution that will allow you to get a hold of your system and network completely.
You get all the functionalities without any cost as this firewall is free of cost and open source as well.
I am allowing you to customize it entirely according to your needs.
If you want something with a smaller scope, you must go with Smoothwall Express. It is very efficient and made for small businesses.
With ample community support, you can quickly work smoothly, even if stuck somewhere. The firewall also has deficient maintenance, which will help you save time and work power simultaneously.




