A sophisticated phishing campaign has emerged, targeting high-profile X (formerly Twitter) accounts to promote fraudulent cryptocurrency schemes.
The attack exploits the credibility of verified accounts, leveraging their reach to deceive users into visiting phishing sites.
The attackers employ a variety of phishing lures, including fake login alerts and copyright violation notices.

A typical email might claim, “We noticed a login to your account from a new device,” with a link redirecting victims to a malicious credential-stealing site.
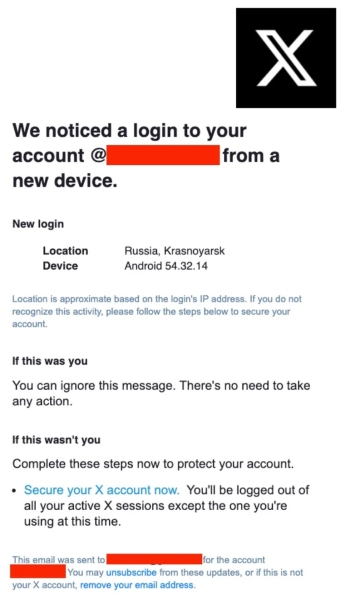
An X ‘new login’-themed phishing email (Source – SentinelOne)
In some cases, the attackers use Google’s AMP Cache domain (cdn.ampproject[.]org) to bypass email security filters and redirect users to phishing domains like x-recoverysupport[.]com.
Researchers at SentinelOne Labs detected that once victims enter their credentials, the attackers lock them out of their accounts and use the compromised profile to post fraudulent cryptocurrency opportunities.
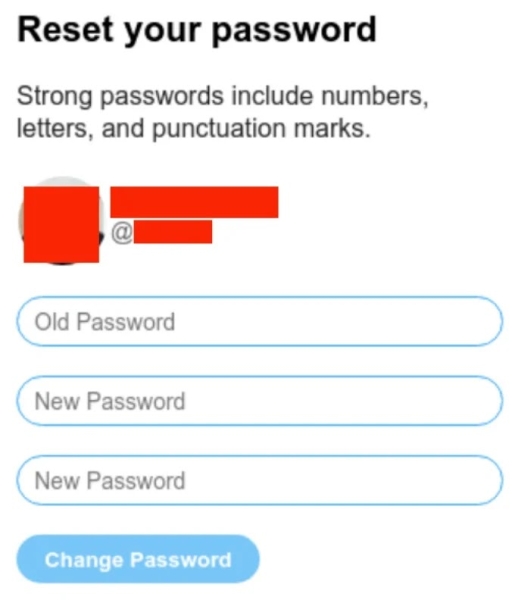
X credential phishing page (Source – SentinelOne)
These posts often include links to external phishing sites or wallet drainers.
Attack Details
Key domains associated with this campaign include:-
- securelogins-x[.]com
- x-recoveraccount[.]com
- buy-tanai[.]com
The infrastructure is linked to IP addresses hosted by a Belize-based VPS service and Turkish registrars, indicating a global operation.
Some phishing pages are built using FASTPANEL, a legitimate website management tool often abused by cybercriminals for its ease of deployment.
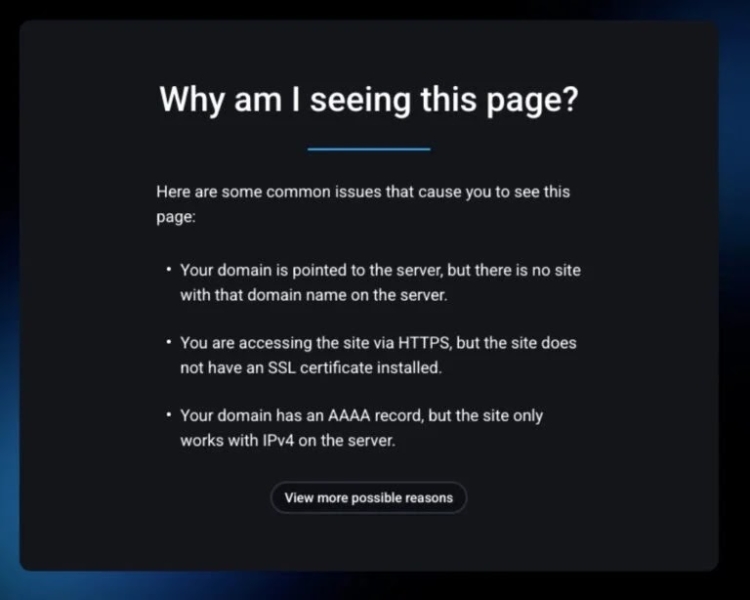
FASTPANEL landing page on buy-tanai[.]com (Source – SentinelOne)
Recent high-profile breaches include the compromise of Tor Project’s X account on January 30, 2025, which was used to promote fraudulent cryptocurrency schemes.
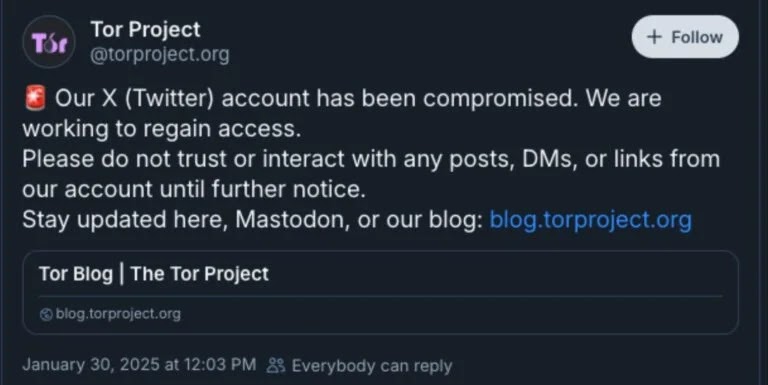
Tor Project account compromise notice (Source – SentinelOne)
Nasdaq’s X account, hacked on January 22, 2025, to endorse a fake memecoin named “STONKS” that briefly inflated its market cap to $80 million, and Microsoft India’s X account, hijacked in June 2024 to impersonate “Roaring Kitty” and lure users into connecting their wallets to malicious sites.
The attackers also exploit advanced methods like Man-in-the-Middle (MitM) attacks using tools such as Evilginx.
These techniques intercept authentication tokens during user logins, bypassing even robust two-factor authentication (2FA).
To safeguard against such attacks:-
- Use unique passwords and enable multi-factor authentication (preferably hardware-based like FIDO2).
- Avoid clicking on unsolicited links in emails or direct messages.
- Verify URLs before entering credentials; legitimate X URLs will always start with https://twitter.com.
Users are urged to remain vigilant and report suspicious activities promptly. Cybersecurity experts recommend continuous monitoring and adopting advanced authentication methods to mitigate risks.
Indicators of Compromise
- Domains:-
buy-tanai[.]com
dataoptimix[.]com
gamecodestudios[.]com
infringe-x[.]com
protection-x[.]com
rewards-dawn[.]com
securelogins-x[.]xyz
shortwayscooter[.]com
violationappeal-x[.]com
violationcenter-x[.]com
x-accountcenter[.]com
x-changealerts[.]com
x-logincheck[.]com
x-loginhelp[.]com
x-passwordrecovery[.]com
x-recoveraccount[.]com
x-suspiciouslogin[.]com
- IP Address: 84.38.130[.]20 (linked to phishing infrastructure)
- SHA-1 Hash: e2221e5c58a1a976e59fe1062c6db36d4951b81e (malicious PHP file)




