Security researchers at AhnLab Security Intelligence Center (ASEC) have uncovered a sophisticated malware campaign distributing the LummaC2 information stealer disguised as a cracked version of Total Commander, a popular file management tool for Windows.
The operation targets users seeking unauthorized access to the software’s premium features, exploiting their willingness to download illicit copies from unverified sources.
This attack shows the growing trend of malware actors weaponizing legitimate software tools to bypass user suspicion.
Total Commander, a dual-pane file manager supporting FTP, encryption, and advanced search functions, operates on a freemium model requiring a paid license after a 30-day trial.
Despite its official availability through ghisler[.]com, threat actors have created fake “cracked” versions embedded with malware.
ASEC’s investigation reveals that attackers mimic Total Commander’s interface and version history to appear authentic.
Total Commander (Source – ASEC)
Multi-Stage Social Engineering Attack Chain
The infection begins when users search for “Total Commander Crack” on search engines like Google. Results direct them to a Google Colab page posing as a download portal.
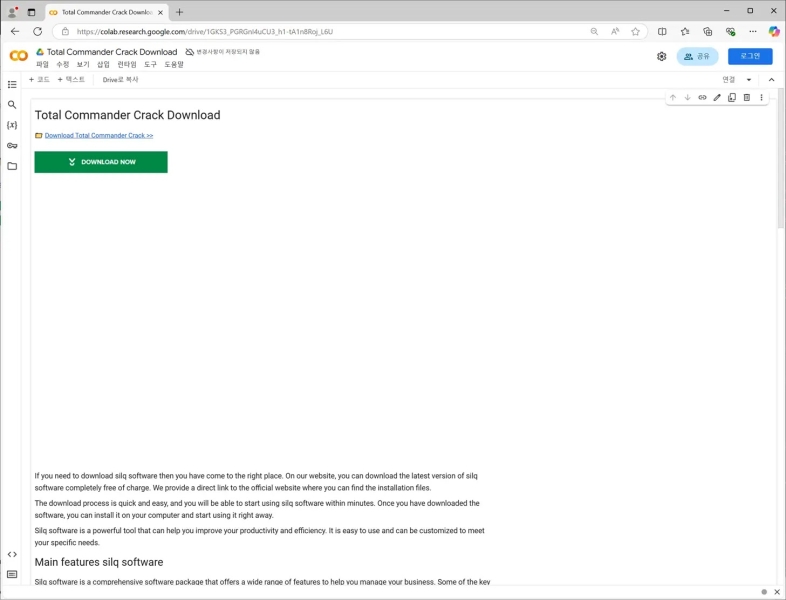
Fake Google Colab download page (Source – ASEC)
Victims must manually navigate through multiple redirections—including a fabricated Reddit thread to reach the final download link.
This deliberate, interactive process ensures only intentionally malicious downloads proceed, filtering out accidental clicks.
The downloaded file (installer_1.05_38.2.exe) uses a double-compressed RAR archive protected with a password (“Schools”) to evade detection.
Upon extraction, an NSIS installer script executes a heavily obfuscated batch file (Nv.cmd) that deploys the LummaC2 payload.
ExecShell open cmd “/c copy Nv Nv.cmd & Nv.cmd Set VO%Ingredients%%Oxford%%Restrict%t%Oxford%%Canadian%… tasklist | findstr // “opssvc wrsa” & if not errorlevel 1 ping -n 194 127.0.0.1
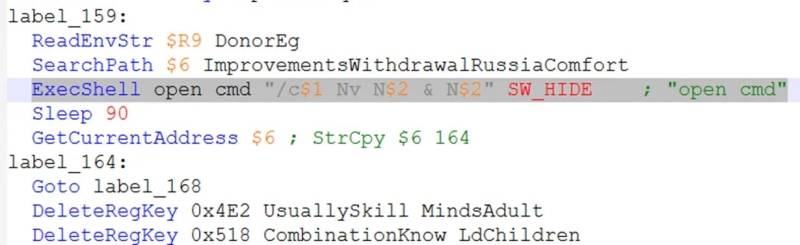
Obfuscated NSIS script deploying the batch file (Source – ASEC)
The batch script checks for security tools like Avast, Sophos, and Bitdefender processes. If none are detected, it decrypts and assembles LummaC2 components from fragmented binary blobs.
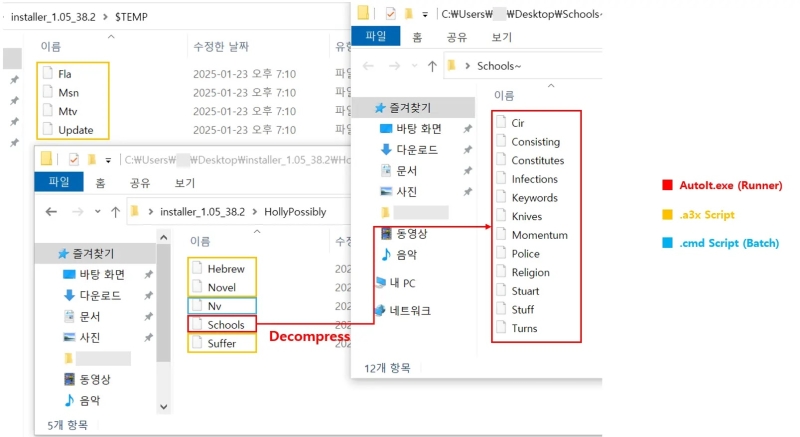
Obfuscated scripts and payload assembly (Source – ASEC)
The final payload, embedded within an AutoIt script (.a3x), uses layered encryption to hide its malicious code:
autoit $hpdevoce = $hpdevoce & “EFE8727F7890696E36E5B3BE49D788BA168FC004E3674768906DBB6528D48673AAD13A0A6B84619F2DC5F77526769B2…” Func ROULETTEGIVING($plannersdepressionperfumeseats) While 0xcl $mithateprotest = 0xcbaf Switch $mithateprotest …
Encrypted LummaC2 payload within the AutoIt script (Source – ASEC)
LummaC2 exfiltrates browser credentials, cryptocurrency wallets, and autofill data to attacker-controlled servers (affordtempyo[.]biz, hoursuhouy[.]biz).
Campaign MD5 hashes include 0a2d4bbb5237add913a2c6cf24c08688 and 25728e657a3386c5bed9ae133613d660.
This campaign exemplifies how threat actors exploit software piracy to deliver malware. Users are urged to avoid cracked software and download tools exclusively from official vendors.
Enterprises should monitor network traffic for connections to suspicious domains like those listed in the IoCs.
As LummaC2 continues evolving, combining behavioral analytics with endpoint detection remains critical to mitigating risks.




