A staggering 33.3 million attacks involving malware, adware, and unwanted mobile software were prevented throughout 2024.
This alarming figure translates to an average of 2.8 million attempted attacks per month, highlighting the persistent and evolving threat landscape facing mobile device users worldwide.
The research indicates that adware remains the most prevalent mobile threat, accounting for approximately 35% of all detected malicious activities.
The cybersecurity experts at Kaspersky documented the discovery of 1.1 million malicious and potentially unwanted installation packages during the year, with nearly 69,000 of these being associated specifically with mobile banking Trojans.
Despite a slight decrease in unique malware installation packages compared to previous years, the overall threat landscape appears to be plateauing rather than declining significantly, suggesting cybercriminals are refining their tactics rather than abandoning them.
Among the most concerning developments was the proliferation of modified messaging applications embedding the Triada Trojan family.

Fake mobile app (Source – Securelist)
Third-party WhatsApp mods containing Triada.ga ranked third in prevalence among all mobile threats detected.
Kaspersky Security Network notes that various other messaging app modifications harboring similar malicious code—including Triada.fd, Triada.gs, Triada.gn, and Triada.gm—also featured prominently in the year’s threat rankings.
The increasingly sophisticated Fakemoney family of scam applications demonstrated the highest activity levels in 2024. These malicious apps typically lure victims with fraudulent investment opportunities and false promises of payouts, exploiting users’ financial motivations.
Banking Trojans: A Growing Menace
The Mamont banking Trojan family emerged as a particularly significant threat in 2024, ranking fourth in the overall mobile threat landscape.
Cybersecurity researchers uncovered a new distribution scheme for this malware targeting Android users in Russia, where attackers enticed victims with discounted products.
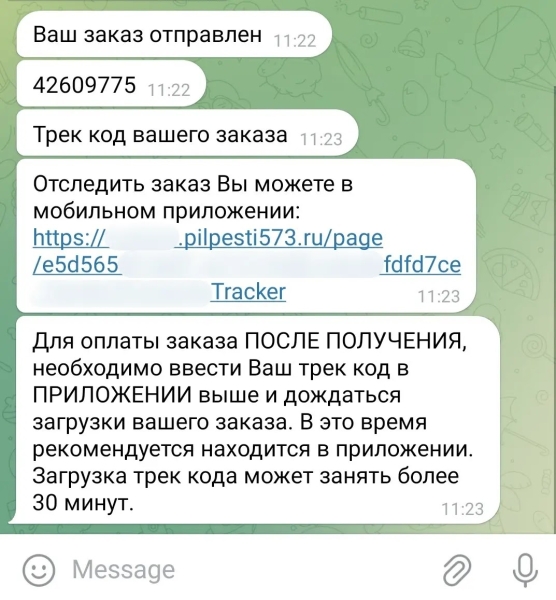
The phishing link (Source – Securelist)
After users initiated contact to place orders, they would later receive phishing links to download malware disguised as shipping tracking applications.
The malicious code uses a combination of social engineering and technical exploitation to gain access to banking credentials and financial accounts.
The technical implementation of these banking Trojans often involves permissions abuse, with the malware requesting SMS access privileges (android.permission.RECEIVE_SMS) to intercept authentication codes.
Similarly, they frequently request accessibility services access to monitor screen content and overlay fake login screens using the TYPE_APPLICATION_OVERLAY window type.
The report also shows the region-specific threats, with Turkey and India experiencing the highest concentration of banking malware.
Turkish users faced numerous variants of Piom Trojans associated with GodFather and BrowBot banker campaigns, while Indian users contended primarily with Rewardsteal bankers and SmsThief SMS-intercepting malware.
Cybersecurity experts recommend maintaining up-to-date security software, avoiding unofficial app sources, carefully reviewing requested permissions, and remaining vigilant about unsolicited messages containing links or download instructions to minimize exposure to these evolving mobile threats.




