Vulnerability scanning attacks targeting internet-connected devices have surged dramatically over the past year.
According to recent data compiled by F5 Labs in their February 2025 Sensor Intel Series report, scanning for vulnerabilities increased by a staggering 91% in 2024 compared to the previous year.
This unprecedented rise represents the largest year-over-year increase observed in recent history, dwarfing the mere 5% increase seen from 2022 to 2023.
The dramatic escalation isn’t isolated to a single vulnerability or attack vector.
While researchers at F5 Labs initially suspected that massive scanning for CVE-2023-1389 might be skewing the numbers, further analysis revealed that even when removing this specific threat, the overall traffic still showed a 91% increase.
The trend shows no signs of abating in early 2025 data, suggesting these elevated threat levels may represent a new normal for internet-connected devices.
Most concerning for home users and businesses alike is the concentration of attacks targeting IoT devices and consumer-grade routers.
The report indicates that a full 42% of all identified CVE-related traffic specifically targeted these devices. The TP-Link Archer AX21 router vulnerability (CVE-2023-1389) continues to dominate scanning activity for the sixth consecutive month.
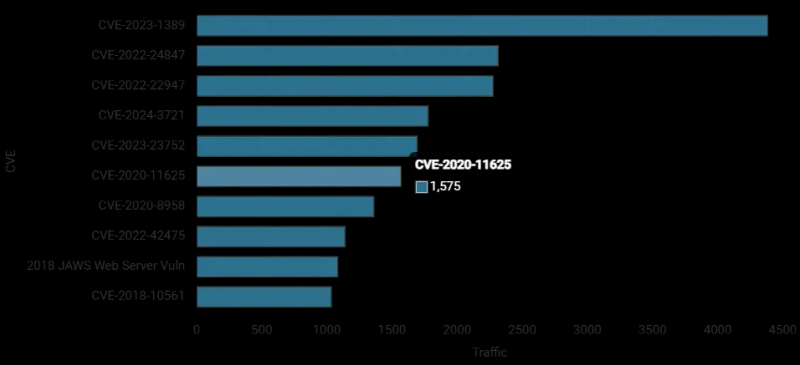
Top ten vulnerabilities by traffic volume in January 2025 (Source – F5 Labs)
The data reveals that command injection vulnerabilities in consumer devices remain particularly attractive to attackers.
For instance, CVE-2024-3721, a command injection vulnerability affecting TBK DVR models, surged by two orders of magnitude in January 2025, climbing to fourth place among targeted vulnerabilities.
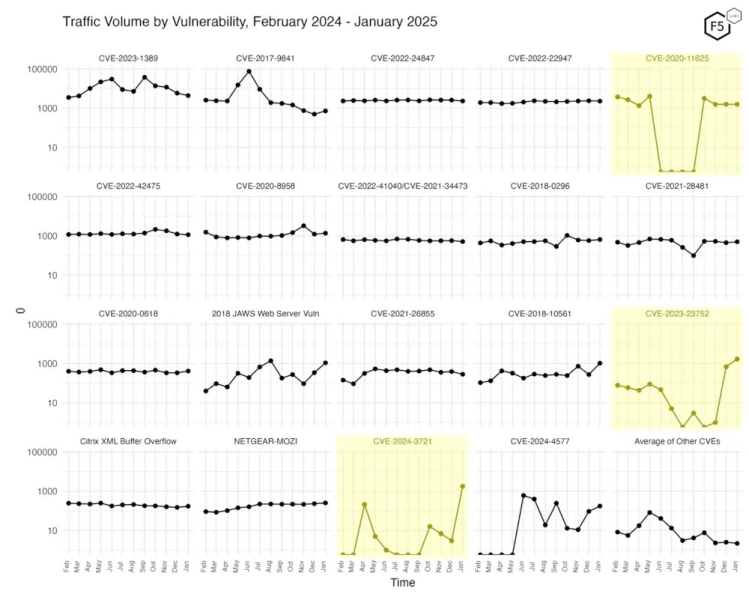
Traffic volume by vulnerability (Source – F5 Labs)
This dramatic spike suggests that attackers are rapidly shifting resources toward newly discovered vulnerabilities in these devices.
Infrastructure Behind the Attacks
Contrary to what might be expected, the vast majority of scanning doesn’t originate from botnets comprised of compromised consumer devices. Analysis of the “top talkers” by autonomous system number (ASN) revealed that 75% of all traffic originated from just 20 ASNs, with most being hosting providers.
The top contributor, Lithuania-based UAB Host Baltic, accounted for nearly 20% of all observed traffic from just 62 distinct IP addresses.
This pattern of scanning predominantly from hosting providers rather than residential networks indicates that attackers are leveraging commercial infrastructure for their campaigns, likely due to the greater bandwidth and stability these services provide.
The report notes that some hosting providers have begun taking action against these activities, but significant work remains to curtail the growing tide of vulnerability scanning threatening internet-connected devices worldwide.




