A newly disclosed edge case in Substack’s custom domain implementation allows threat actors to hijack inactive subdomains, potentially enabling content spoofing, phishing campaigns, and brand impersonation.
The researcher identified 1,426 vulnerable domains – representing 8% of all Substack-associated custom domains – that remain exposed due to misconfigured DNS records, including 11 wildcard domains that exponentially increase attack surfaces.
While Substack’s $50 custom domain activation fee provides partial deterrence, the platform’s lack of domain ownership verification creates systemic risk for organizations using its publishing services.
Substack’s Domain Architecture
Substack employs Cloudflare for SaaS to manage custom domains through CNAME record redirection.
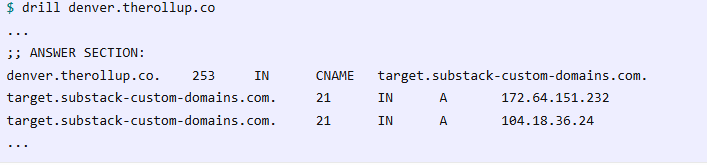
Users configure their DNS to point blog.example.com to target.substack-custom-domains.com, which routes traffic through Cloudflare’s Anycast network to Substack’s origin servers.
The platform then maps incoming domain requests to corresponding blogs using reverse proxy logic. The vulnerability manifests when users decommission Substack blogs without removing associated DNS records.
A residual CNAME entry creates an exploitable condition where any attacker can claim the orphaned domain by:
- Paying the $50 activation fee
- Adding the vulnerable domain to their Substack account
- Serving malicious content through what appears to be a legitimate domain
Taking over a subdomain
Wildcard Domains Amplify Risk
The threat escalates when organizations configure wildcard CNAME records (*.example.com), making every subdomain under the parent domain vulnerable.
Security Researcher Joren Vrancken’s analysis revealed 11 such wildcard configurations, theoretically exposing thousands of subdomains to abuse.
Attackers could spin up fraudulent subdomains like support.example.com or login.example.com to execute sophisticated phishing operations.
Cloudflare’s error handling inadvertently aids attackers – domains not actively routed through Substack return either:
- Error 1001: DNS resolution failure for non-Cloudflare domains
- Error 1014: Host header mismatch for Cloudflare-managed domains
These generic messages prevent legitimate owners from detecting misconfigurations while providing no barrier to malicious registration.
While Substack isn’t directly responsible for third-party DNS management, its authentication gap violates OWASP’s Domain Takeover Prevention guidelines.
Cloudflare for SaaS supports domain validation through TXT records or API-triggered challenges – mechanisms Substack has yet to implement.
Recommended mitigations include:
- For Users: Audit DNS records via tools like SecurityTrails; remove unused CNAMEs
- For Organizations: Implement DNSSEC to prevent unauthorized record modifications
- For Substack: Adopt domain validation per Cloudflare’s SaaS best practices
The $50 fee creates asymmetric defense, which is prohibitive for casual attackers but negligible for advanced persistent threats (APTs).
As noted in EdOverflow’s can-i-take-over-xyz repository, similar vulnerabilities affect 38+ SaaS platforms, underscoring systemic issues in cloud-era DNS management.
As cloud services increasingly abstract infrastructure management, this incident highlights the critical need for automated DNS hygiene tools and provider-enforced security controls.




