In cybersecurity, a honeypot is a bait system specifically designed to attract and analyze cyber-attacks, functioning as a trap for potential intruders.
By mimicking legitimate targets, honeypots divert threat actors from real assets while gathering intelligence on their methods and behaviors.
Cybersecurity analysts Hakan T. Otal and M. Abdullah Canbaz from the Department of Information Science and Technology College of Emergency Preparedness, Homeland Security, and Cybersecurity University at Albany recently developed an AI honeypot to engage with sophisticated threat actors.
AI Honeypot & Attackers
Honeypots range from low-interaction honeypots, which simulate basic network services, to high-interaction honeypots that mimic entire network infrastructures.
Here below we have mentioned all the major types of them:-
- Server honeypots (Expose network services)
- Client honeypots (Designed to be attacked by malicious servers)
- Malware honeypots (Capture and analyze malicious software)
- Database honeypots (Protect sensitive data repositories)
Though they are effective, the traditional honeypots face limitations such as vulnerability to honeypot fingerprinting and limited engagement capabilities.
To create more sophisticated honeypots the LLMs like “Llama3,” “Phi 3,” “CodeLlama,” and “Codestral” were actively integrated through recent advancements.
However, to enhance the performance while reducing the computational load all these LLM-based honeypots primarily employ techniques like “Supervised Fine-Tuning (SFT),” “prompt engineering,” “Low-Rank Adaptation (LoRA),” and “Quantized Low -Rank Adapters (QLoRA).”
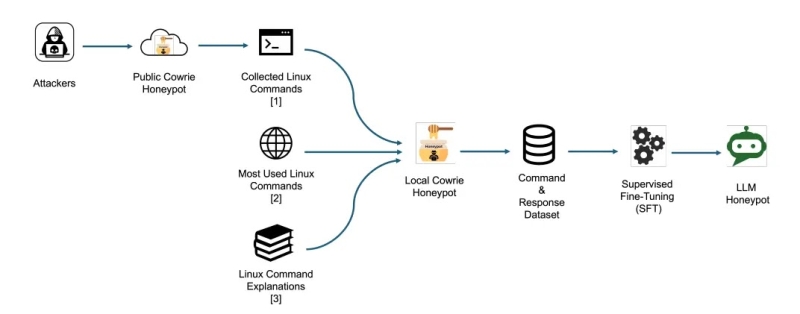
Data Collection & Model Training Pipeline (Source – Arxiv)
They also utilize NEFTune noise for regularization and Flash Attention 2 for efficient processing of long sequences.
Typically deployed on cloud platforms like AWS, Google Cloud, and Azure, while besides this, all these honeypots were combined with custom SSH servers using libraries like Paramiko, reads the research.
The LLM processes attacker commands at the IP (Layer 3) level which helps in generating contextually appropriate responses that mimic the behavior of the real system.
Evaluation metrics include ‘cosine similarity,’ ‘Jaro-Winkler similarity,’ and ‘Levenshtein distance’ to assess the model’s output against expected responses.
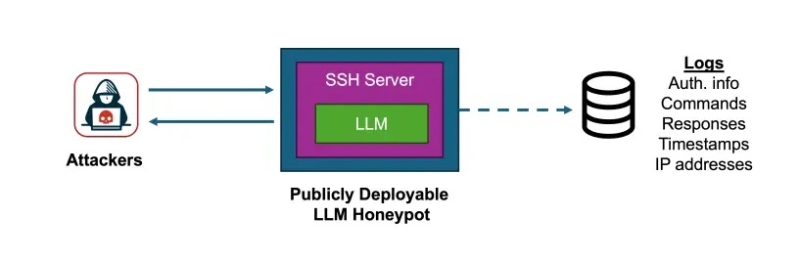
Interactive LLM-Honeypot Server Framework (Source – Arxiv)
This approach significantly enhances the ability of the honeypot which enables it to engage attackers convincingly, improves threat detection, and also allows intelligence gathering.
But, here the challenges remain in balancing computational efficiency, detection avoidance by sophisticated threat actors, and maintaining realistic behavior.
For fine-tuning these models, Frameworks like LlamaFactory are used, which can be made publicly accessible via platforms like Hugging Face.
The integration of LLMs in honeypot technology represents a significant advancement in cybersecurity that offers more dynamic and adaptive defenses against evolving cyber threats.




