Researchers from LevelBlue Labs have uncovered a new tactic threat actors employ to hijack legitimate anti-virus software for malicious purposes.
This sophisticated attack leverages a tool named SbaProxy, which masquerades as a legitimate anti-virus component to establish proxy connections through a command and control (C&C) server.
SbaProxy is a new tool in the threat actor’s evolving toolkit, capable of establishing proxy connections that can be used to generate revenue.
The tool is distributed in various formats, including DLLs, EXEs, and PowerShell scripts, making it challenging to detect due to its legitimate appearance and sophisticated design.
Threat actors are modifying legitimate anti-virus binaries to serve malicious purposes while maintaining their appearance as benign software.
This makes detection difficult, as the malicious binaries are signed with valid or seemingly valid certificates, bypassing security checks. The targeted anti-virus products include Malwarebytes, BitDefender, and APEX products, among others.
The malicious binaries are signed with valid or seemingly valid certificates, which helps them evade detection. For example, a certificate with the thumbprint “DCB42EF087633803CD17C0CD6C491D522B8A2A” issued to “STERLING LIMITED” is currently valid and used to sign some of the samples in this campaign. The threat actor likely acquired this certificate to perform their activities, as the date it was issued fits the campaign timeline.
Technical Analysis
LevelBlue Labs observed suspicious activity originating from seemingly legitimate anti-virus binaries in early June. Upon investigation, this activity was linked to a new tool associated with a campaign already reported by Sophos in late April. This marks a new iteration in the toolset used by this threat actor.
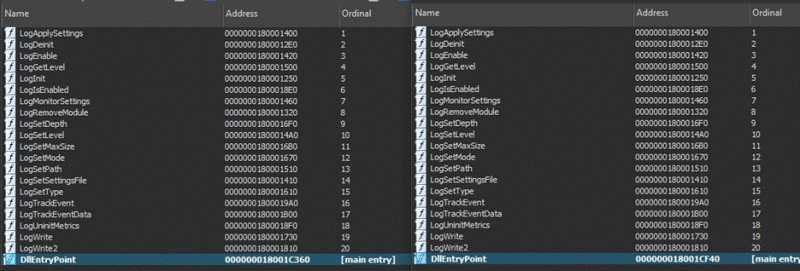
Comparison of exported functions between legitimate and malicious samples (Source AT&T)
A sample masquerading as a BitDefender logging DLL was analyzed. The exported functions in the malicious DLL were identical to those in the original DLL, except for one modified function, ‘LogSetMode’. This function was replaced with a jmp instruction to another address, which decrypts and executes a bundled XOR-encrypted shellcode.
The payload decryption function includes a pointless loop that sets several local variables to a hardcoded value, repeated 448,840 times. This is a rudimentary form of bypassing detection methods that rely on emulation.
After completing the loop, the code checks one of the set variable’s values and crashes if it’s not what was expected. The code then allocates memory for the payload, decrypts it using a hardcoded multi-byte XOR key, and executes it.
The initial communication with the C&C server involves a series of calls to the ‘send’ function with all zero content and lengths of 16, 4, and 0 bytes, respectively.
This is likely a magic sequence to ensure the C&C only replies to the malicious client. After performing this set of sends, it receives 16 bytes from the C&C and sends them back to the server over a new socket. This new set of connections is performed in an iterative loop, allowing for several active connections in parallel.
These attackers hijack legitimate anti-virus software to evade detection, using valid certificates and crafting malicious binaries that mimic legitimate ones, complicating threat detection. As cybercriminals innovate, organizations must stay vigilant and proactive in their defenses.
LevelBlue Labs has developed detection methods to identify and combat this threat. These include SURICATA IDS signatures that alert on specific patterns of communication with the C&C server. The associated indicators of compromise (IOCs) are available in the OTX Pulse.




