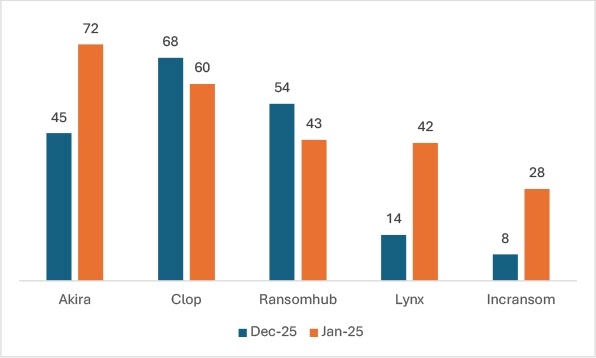
January 2025 marked a significant month in the ransomware landscape, with Akira emerging as the leading threat.
According to recent reports, Akira was responsible for 72 attacks globally, highlighting its rapid rise in prominence.
This surge in activity is part of a broader trend where ransomware groups are becoming increasingly sophisticated in their tactics and targets.

Ransomware Trends Graph (Source – Cyfirma)
In January, Akira emerged as the most active ransomware group, with a 60% increase in activity due to its effective use of Python-based malware and exploitation of critical infrastructure vulnerabilities.
Meanwhile, new ransomware groups like MORPHEUS and Gd Lockersec have entered the scene, with MORPHEUS claiming three victims since December 2024 and Gd Lockersec targeting five by the end of January.
MORPHEUS Onion Site (Source – Cyfirma)
MORPHEUS and HellCat share a codebase, deploying 64-bit executable payloads that exclude certain system files from encryption, while Gd Lockersec focuses on financial gains and avoids attacking entities in specific countries and non-profit hospitals.
Gd Lockersec Onion Site (Source – Cyfirma)
The Manufacturing sector remained the primary target, with 75 reported incidents, while the IT sector saw a 60% increase due to its critical data and supply chain access.
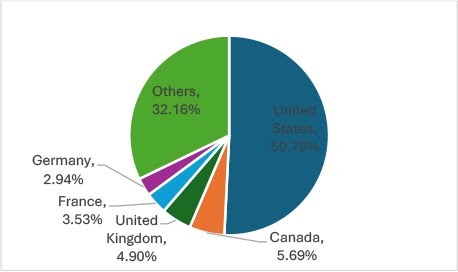
While besides this, the security researchers at Cyfirma noted that geographically, the United States was the most targeted region, with 259 incidents, followed by Canada, the UK, France, and Germany—nations frequently targeted for their strong economies and data-rich enterprises.
Top Locations Targeted (Source – Cyfirma)
Akira Attack Chain
- Python-Based Malware: Ransomware groups are increasingly using Python-based backdoors for network infiltration.
These backdoors establish SOCKS5 tunnels, facilitating lateral movement and ransomware deployment while evading detection.
# Example of Python-based backdoor code import socket import socks # Establishing a SOCKS5 connection socks.setdefaultproxy(socks.PROXY_TYPE_SOCKS5, ‘127.0.0.1’, 9050) socks.wrapmodule(socket) # Creating a reverse proxy for communication def create_reverse_proxy(): # Code to handle reverse proxy logic pass
- VMware ESXi Exploitation: Threat actors are targeting VMware ESXi hypervisors using SSH tunnels to establish persistence and deploy ransomware. This approach exploits the critical role of ESXi in virtualized infrastructures.
# Example of SSH tunneling command ssh -L 8080:localhost:8080 user@esxi-host
The ransomware landscape in January 2025 was marked by increased sophistication and targeted attacks.
With such rapid evolution it is crucial for organizations to enhance their cybersecurity measures.
This includes monitoring for Python-based malware, securing VMware ESXi systems, and implementing robust access controls.




