A sophisticated cyberespionage campaign leveraging the FatalRAT remote access trojan (RAT) is targeting industrial organizations across the Asia-Pacific (APAC) region, according to a Kaspersky ICS CERT report.
The attackers, suspected to be Chinese-speaking threat actors, employ a multi-stage infection chain exploiting legitimate Chinese cloud services like Youdao Cloud Notes and Tencent Cloud (myqcloud) to deliver payloads while evading detection.
The campaign primarily targets manufacturing, energy, IT, and logistics sectors in Taiwan, China, Japan, Thailand, and Singapore.
Attackers distribute phishing emails and messages via WeChat/Telegram, masquerading as tax documents or invoices (“税务总局关于补贴有关税收的公告.zip” [State Taxation Administration Announcement on Subsidies.zip]).
Cybersecurity experts at Kaspersky ICS CERT noted that these ZIP archives contain first-stage loaders packed with AsProtect or UPX, which initiate a complex, seven-step infection process.
FatalRAT’s Multi-Stage Evasion Framework
The malware’s infection chain begins with a loader retrieving dynamically updated C2 configurations from Youdao Cloud Notes via HTTP requests to URLs like http://note.youdao[.]com/yws/api/note/4b2eead06fc72ee2763ef1f653cdc4ae.
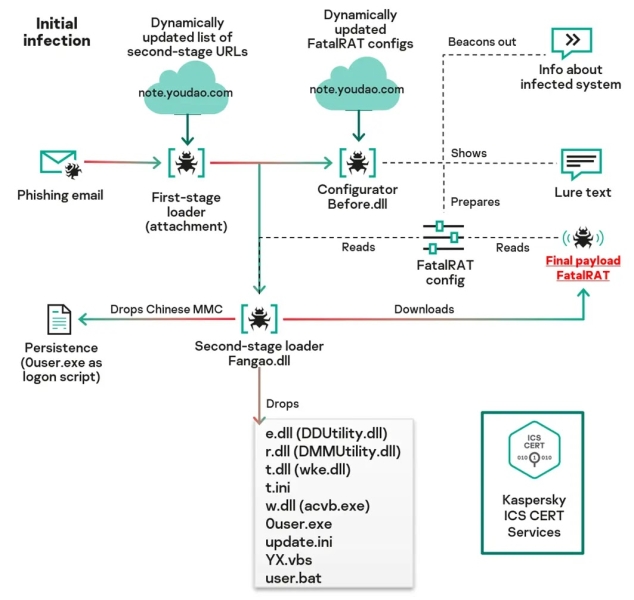
Infection chain (Source – Kaspersky ICS CERT)
The JSON response includes encrypted links to secondary modules like Before.dll (configurator) and Fangao.dll (second-stage loader), which decrypt using XOR keys (0x58).
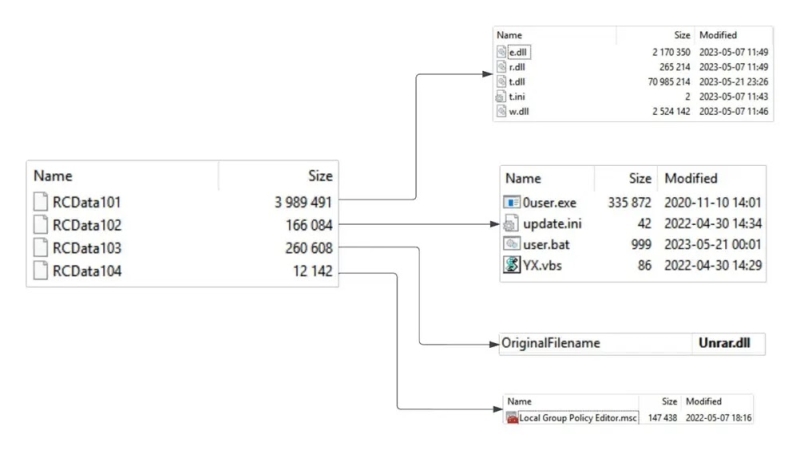
Fangao.dll resource unpacking scheme (Source – Kaspersky ICS CERT) // Sample decryption routine in Before.dll (PDB: K:C++梵高远程管理客户端二号ReleaseBEFORE.pdb) for (int i = 0; i < data_length; i++) { decrypted_data[i] = encrypted_data[i] ^ 0x58; }
Fangao.dll deploys PureCodec and DriverAssistant legitimate software for DLL sideloading, injecting malicious libraries like wke.dll into memory.
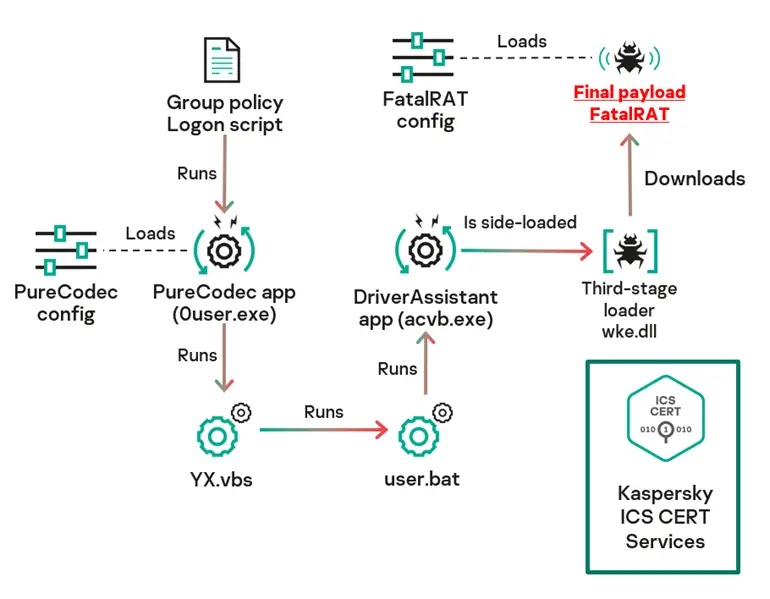
FatalRAT launch sequence (Source – Kaspersky ICS CERT)
The final payload, FatalRAT (MD5: bcec6b78adb3cf966fab9025dacb0f05), performs 17 anti-VM checks, including registry scans for VMware artifacts and verification of Chinese locale settings.
# FatalRAT anti-analysis check (registry key) Get-ItemProperty -Path “HKLM:SYSTEMControlSet001ServicesdiskEnum�” | Select-Object -Property “ClassGUID”
The RAT logs keystrokes to C:WindowsFatal.key, exfiltrates data via encrypted C2 channels (1.12.37[.]113:8081), and enables remote execution of destructive commands like MBR corruption.
Kaspersky’s telemetry revealed compromised engineering workstations, highlighting risks to operational technology (OT) environments.
Kaspersky recommends segmenting networks, monitoring DLL sideloading (wke.dll), and blocking IoCs like the C2 domain fakaka16[.]top.




