Cybersecurity researchers have uncovered a sophisticated malware campaign exploiting tax season to target financial organizations and individuals globally.
The campaign involves phishing emails impersonating tax agencies and financial institutions, delivering malware and harvesting sensitive credentials.
The malicious actors behind this campaign are leveraging tax-related themes, such as account updates, overdue payments, or tax refunds, to lure victims.

Emails often appear to come from legitimate entities like HM Revenue & Customs (HMRC) in the UK, Intuit in the US, or myGov in Australia.
Security analysts at ProofPoint noted that all these emails include links to phishing websites or attachments containing malware.
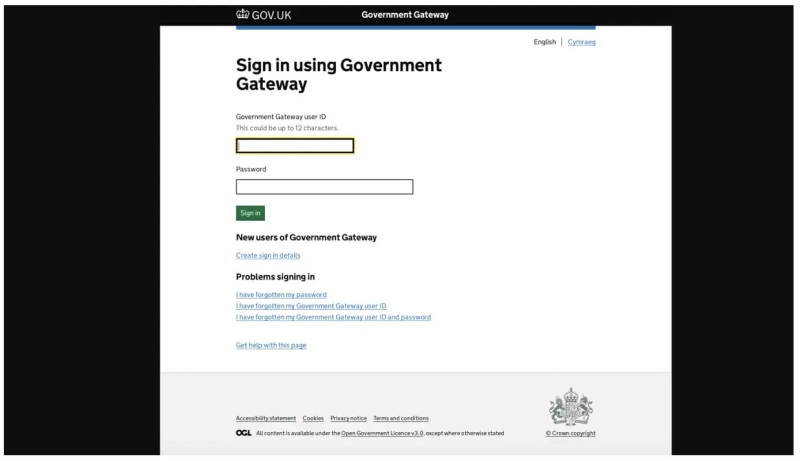
Fake HMRC login page used for credential harvesting (Source – ProofPoint)
For instance, some phishing emails claim that recipients’ business tax accounts need urgent updates and direct them to fake HMRC login pages designed to steal credentials.
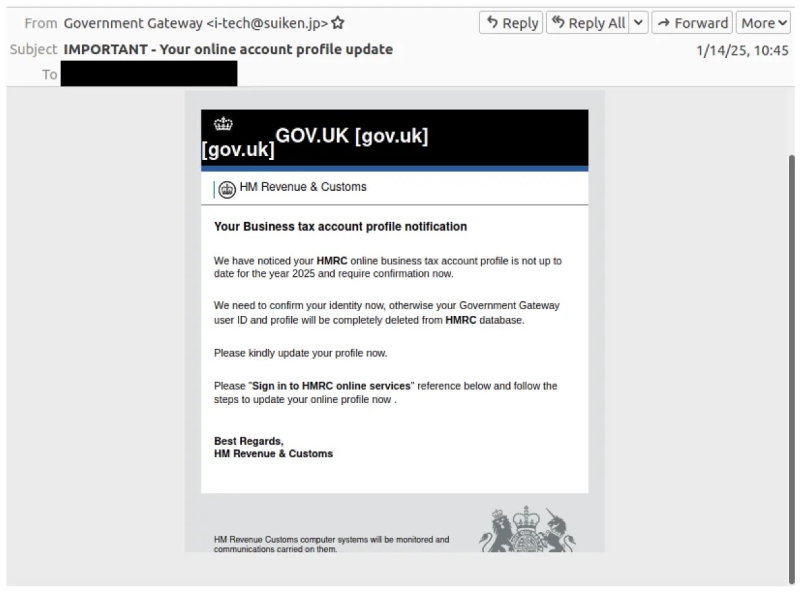
HMRC lure impersonating the agency and distributing credential phishing (Source – ProofPoint)
Other emails impersonate Intuit by notifying users of rejected tax forms and leading them to credential-harvesting websites with suspicious URLs.
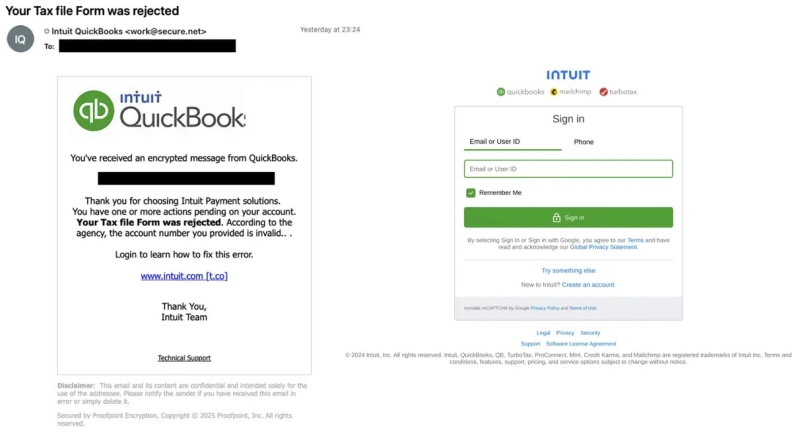
Email impersonating Intuit (left), credential phishing landing page (right) (Source – ProofPoint)
Additionally, messages mimicking the Australian Taxation Office impersonate myGov, urging users to resolve pending tax issues via phishing sites.
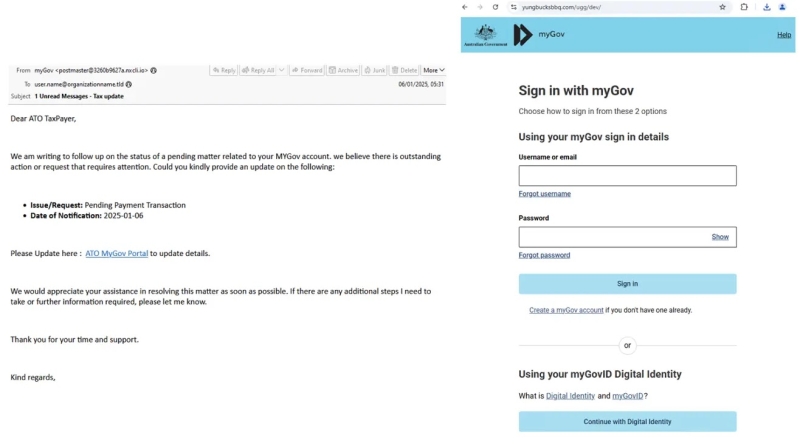
Phishing email impersonating myGov (left), phishing landing page (right) (Source – ProofPoint)
Malware Payloads
Beyond phishing, the campaign delivers advanced malware payloads. Notable examples include:-
Rhadamanthys Malware: Distributed via fake tax software emails containing malicious JavaScript files hosted on Microsoft Azure. The script executes PowerShell commands to download and install Rhadamanthys.
Example URL:
hxxps://drakesoftware[.]blob[.]core[.]windows[.]net/drakesoftware/Invoice%2352223.html
Voldemort Malware: A backdoor that uses Google Sheets for command-and-control communication. It disguises itself as a PDF file linked in phishing emails from fake tax agencies.
Attack chain: Phishing email → Fake PDF → Python script execution → DLL download → System compromise.
This campaign has affected thousands of organizations across multiple countries. In the UK, HMRC-themed phishing attacks targeted businesses with credential-stealing websites.
In the US, over 40,000 Intuit-themed phishing emails were sent in January 2025 alone.
Meanwhile, in Switzerland, fraud campaigns impersonated federal tax authorities, requesting bogus payments to adversary-controlled Revolut accounts.
Tax-themed cyberattacks are particularly effective due to their timing and perceived urgency. Recipients are often compelled to act quickly on such communications, making them vulnerable to scams.
Financial organizations are prime targets because of their critical role in processing sensitive data and transactions.
To mitigate these threats, organizations should educate employees about recognizing phishing attempts, implement multi-factor authentication for all accounts, and deploy advanced email filtering systems to detect malicious attachments and links.
Additionally, regularly updating antivirus software and monitoring for indicators of compromise (IoCs) are crucial steps to ensure robust security.
Organizations must strengthen defenses against evolving threats like this campaign that exploits trust in authoritative entities to deliver destructive malware payloads.
Indicators of Compromise (IOCs)
Security teams should monitor for these IOCs:-
| Indicator | Description | First Seen |
|---|---|---|
| hxxps://clearlivate[.]com/xxx/rest.html | Phishing URL | January 16, 2025 |
| hxxps://drakesoftware[.]blob[.]core.windows.net/… | Malware-hosting URL | January 16, 2025 |
| hxxps://revolut[.]me/swisstaxadm | Fraudulent payment URL | December 18, 2024 |




