Cybersecurity firm Mandiant has uncovered a novel method to bypass browser isolation technologies, a widely used security measure designed to protect users from web-based attacks such as phishing and malware.
This new way to get around security measures uses machine-readable QR codes to set up command-and-control (C2) communication. This shows where browser isolation systems used by businesses around the world might be weak.
Browser isolation is a security technique that separates web browsing activity from users’ local devices by operating the browser in a secure environment such as the cloud or virtual machines.
This method ensures that any malicious web-based activity remains contained within the isolated environment and streams only the visual content back to the user’s local browser. Organizations commonly deploy one of three types of browser isolation:
- Remote Browser Isolation (RBI): Sandboxes browser activities in a cloud-based environment.
- On-Premises Browser Isolation: Hosts sandboxed browsers within the organization’s infrastructure.
- Local Browser Isolation: Runs the browser in a containerized local environment (e.g., Docker, Windows Sandbox).
Attackers commonly use this technology to stop them from exploiting browser vulnerabilities, launching phishing attacks, or creating C2 links between their infrastructure and compromised devices.
C2 Through QR Codes
Mandiant’s research has demonstrated that even the most advanced browser isolation systems can be circumvented. Attackers can get around standard HTTP-based C2 methods that don’t work in browser isolation environments because of pixel streaming by putting command data into QR codes. Here’s how the QR code-based C2 method works:
- Planting the Malicious Implant: A compromised device uses a headless browser (e.g., Puppeteer with Google Chrome) controlled via the DevTools protocol.
- Requesting the Web Page: The implant retrieves a webpage from the attacker-controlled server through the headless browser, relayed via the isolated browser.
- Encoding via QR Code: The attacker’s server responds with an HTML page containing the command data embedded in a QR code.
- Rendering and Scanning: The remote browser streams the webpage back to the local machine. The malicious implant captures a screenshot of the QR code displayed and decodes the command using an embedded QR scanning library.
- Executing Commands: The implant executes the command and sends the output back to the attacker, using URL parameters as part of the process.
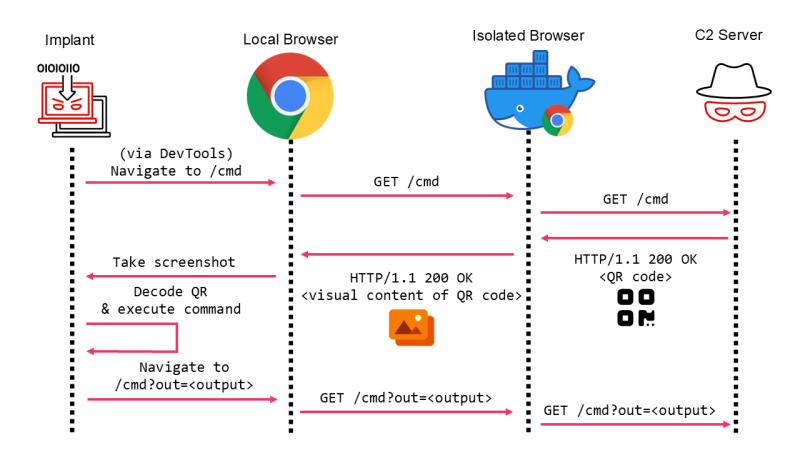
Sequence diagram of C2 via QR codes
This method allows attackers to exploit the visual content streamed by the isolation system, completely bypassing standard security mechanisms.
To demonstrate its findings, Mandiant developed a proof-of-concept (PoC) implant using Chrome in headless mode. The approach was further integrated with Cobalt Strike’s BEACON implant to show how QR codes can facilitate viable C2 operations. However, the researchers noted limitations:
- QR codes could only reliably transfer up to 2,189 bytes due to quality constraints in the pixel stream.
- Each request took approximately five seconds, introducing latency and making high-throughput operations like SOCKS proxying impractical.
Even with these limitations, Mandiant’s Proof of Concept shows a major flaw: attackers could send low-bandwidth C2 data using QR codes in all three types of browser isolation.
This findings spotlight the evolving sophistication of attacker tactics in defeating cybersecurity defenses. While browser isolation remains a powerful protection measure against web-based threats, this research underscores that no single defense is foolproof.
Recommendations for Organizations
To mitigate risks associated with this new C2 technique, Researchers provides the following recommendations:
- Inspect network traffic for anomalous patterns, as browser isolation generates numerous HTTP requests that may indicate unusual activity.
- Track process creation for automation flags (e.g., –enable-automation) to identify headless or automated browser usage.
- Strengthen defenses with advanced threat detection systems and regular adversarial emulation exercises to complement browser isolation.




