Security researchers have uncovered an ongoing malicious campaign targeting the Go ecosystem with seven typosquatted packages designed to install hidden loader malware on Linux and macOS systems.
The threat actor has published packages that impersonate widely used Go libraries, employing sophisticated obfuscation techniques to evade detection while silently executing malicious payloads in the background.
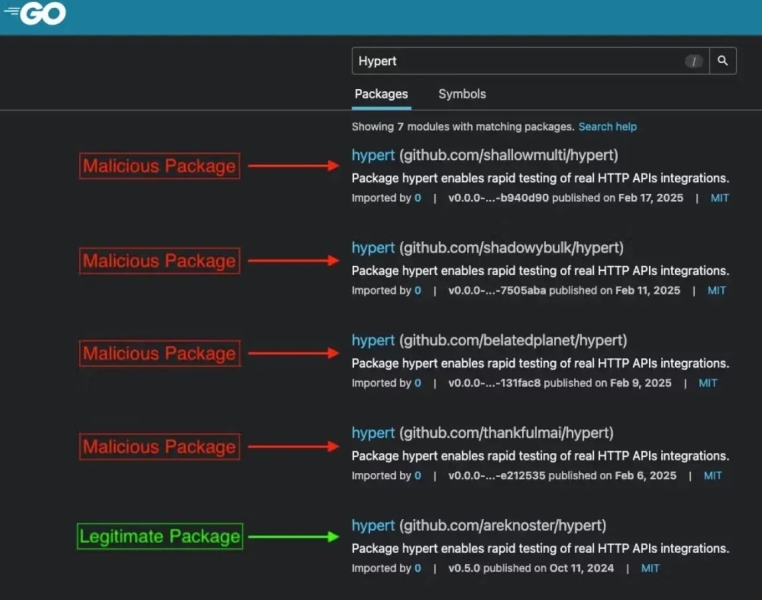
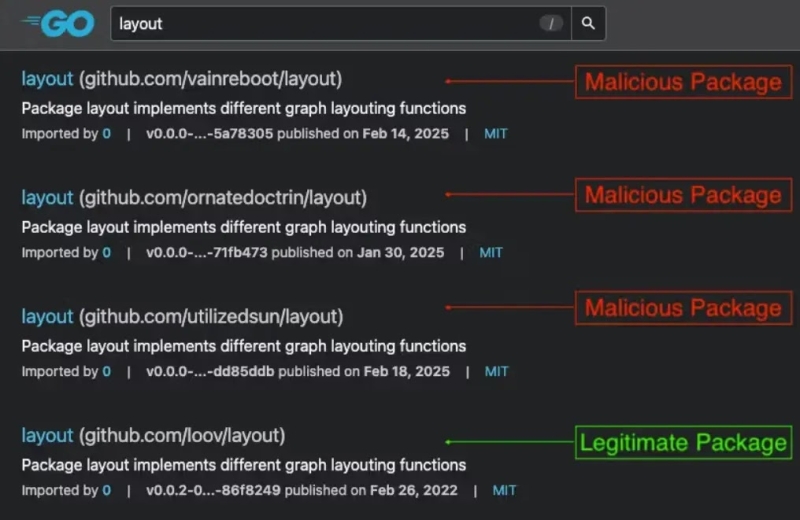
The campaign specifically targets developers using UNIX-like environments, with four packages impersonating the legitimate github.com/areknoster/hypert library and three others mimicking the github.com/loov/layout library.
Most concerning is one variant (github.com/shallowmulti/hypert) that appears to specifically target financial-sector developers through domain names resembling legitimate financial institutions.
Typosquatted clones (Source – Socket.dev)
Socket researchers identified the malicious packages: shallowmulti/hypert, shadowybulk/hypert, belatedplanet/hypert, thankfulmai/hypert, vainreboot/layout, ornatedoctrin/layout, and utilizedsun/layout.
Malicious layout packages (Source – Socket.dev)
These packages share consistent obfuscation techniques and filenames, suggesting a coordinated effort by a single threat actor with an infrastructure designed for persistence.
When imported into a developer’s project, these packages execute concealed functions that download and run remote scripts from domains like alturastreet[.]icu, host3ar[.]com, binghost7[.]com, and sharegolem[.]com.
The malicious domain alturastreet[.]icu bears a superficial resemblance to alturacu.com, the legitimate online banking portal for Altura Credit Union, indicating possible targeting of financial institutions.
The packages contain obfuscated functions similar to this deobfuscated example:-
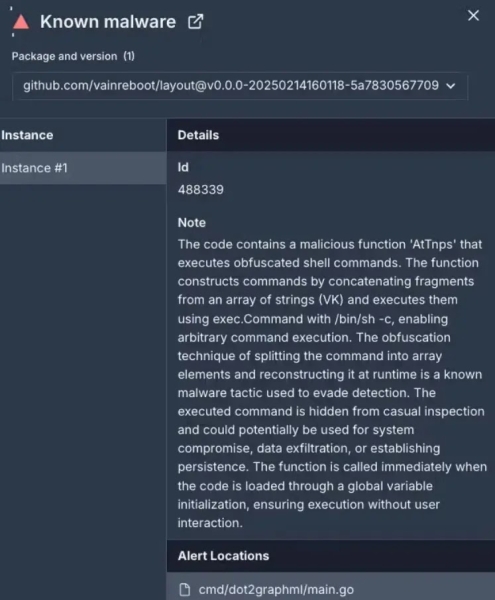
func qcJjJne() error { qAYW := []string{ “d”, “0”, “n”, “t”, “|”, /* many more characters */ } QJqmcouO := “/bin/sh” Tsfs := “-c” fFadxxb := qAYW[29] + qAYW[15] + /* more concatenation */ exec.Command(QJqmcouO, Tsfs, fFadxxb).Start() return nil }
The script ultimately executed downloads an ELF file named f0eee999 and installs it after a deliberate one-hour delay to evade detection.
The ELF file shows minimal initial malicious behavior, suggesting it may be a cryptominer or dormant loader awaiting activation.
Socket AI Scanner analysis (Source – Socket.dev)
Developers are urged to implement real-time scanning tools, conduct code audits, and verify package integrity before installation.
Security researchers recommend using tools like Socket’s GitHub app, CLI, or web extension to automatically detect and block typosquatted or malicious packages.
The threat actor’s demonstrated ability to rapidly pivot suggests this campaign may continue evolving with new typosquatted packages targeting the Go ecosystem.




