A new report published recently, details how red team operators can use SpecterInsight 4.2.0 to successfully bypass Windows Defender and other antivirus solutions.
The technique allows threat actors to evade detection while loading malicious .NET payloads into memory, presenting significant challenges for security teams.
Security researcher Pracsec demonstrated that despite Microsoft’s extensive efforts to improve heuristic signatures and detect AMSI bypass techniques, including the detection of code manipulation within AMSI.dll, certain methodologies still allow attackers to evade these protections.
The recent advancements in Windows Defender have made it increasingly difficult to craft undetectable payloads, but the report shows that carefully constructed attack chains can still be successful.
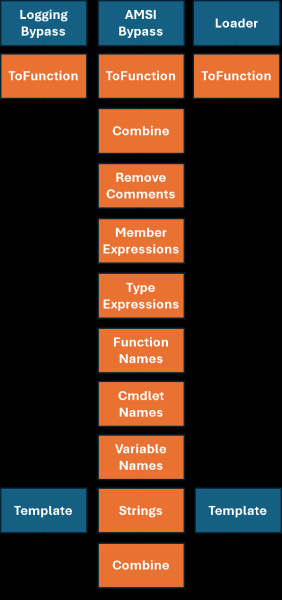
The methodology involves a four-stage attack chain, beginning with a PowerShell command that triggers subsequent stages.
The attack relies on a sophisticated combination of logging bypass, AMSI bypass, and carefully applied obfuscation techniques to avoid detection.
“Microsoft has put a ton of effort into deploying good heuristic signatures to block known AMSI bypass techniques and common ways they are obfuscated,” notes the researcher at Practical Security Analytics LLC, highlighting how the security landscape has evolved.
“Windows Defender now detects manipulation of code within AMSI.dll which effectively eliminates an entire category of AMSI bypass techniques.”
SpecterInsight Payload Pipeline Interface (Source – Practical Security Analytics)
Technical Implementation
At the core of the bypass technique is the AmsiScanBufferStringReplace method, which avoids detection by searching for the string “AmsiScanBuffer” in CLR.DLL and overwriting it.
This prevents CLR.DLL from calling the function when loading a payload, effectively disabling AMSI scanning of reflectively loaded .NET modules.
Unlike other techniques that patch the AmsiScanBuffer function directly, this method doesn’t trigger Windows Defender‘s behavioral signatures.
The attack chain leverages multiple stages of obfuscation, including removing comments, obfuscating member expressions, type expressions, function names, cmdlets, variables, and strings.
The payload is further disguised by padding it with legitimate, non-malicious PowerShell scripts to make it blend in with normal system operations.
When the obfuscated payload was submitted to VirusTotal, it recorded zero detections, confirming its effectiveness against current security solutions.
The researcher noted that NICS Labs identified “suspicious things about the script” but couldn’t see through the obfuscation, indicating that while AI integration into antivirus solutions may present future challenges for attackers, current implementations remain vulnerable.
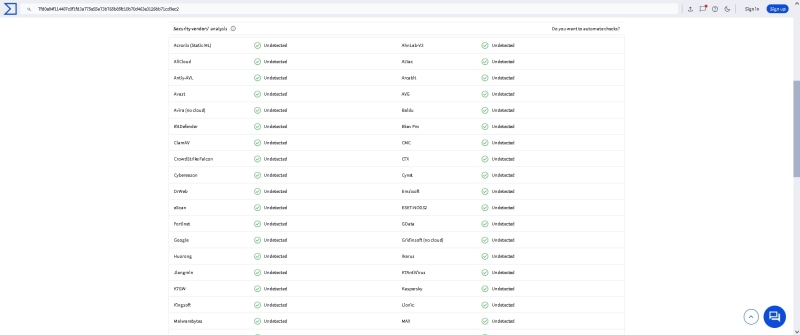
VirusTotal Results Showing Zero Detections (Source – Practical Security Analytics)
Security teams are advised to implement defense-in-depth strategies and consider advanced endpoint detection and response solutions that look beyond signature-based detection methods.




