Physical penetration testing provides crucial insights into real-world security vulnerabilities that might be overlooked in purely digital assessments.
A recent case study conducted by Hackmosphere for a furniture retailer, referred to as ExCorp, revealed how physical access to facilities could compromise internal networks despite robust cybersecurity measures.
The penetration test identified four critical vulnerabilities that could potentially allow malicious actors to breach the company’s digital infrastructure without sophisticated hacking techniques.
This case demonstrates that cybersecurity strategies must encompass both digital and physical dimensions to be truly effective.
The Hackmosphere team employed a methodical approach to their physical penetration testing engagement. Initially, they gathered publicly available information about the store’s operations, including opening hours and staff schedules.
Subsequently, they conducted reconnaissance by posing as customers to observe employee patterns, accessible computer locations, and the store layout.
Throughout these visits, the team varied their appearance using different clothing styles and accessories to avoid detection, as social engineering was explicitly prohibited in this assessment.
The reconnaissance phase enabled the testers to formulate intrusion scenarios in consultation with the client.
Multiple visits were conducted in pairs to maintain discretion and ensure comprehensive coverage of potential vulnerabilities.
The team was particularly interested in identifying weaknesses that could provide access to the internal network, as this would represent a significant security breach with potentially severe consequences.
During the assessment, the analysts at Hackmosphere observed that store computers were frequently left unlocked and unattended during employee breaks.
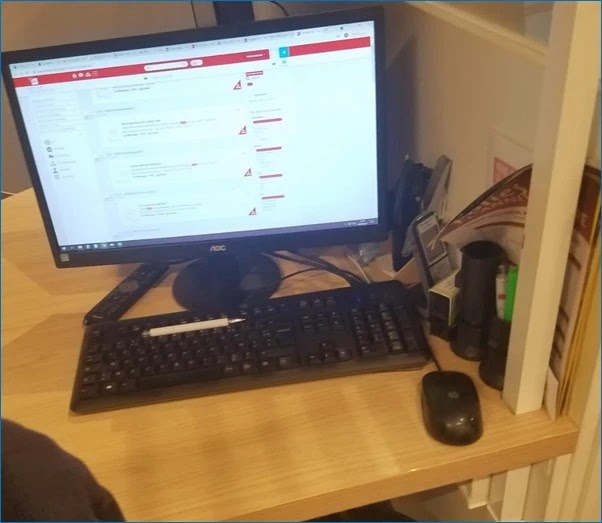
The sales lobby where these vulnerable terminals were located (Source – Hackmosphere)
These computers, used by both regular staff and kitchen designers, presented an obvious entry point for attackers in a high-traffic public space.
Hackmosphere recommended implementing automatic screen locking after five minutes of inactivity or badge-based authentication to mitigate this risk.
Vulnerabilities Exposed
The second major vulnerability involved functional USB ports on lobby computers. The penetration testers were able to connect a “Rubber Ducky” USB device to the terminals during brief periods when staff were away from their stations.
This device allowed them to execute commands and gain control of machines connected to the internal network.
Through this access, malicious actors could potentially deploy ransomware, keyloggers, or other malware, while also exfiltrating sensitive customer data.
Network logs showed the successful compromise, with the device establishing a connection to the ExCorp.com.local domain.
The third weakness involved unsecured RJ45 network ports accessible to the public. The team connected a LanTurtle device to an exposed network socket hidden under a desk, obtaining an IP address (10.3.86.30) within the internal network.
The device established an SSH connection encapsulated in TLS on port 443 to bypass firewall restrictions, providing remote access to ExCorp’s internal systems.
The network configuration revealed multiple interfaces as shown in the connection data, including eth0 (172.16.84.1) and eth1 (10.3.86.30), showing complete network penetration.

The device was concealed while maintaining an active connection (Source – Hackmosphere)
Finally, the assessment team gained unauthorized access to the manager’s office by consulting the building’s emergency evacuation map, which improperly disclosed the office location.
Posing as fire hydrant inspectors, they navigated to the office unquestioned by employees and successfully entered the unoccupied space.
They left an object in the room as proof of successful intrusion. This highlighted serious deficiencies in physical access controls and employee security awareness.
The case study demonstrates that comprehensive security requires attention to physical vulnerabilities alongside digital protections.
Organizations must implement protocols for securing employee terminals, especially in public-facing environments, while simultaneously training staff to recognize and respond to suspicious behavior.
Besides this, Hackmosphere analysts affirmed that even robust cybersecurity investments can be undermined by overlooking basic physical security measures.




