Microsoft has announced plans to enhance security measures by removing the Data Encryption Standard (DES) encryption algorithm from Kerberos authentication in upcoming Windows releases.
This security change will affect Windows Server 2025 and Windows 11 version 24H2 computers after they install Windows Updates released on or after September 9, 2025.
The removal represents an important step in Microsoft’s ongoing Secure Future Initiative (SFI), which aims to eliminate outdated and vulnerable encryption technologies from their ecosystem.
DES encryption, established in 1977 as the first standard encryption algorithm for business use in the United States, has become increasingly vulnerable to security breaches over time.
The algorithm was incorporated into Kerberos in RFC1510 (1993) and appeared in Windows’ first Kerberos implementation with Windows 2000.
However, Windows systems never natively relied on DES for Kerberos, defaulting instead to RC4 for Windows-to-Windows transactions.
As of Windows 7 and Windows Server 2008 R2, DES has been disabled by default but remained available as an optional component when manually enabled by administrators.
Besides this, researchers at Microsoft noted that the transition to disable DES in Kerberos will occur in phases. Currently, Windows operates in a “Compatibility Mode” where DES is disabled by default but can be manually configured if required.
After September 2025, affected systems will enter “DES in Kerberos Disabled Mode,” where DES will no longer be supported as an encryption cipher in any Kerberos function.
It’s important to note that DES will not be removed from earlier Windows versions, allowing organizations time to transition their systems.
Microsoft strongly recommends that organizations identify and address any current use of DES encryption before the September 2025 security update.
Organizations should detect DES usage, identify applications relying on it, and reconfigure them to use stronger ciphers like the Advanced Encryption Standard (AES).
Detection and Remediation
To identify DES usage, administrators can utilize PowerShell scripts that scan security event logs for Kerberos Key Distribution Service (KDCSVC) Event IDs 4768 and 4769.
These events are logged whenever a Key Distribution Center issues a Kerberos Ticket Granting Ticket or when a Kerberos service ticket is requested.
After identifying DES usage, administrators should disable it through Active Directory and Group Policy settings.
In Active Directory Users and Computers policy, administrators should ensure the “Use only Kerberos DES encryption types for this account” option is unchecked for all accounts.
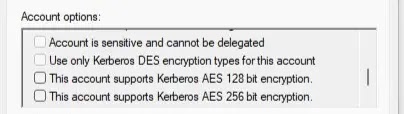
Screenshot of account options in Active Directory Users and Computers policy showing the DES encryption checkbox (Source – Microsoft)
Additionally, in Group Policy, navigate to “Network security: Configure encryption types allowed for Kerberos” located at Computer ConfigurationWindows SettingsSecurity SettingsLocal PoliciesSecurity Options.
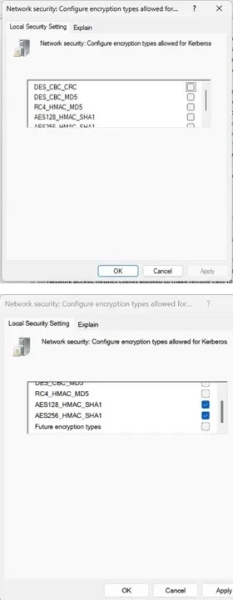
Dialog box for configuring Kerberos encryption types (Source – Microsoft)
For accounts created on older domain controllers running Windows Server 2003 or earlier, Microsoft advises changing the account’s password to ensure AES compatibility.
Organizations should gradually transition from DES to AES encryption, ensuring all domain trusts support AES and implementing proper testing and rollback procedures during the transition.




