A sophisticated exploit kit called MOONSHINE has been actively targeting Android messaging apps to plant backdoors on user devices.
The toolkit has been under continuous monitoring since 2019 and was recently found to have an upgraded version with enhanced functionality and protection against security analysis.
The threat actor behind this attack, Earth Minotaur, mainly targets Tibetan and Uyghur communities. Their modus operandi includes:-
- Send carefully crafted messages via messaging apps
- Entice victims to click on embedded malicious links
- Redirecting victims to the MOONSHINE exploit kit server
- Installing a cross-platform backdoor called DarkNimbus
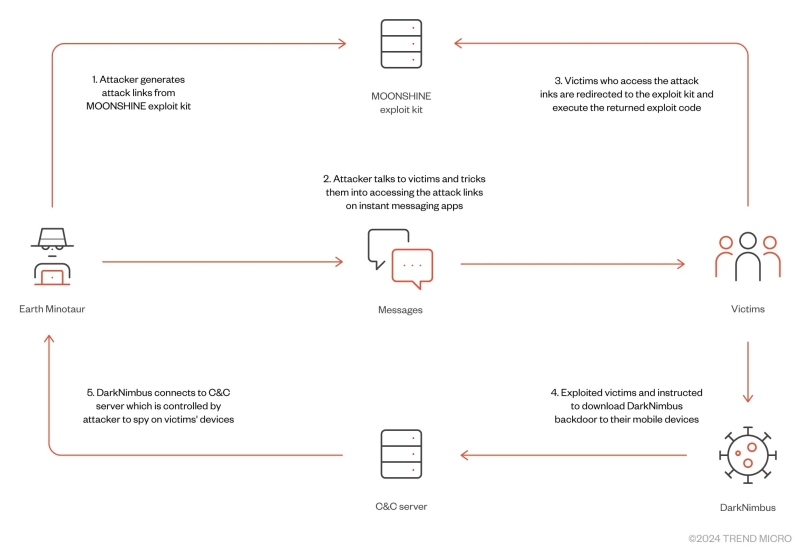
The Earth Minotaur’s attack chain (Source – Trend Micro)
Security experts at Trend Micro have observed attack links disguised as legitimate content, including government announcements, COVID-19 news, religious information, and travel updates.
Technical Analysis
The upgraded MOONSHINE kit uses a variety of advanced technologies:-
- Preconfigured attack links: Each link contains encoded information about the disguised legitimate link, timestamp, and tag
- Browser version validation: exploits are only delivered to vulnerable versions of the target application
- Multiple Chromium vulnerabilities: targeting various versions of Chromium and Tencent Browser Server (TBS)
- Phishing downgrade: attempts to trick users into downgrading their browser engine to a vulnerable version
The kit can target multiple Android apps, including WeChat, Facebook, Line, and QQ.
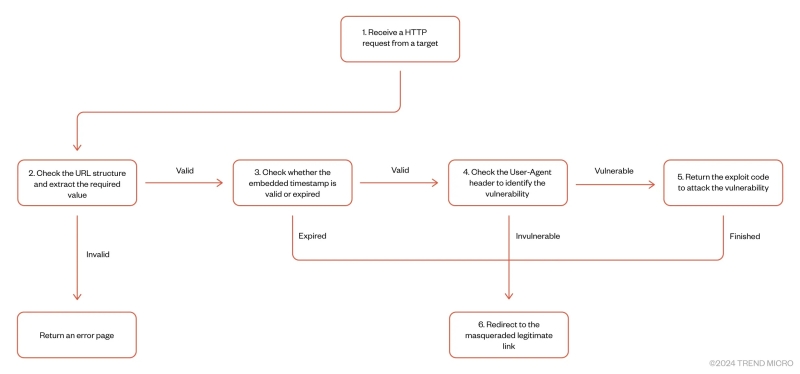
The verification process of the MOONSHINE exploit kit (Source – Trend Micro)
The main payload of the MOONSHINE toolkit is the DarkNimbus backdoor, which has Android and Windows versions:-
Android version features:-
- Collect device information, installed applications, and geolocation data
- Steal personal information from contact lists, call logs, and messaging apps
- Support call recording, photo taking and screen recording
- Abusing Android’s Accessibility Services to Spy on Conversations in Messaging Apps
Windows version features:-
- Collects host information, installed applications, and browsing history
- Capture screenshots and keystrokes
- Steal browser credentials and clipboard data
- execute shell commands
Both versions use a similar command structure and communicate with a command and control (C&C) server to steal data and receive instructions.
While Earth Minotaur is considered a unique threat actor, the MOONSHINE exploit kit has been linked to multiple Chinese operations:-
- Poison Carp: Previously associated with Moonlight, but different from the Minotaur
- UNC5221: MOONSHINE Server Used in Recent Ivanti Zero-Day Attack
- Possible links to APT41 and Winnti groups based on shared malware characteristics
The widespread use of MOONSHINE and its related tools by Chinese threat actors suggests the existence of a complex ecosystem of shared resources and techniques in cyber espionage operations.
To prevent such attacks, users should exercise caution when clicking on links in suspicious messages and update their applications to the latest versions to mitigate known vulnerabilities.




