Security researchers at Positive Technologies have uncovered a sophisticated malware campaign dubbed “Desert Dexter” that has compromised more than 900 victims worldwide since September 2024.
The attack, discovered in February 2025, primarily targets countries in the Middle East and North Africa, with Egypt, Libya, UAE, Russia, Saudi Arabia, and Turkey being the most affected regions.
The threat actors behind Desert Dexter employ a social engineering strategy that leverages the region’s current geopolitical climate.
They create fake news channels on social media platforms, particularly Facebook, masquerading as legitimate media outlets such as Libya Press, Sky News, and The Times of Israel.
These channels publish advertisements containing links to malicious files hosted on legitimate file-sharing services or in Telegram channels.
Message containing a malicious archive in a Telegram channel (Source – Positive Technologies)
When victims click on these links, they download RAR archives containing malicious JavaScript or BAT scripts that initiate a complex infection chain.
The archives appear to contain sensitive political information, exploiting users’ curiosity about regional conflicts.
Positive Technologies researchers noted that the malware deployed in these attacks is a sophisticated modification of AsyncRAT, customized to search for cryptocurrency wallets and establish communication with a Telegram bot.
Once installed, it creates persistence by modifying registry keys and replacing the user’s startup folder with a malicious path.
Victims span various sectors including oil production, construction, information technology, and agriculture.
The widespread impact demonstrates how effective social engineering tactics can be when combined with legitimate services and geopolitical lures.
Kill Chain
The Desert Dexter attack chain employs multiple stages of obfuscation. The initial infection begins with a JavaScript file containing obfuscated code like the following snippet:
var FCZRAVDNOIUC = “C:\ProgramData\YUFJQUSCFHVBYK.ps1”; var XGCJFJGSLBOJF = “[REDACTED]”;
This script then creates a PowerShell file that contains the main payload. The malware employs reflective loading techniques to inject AsyncRAT into legitimate Windows processes, specifically targeting .NET framework files like aspnet_compiler.exe.
The modified AsyncRAT includes a keylogger component and checks for cryptocurrency wallet extensions including Binance Wallet, Phantom, and Trust Wallet.
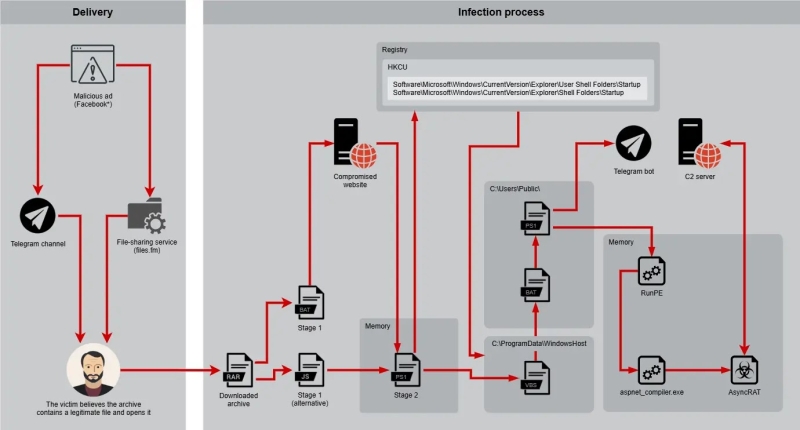
Kill Chain (Source – Positive Technologies)
It also searches for installed wallet applications such as Atomic Wallet and Bitcoin Core. The complete kill chain of the attack shows that how multiple scripting languages work together to establish persistence and execute the final payload.
Communication with command and control servers occurs through DDNS domains linked to VPN services, making attribution challenging but not impossible.
Researchers identified a suspected Desert Dexter member through screenshots inadvertently captured by the malware itself, indicating a possible Libyan origin.




