A groundbreaking tool has emerged in the realm of red teaming, offering a sophisticated method to execute system commands on compromised hosts through Microsoft Teams.
This innovative Command and Control (C2) infrastructure, known as convoC2, leverages the popular collaboration platform to infiltrate and exfiltrate data, making detection significantly more challenging for blue teams.
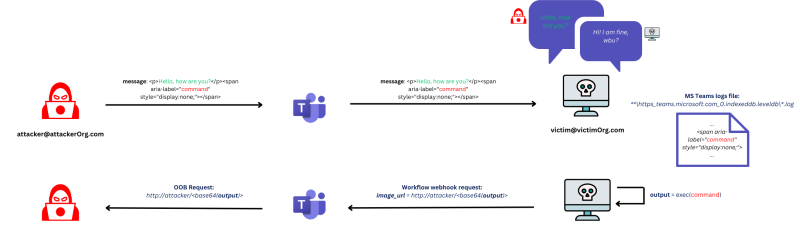
The convoC2 tool operates by embedding commands into hidden span tags within Microsoft Teams messages.
These commands are then executed on the compromised host, with the output cleverly disguised in Adaptive Cards image URLs. This triggers out-of-bound requests to a C2 server, effectively establishing a covert communication channel.
What makes this tool particularly stealthy is its lack of direct communication between the attacker and the victim.
Security analyst, Fabio Cinicolo (cxnturi0n) observed that all HTTP requests from the victim are sent exclusively to Microsoft servers, and since most antivirus solutions don’t scrutinize Microsoft Teams log files, the malicious activity often goes unnoticed.
Technica Analysis
- Cross-Platform Compatibility: The tool has been demonstrated to work on both the new Teams version on Windows 11 and the old Teams version on Windows 10.
- External Org Attack: Notably, the attacker doesn’t need to be in the same organization as the victim, expanding its potential reach.
- Preemptive Command Execution: Even if the victim hasn’t accepted or visualized a chat from an external attacker, commands are still received and executed due to message caching in the log file.
convoC2 Architecture (Source – GitHub)
The convoC2 infrastructure consists of two main components: a server and an agent. The server, which can be easily set up on a public-facing host, manages the C2 operations.
The agent, deployed on the victim’s machine, interacts with the Teams log file and executes the received commands.
To utilize this tool, red teamers need to:-
- Create a Teams channel with a Workflow Incoming Webhook
- Fetch necessary IDs and authentication tokens
- Ensure the victim’s host is running Teams (even in the background)
While this tool represents a significant advancement in red team capabilities, it’s crucial to emphasize that it should only be used in authorized, ethical hacking scenarios.
The potential for misuse underscores the importance of robust security measures and continuous monitoring of collaboration platforms like Microsoft Teams.
The convoC2 tool exemplifies the evolving landscape of cybersecurity, where even trusted platforms can become vectors for sophisticated attacks.
As red teams adopt such advanced techniques, blue teams must remain vigilant, adapting their detection and prevention strategies to counter these emerging threats.




