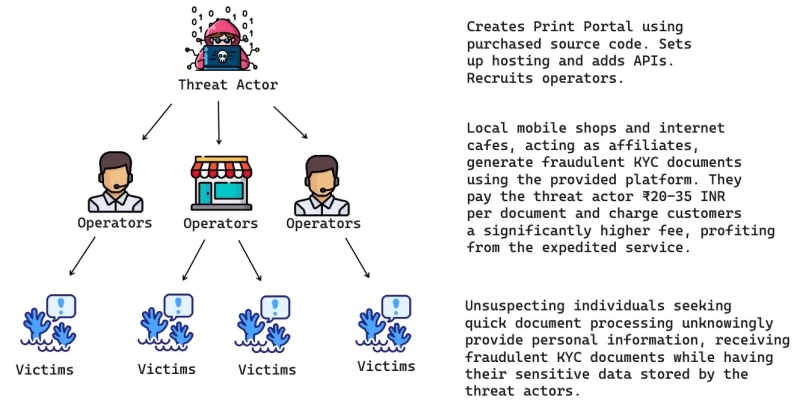
A sophisticated cyber criminal operation known as “PrintSteal” has been discovered generating and distributing fraudulent Indian identity documents on a massive scale.
This operation has established over 1,800 domains impersonating government websites, with approximately 600 currently active.
The criminal network has generated more than 167,000 fake documents, including Aadhaar cards, PAN cards, and birth certificates, earning an estimated ₹40 Lakhs in illicit profits from a single platform alone.
The operation relies on a widespread network of affiliates, including local mobile shops and cyber cafes, who serve as distribution points for these counterfeit documents.
Security analysts at CloudSek noted that these affiliates are recruited through social media platforms like YouTube and Instagram, where tutorials and promotional content advertise the service.
Communication and operational security are maintained through private Telegram groups, where affiliates receive warnings about ongoing law enforcement investigations.
What makes PrintSteal particularly dangerous is its convincing forgery techniques.
PrintSteal operation and network (Source – CloudSek)
The fraudulent documents include QR codes that, when scanned, direct users to fake verification websites mimicking official government portals.
This deceptive verification system creates the false impression that the documents are legitimate, making them difficult to identify as forgeries through basic verification attempts.

Programmatically generated Aadhar card using crrsg.site (Source – CloudSek)
Investigation has attributed one of the main platforms, crrsg.site, to an individual identified as Manish Kumar, who uses the alias “Mg Khaan” and operates the Telegram channel @royalprint_site.
The operation spans across multiple Indian states, with confirmed activity in regions including Andhra Pradesh, Gujarat, Jharkhand, Karnataka, Madhya Pradesh, and Uttar Pradesh.
Technical Infrastructure Behind The Fraud
The technical analysis reveals that PrintSteal’s platforms are built using PHP with MySQL databases to store document templates and user inputs.

Templates used to generate documents (Source – CloudSek)
The source code for these platforms is based on repurposed educational management systems readily available online, significantly reducing the technical barriers to creating similar operations.
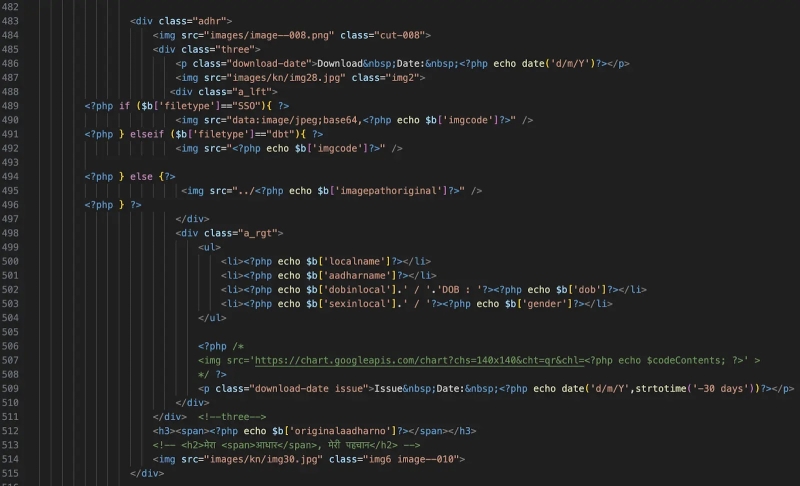
PHP code used to generate Aadhar cards (Source – CloudSek)
The operation integrates with illicit API services, primarily apizone.in and hhh00.xyz, to access sensitive data needed for document generation.
These APIs require only a simple key and utilize standard HTTP GET requests, enabling easy access to restricted information.
The platforms also employ api.qrserver.com to generate QR codes that link to fraudulent verification pages designed to mimic official government websites like crsorgi.gov.in.
The threat actors distribute their platforms’ source code through various channels, facilitating the rapid proliferation of similar fraudulent operations. Law enforcement agencies are currently working to disrupt this network through domain takedowns and financial flow investigations.




