Several sophisticated multi-stage malware campaigns were revealed by recent findings from Palo Alto Networks’ Unit 42 have employing advanced encryption techniques to evade detection.
Threat actors are increasingly using the Advanced Encryption Standard (AES) in combination with code virtualization to protect malicious payloads, creating a complex chain of obfuscation that challenges traditional security measures.
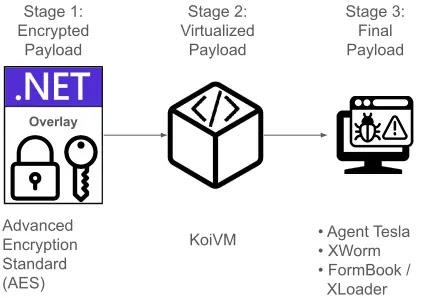
Chain of obfuscation techniques (Source – Plao Alto Networks)
These malware samples hide their payloads within PE overlays using AES cryptography in cipher block chaining (CBC) mode.
This technique employs symmetric keys and initialization vectors to encrypt ciphertext, making it significantly more difficult to analyze than simpler XOR-based obfuscation.
The malware samples examined contained an ASCII string marker that delimits the encryption parameters, which the main .NET code references to locate and decrypt the hidden payloads.
Here the security analysts at Palo Alto Networks noted that the obfuscation chain typically begins with an encrypted payload in the PE overlay, which contains the AES key, initialization vector, and ciphertext for the second stage.
Attackers add arbitrary padding using null bytes and repeating strings (such as “PAPADDINGXX”) to further evade signature-based detection systems.
When the first stage executes, it extracts these cryptographic materials using the marker as a delimiter and decrypts the next payload in memory.

AES encryption operating in CBC mode (Source – Plao Alto Networks)
The above image illustrates how AES encryption operates in CBC mode, demonstrating the encryption process that these threat actors utilize.
The encrypted payload typically contains tokens for performing Antimalware Scan Interface (AMSI) bypass and dynamic .NET Framework code execution through reflection.
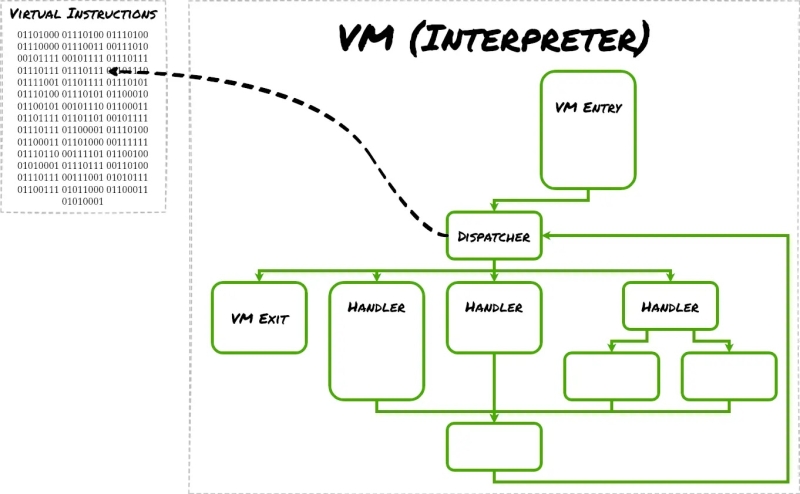
Architecture of VM-based obfuscation (Source – Plao Alto Networks)
The second stage of these attacks introduces an even more complex protection mechanism: code virtualization through KoiVM, a plugin for the ConfuserEx obfuscation tool.
This technique transforms the code into specialized instructions that can only be executed by a custom interpreter, adding another layer of complexity that standard disassemblers cannot easily analyze.
Malware Families Utilizing Advanced Encryption
Security researchers identified several malware families employing these sophisticated obfuscation techniques.
Agent Tesla, XWorm, and FormBook/XLoader samples were discovered using this multi-layered approach.
These samples utilize embedded AES-encrypted resources in their Stage 2 payloads, which are decrypted and executed in memory at runtime.
The XWorm samples further encrypted their configuration parameters using AES in Electronic Codebook (ECB) mode with hard-coded keys stored in variables named “Mutex”.
This approach allows the malware to restore its configuration values, including command and control endpoints, while remaining difficult to detect.
The transition from traditional obfuscation methods to these advanced techniques represents a significant evolution in malware sophistication, demonstrating how threat actors continue to develop more resilient methods to protect their malicious code from analysis and detection.




