Vulnerability management tools play an important role in detecting, analyzing, and patching vulnerabilities in web and network-based applications. The most commonly used words in the security field are vulnerability, risk, and threat.
Risk is the possibility of causing damage or loss, and threat is an adverse event that exploits a vulnerability. Finding these weaknesses is essential to protect every asset and company’s data. Vulnerabilities are weaknesses or loopholes in a system that can pose a threat to it.
Vulnerability management tools are designed to identify issues. Many security researchers and companies use the Common Vulnerability Scoring System (CVSS) to rank the severity of vulnerabilities.
Tools regularly scan systems or networks for vulnerabilities and outdated software to protect them from external and internal threats. It includes processes, plans, and tools to find, assess, and report system or network security vulnerabilities.
Before you begin the vulnerability management process, you must complete specific tasks, such as determining the scope, selecting tools to identify vulnerabilities, providing roles and responsibilities for your team, and creating policies and SLAs. Implementing a policy is only half the job, as you may need to fine-tune it to keep up with evolving threats. For example, you can’t take a one-and-done approach to your firewall. A firewall policy manager can help you monitor and upgrade firewall policies when needed.
Four Essential Steps In The Vulnerability Management Procedure
- Identify vulnerabilities: – Use various vulnerability scanners to scan systems, devices working in the network, databases, virtual machines, servers and services with open ports to identify potential security holes.
- Assessing Vulnerabilities:- The identified vulnerabilities are then assessed using the risk score of the organization’s operations and focus is placed on them accordingly.
- Dealing with vulnerabilities: Based on the priority of the vulnerability, three approaches are used to deal with the vulnerability: remediation, mitigation, and acceptance.
- Reporting vulnerabilities: Reporting is critical to any assessment or process. Found vulnerabilities need to be properly documented, including steps to reproduce, impact, and mitigation.
Strengthening infrastructure security with vulnerability management solutions can make users more efficient and make it more difficult for attackers. These tools can find vulnerabilities and fix them before attackers do.
Here Are Our Picks For The 10 Best Vulnerability Management Tools In 2024 And Their Feature
- Intruder: Automated vulnerability scanner with proactive monitoring and cloud-based security insights.
- Qualys: A comprehensive cloud-based platform for continuous vulnerability management and compliance.
- Acunetix: Specializes in network vulnerability scanning, with accurate detection and reporting.
- Tripwire: Provides powerful security configuration management and file integrity monitoring.
- Astra Pentest: Provides continuous vulnerability assessment, detailed reporting, and actionable remediation guidance.
- Rapid7: An integrated platform for vulnerability management, detection, and response.
- Syxsense: Combines endpoint management with real-time vulnerability detection and patching.
- F-Secure: Provides proactive vulnerability scanning and threat intelligence for enhanced security.
- OutPost24: Scalable network security assessment with continuous monitoring.
- BreachLock: A cloud-native platform for AI-powered vulnerability scanning and penetration testing services.
Best Vulnerability Management Software – 2024 Features
| Vulnerability Management Tools | Keywords | Independent functions | price | Free Trial/Demo |
|---|---|---|---|---|
| 1. Intruder | 1. Proactively scan for emerging threats 2. Attack surface monitoring and reduction 3. Simplify cloud security through AWS, GCP, and Azure integration 4. Asset discovery and network scanning 5. Actionable remediation recommendations and compliance reporting |
Automated network vulnerability scanning. | Starting at $99 per month | Yes |
| 2. Qualys | 1. Vulnerability Management 2. Asset discovery and inventory 3. Vulnerability Assessment 4. Patch Management Integration |
Cloud-based continuous security monitoring. | Prices vary. Please contact for a quote | Yes |
| 3. Acunetix | 1. Web vulnerability scanning 2. Deep scanning capability 3. OWASP Top 10 Coverage 4. Network Scanning |
Comprehensive web application security testing. | Prices vary, please contact for a quote | Yes |
| 4. Tripwire | 1. Configuration Management 2. Vulnerability Management 3. File Integrity Monitoring (FIM) 4. Security configuration assessment |
File integrity monitoring and compliance. | Contact for custom pricing | No |
| 5. Astra Penetration Testing | 1. Automatic scanning 2. Deep scanning capability 3. Intelligent fuzz testing 4. Customizable test profiles |
Manage penetration testing with actionable reports. | Starting at $699 per scan | Yes |
| 6. Rapid 7 | 1. Vulnerability Management 2. Penetration Testing 3. Incident detection and response 4. Application Security |
Dynamic application security testing. | Starting at $5,775 per month | Yes |
| 7. Syxsense | 1. Endpoint Management 2. Patch Management 3. Security Assessment and Monitoring 4. Remote control and troubleshooting |
Unified endpoint vulnerability management. | From $600 per year | Yes |
| 8. F-Secure | 1. Endpoint protection 2. Threat Intelligence 3. Incident Response and Forensics 4. Vulnerability Management |
Advanced threat detection and response. | Pricing based on required solution | No |
| 9. OutPost24 | 1. Vulnerability Management 2. Web Application Security 3. Cybersecurity 4. Cloud Security |
Scalable vulnerability management and assessment. | Contact for pricing details | Yes |
| 10. BreachLock | 1. Vulnerability Assessment 2. Penetration Testing 3. Web Application Testing 4. Network security testing |
Penetration Testing as a Service (PTaaS). | Custom pricing available upon request. | Yes |
1. Intruder
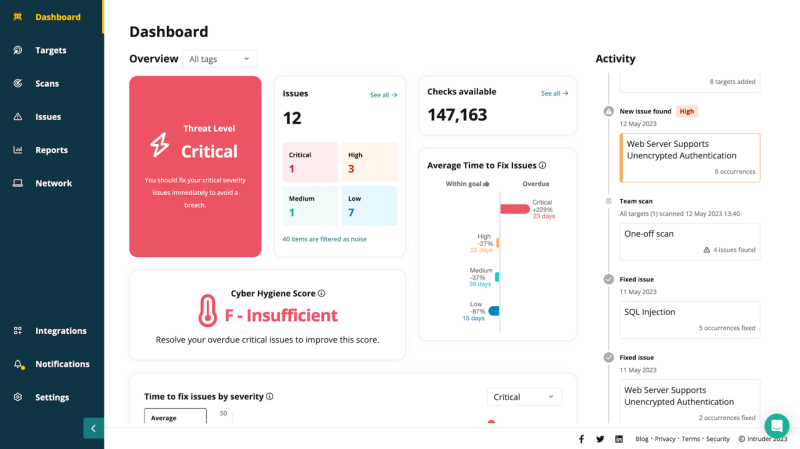
Intruder
Intruder combines continuous network monitoring, automated vulnerability scanning, and proactive threat response into a single platform. This approach provides a detailed view of your attack surface so you can remediate the most critical vulnerabilities quickly and effectively.
Intruder Reports can demonstrate your commitment to security or compliance with ISO 27001 and SOC 2 to partners and customers. Additionally, Intruder Cyber Hygiene Scores can track the time it takes to resolve issues and how you compare to industry standards.
You can easily integrate Intruder with your cloud provider (AWS, Azure, Google Cloud) to get proactive alerts when exposed ports and services of your digital assets change, and automatically scan your systems upon any changes.
feature
- Proactive scanning for emerging threats
- Attack surface monitoring and reduction
- Simplify cloud security with AWS, GCP, and Azure integration
- Asset discovery and network scanning
- Actionable remediation recommendations and compliance reporting
| What is good? | What else can be improved? |
|---|---|
| Proactively conduct comprehensive inspections and scans | Additional options such as vulnerability hunting are only available on the Premium and Vanguard plans. |
| Expert team of penetration testers | Improve integration with more tools. |
| Easy to use, intuitive design | Enhanced user interface design. |
| Multi-developer integration with Jira, Slack, GitHub, and more | Faster scanning and reporting times. |
| Excellent and responsive support team | |
| Displays assets exposed to the Internet | |
| Compliance automation and high-quality reporting |
2. Qualys
Qualys
Vulnerability management tool Qualys proactively reduces risk by identifying all environmental assets and assessing risk by vulnerability, support, and asset class. It allows companies to easily catalog software, hardware, and unmanaged network assets and tag critical assets.
Compatible with patch management solutions and configuration management databases (CMDBs), the tool can quickly discover, prioritize and automatically and scalably remediate vulnerabilities to reduce risk.
All discovered hardware, including databases, servers, and network components, is automatically categorized by Qualys. It also records the software, services, and traffic installed on the system and its current operational status.
feature
- With Qualys’ vulnerability management tools, you can find and prioritize vulnerabilities in your networks, systems, and applications.
- With Qualys, organizations can find and list all of their IT assets.
- It has continuous monitoring tools to keep you informed about the security of your IT assets.
- It helps businesses ensure they comply with safety rules and industry laws.
- Automatically find security holes in legacy systems.
- Automatically detect and understand all network threats.
- Assessment of the security of multi-cloud systems.
| What is good? | What else can be improved? |
|---|---|
| Remediate threats quickly and at scale. | Most features require a license. |
| Manage asset vulnerabilities throughout the vulnerability lifecycle. | It takes a long time to get the scan results. |
| Awesome user interface and accuracy of information. | Terrible customer support. |
| Because of the cloud proxy, there are few to no false positives. | Mobile endpoints are not as clearly defined as cloud endpoints. |
3. Acunetix
Ankunette
Acunetix is a powerful vulnerability management software specifically designed for web application security, providing automated scanning capabilities to detect and remediate a wide range of vulnerabilities, including SQL injection, XSS, and other web-based threats.
The software provides detailed vulnerability reporting and seamlessly integrates with popular development and CI/CD tools, enabling organizations to identify and address security vulnerabilities earlier in the development cycle, thereby enhancing their overall security posture.
Supporting both on-premises and cloud deployments, Acunetix provides flexibility and scalability for businesses of all sizes, while its intuitive interface and comprehensive dashboard make vulnerability management efficient and straightforward.
feature
- Acunetix automatically scans websites and web applications which check for security vulnerabilities.
- Acunetix uses advanced testing methods to more thoroughly discover vulnerabilities.
- Acunetix finds vulnerabilities in web applications listed in the OWASP Top 10 and CWE/SANS Top 25.
- These lists are widely used as the industry standard for web application security.
- Use Acunetix’s network scanning tool to find network-based vulnerabilities and network-related devices.
- Acunetix immediately added the vulnerability to its list and marked it as “Open.”
- Test again to ensure the defect has been fixed correctly.
- It makes macros that can automatically scan password-protected areas.
| What is good? | What else can be improved? |
|---|---|
| Scan multiple domains in a short time. | Some versions of this tool are unstable. |
| Detects over 7,000 vulnerabilities, including zero-day vulnerabilities | Scans have fewer configuration options. |
| Ability to schedule daily, weekly, and monthly scans. | Specification of pre-recorded login sequences is more challenging. |
| Initially, setup and configuration were easy. | Multiple endpoints are not supported. |
4. Tripwire
Tripwire
Tripwire vulnerability management software provides continuous monitoring and assessment of your IT environment, identifying vulnerabilities in server, network, and cloud infrastructure, enabling organizations to effectively prioritize and remediate risks.
The software integrates with existing security tools to provide actionable insights, helping security teams focus on high-risk vulnerabilities and ensure compliance with industry regulations and internal security policies.
Tripwire’s solutions provide automated patch management and configuration controls, reducing the attack surface while maintaining system integrity, making them a critical component of a comprehensive cybersecurity strategy.
| What is good? | What else can be improved? |
|---|---|
| What is good? | Technical support is less than impressive. |
| Advanced vulnerability scoring methodologies. | Generates unnecessary network traffic. |
| Reduce network impact. | Some vulnerability findings were inconsistent. |
| Reports tailored to specific audiences. | Vulnerability tracking is not effective. |
5. Astra Pentest
Astra Penetration Testing
Astra Pentest is a sophisticated automated vulnerability management application that assesses and displays asset vulnerabilities in addition to manual penetration testing.
In addition to more than three thousand automated and manual penetration tests, the platform checks assets for critical vulnerabilities (CVEs) listed in the OWASP Top Ten and SANS 25. It includes all the tests required for GDPR, HIPAA, and ISO 27001 compliance.
Administrators can easily track and control vulnerabilities using a codeless dashboard. CVSS score, expected loss, and overall corporate impact determine the vulnerability risk score. Exams available for ISO 27001, SOC 2, PCI-DSS, HIPAA, and GDPR.
| What is good? | What else can be improved? |
|---|---|
| Integrate with CI/CD platforms, Slack, and Jira. | Fewer integration options available. |
| Maximize return on investment (ROI). | It may not detect some malware attacks that slip through the net. |
| Accurate risk scoring and comprehensive remediation guidance. | Astra requires an external dependency, namely manual penetration testing. |
| The support is excellent, fast, and comprehensive. |
6. Rapid 7
Fast 7
Rapid 7 InsightVM and Nexpose, an on-premises vulnerability scanner, address vulnerabilities. By combining multiple security technologies, Rapid 7 enables teams to automate processes, monitor networks, manage vulnerabilities, analyze and block threats, and more.
Nexpose helps you prioritize risks through configuration, control, vulnerability, and real-time change assessments to reduce threat exposure. When it comes to penetration testing applications, Rapid 7 is your best choice.
Nexpose simplifies the grouping of assets by remediation responsibility and makes it easy to generate remediation reports for asset teams – integrating reconnaissance, payload, and closure capabilities in a single program.
| What is good? | What else can be improved? |
|---|---|
| Track and communicate progress. | Frequent updates and console locks. |
| Easily implement RESTful APIs. | Scheduling can turn into a nightmare if not monitored closely. |
| Integrates with 40+ technologies. | No customization or prioritization is possible using credential scanning. |
| Advanced remediation, tracking and reporting capabilities. | There are fewer compliance issues involved with this agency. |
| Large collection of templates for scanning assets. | This tool does not have a real-time threat protection module. |
7. Syxsense

System Awareness
Syxsense is a top vulnerability management solution because it sees and understands every endpoint in the cloud, on-premises, and anywhere else or in the network. It uses artificial intelligence and industry expertise to monitor and protect endpoints to prevent and eliminate threats.
Syxsense provides security through managed services, 24/7 coverage, and compliance. Patch management and vulnerability scanning help companies combine cybersecurity with IT management.
Syxsense makes it simple to connect to remote computers without having to accept. This can help non-technical personnel. Syxsense’s dynamic searches prioritize device groups and remediation based on company needs. System configuration, severity, risk, and affected operations may change these characteristics.
| What is good? | What else can be improved? |
|---|---|
| Zero Trust capabilities are integrated into Syxsense. | On slower connections, the remote control tool can be a bit “flashy.” |
| Easily connect to the user’s machine remotely. | Switching between monitors isn’t that great. |
| No need to upload updates manually. | It is common to encounter duplicate device IDs for end-user machines. |
| Package software with ease. | Assess and deploy gaps in patches. |
8. F-Secure
F-Safety
F-Secure (renamed Secure) is a powerful and easy-to-use vulnerability management tool. It is an all-in-one vulnerability assessment and management platform that provides clear, actionable and prioritized threat visibility to support an organization’s security strategy.
Protect yourself from modern attacks and ransomware with this cloud-based software. It combines automated patch management, continuous behavioral analysis, vulnerability management, and dynamic threat intelligence.
The application can check for vulnerabilities and notify users throughout the day. The F-Secure Elements Vulnerability Management API uses JSON and HTTP methods including GET, PUT, POST, and DELETE.
| What is good? | What else can be improved? |
|---|---|
| Real-time protection. | No protection against zero-day attacks or forensics. |
| As the system grows over time, it will scale with it. | Lack of ready-to-use compliance check templates. |
| Automated and customized reporting. | Occasionally too many executables are blocked, causing the system to slow down. |
| Scan templates provide an easy way to store a set of options. | There are some false vulnerability issues in the results. |
| Reduce resource utilization through background protection. | Occasionally too many executables are blocked, causing the system to slow down. |
9. OutPost24
OutPost24
OutPost24 provides a unified vulnerability management platform that continuously monitors, detects, and remediates security risks across networks, applications, and cloud environments, ensuring comprehensive protection against potential threats.
The software provides real-time insight into vulnerabilities, enabling security teams to effectively prioritize high-risk issues, reduce the likelihood of breaches occurring and improve overall security posture.
OutPost24 integrates seamlessly with existing security tools, automating workflows and streamlining processes to increase operational efficiency and help organizations maintain compliance with industry regulations and standards.
| What is good? | What else can be improved? |
|---|---|
| Ensure compliance and ease of reporting. | The GUI, dashboards, and reporting are the main drawbacks. |
| User-friendly internal vulnerability scanner. | This is not easy and requires extra effort to maintain. |
| Raise priority and focus remedial actions. | The report contains a large number of false positives. |
| A risk-based vulnerability management solution. |
10. BreachLock
Breakthrough lock
BreachLock provides a cloud-based vulnerability management solution that combines automated scanning with manual penetration testing to provide comprehensive insight into security vulnerabilities and actionable remediation steps to strengthen an organization’s security posture.
The software integrates seamlessly with existing workflows and tools, providing continuous monitoring and real-time reporting, enabling security teams to quickly identify, prioritize and mitigate vulnerabilities in their IT infrastructure.
BreachLock emphasizes ease of use and scalability, making it suitable for organizations of all sizes. At the same time, its AI-driven platform ensures accurate detection of vulnerabilities and minimizes false positives, thereby improving overall efficiency.
| What is good? | What else can be improved? |
|---|---|
| Fast, scalable, and efficient. | Need for more support |
| Collect a wide range of study materials. | There are hidden fees for using different features. |
| Integration with Jira and reporting capabilities. | The product needs to become more resilient. |
| Collect a wide range of study materials. | The safety threshold needs to be raised. |
| Managed Service Products. | |
| Compliance Management |




