Dynamic malware analysis tools are critical for detecting and understanding modern cyber threats. These tools execute suspicious software in isolated environments to monitor its behavior, such as file modifications, network activity, or registry changes.
Below is a list of the top 10 dynamic malware analysis tools, with insights into their features, benefits, and limitations.
Tools like ANY.RUN’s Interactive Sandbox provides cybersecurity professionals with powerful capabilities to detect and analyze these persistence methods in real-time. By leveraging the MITRE ATT&CK framework, ANY.RUN simplifies the process of identifying and mitigating threats.
What Is Dynamic Malware Analysis?
Dynamic malware analysis is the process of executing potentially malicious software in a controlled environment to observe its real-time behavior.
Unlike static analysis, which examines the code without running it, dynamic analysis involves interacting with the malware to understand how it alters the system and impacts a network during execution.
This technique is particularly useful for analyzing sophisticated or obfuscated malware that hides its true behavior through encryption or packing.
Malware analysis involves tracking various system interactions to understand its behavior. This includes identifying file system changes by detecting created, modified, or deleted files.
Network activities are monitored to track connections to Command-and-Control (C2) servers, specific IP addresses, or domains. Evasion techniques are also identified, including anti-analysis mechanisms like sandbox evasion, virtualization detection, or encryption.
System impact is examined by analyzing alterations to system components such as the Windows registry, processes, and services. Additionally, process behavior is observed through API calls, memory injections, and subprocess creation.
Importance Of Dynamic Malware Analysis
With the increasing complexity of modern malware, dynamic malware analysis has become a core part of cybersecurity strategies. Some benefits include:
- Detecting Advanced Threats:
Dynamic analysis can identify behaviors hidden through obfuscation or encryption, such as ransomware payloads, banking trojans, and fileless malware. - Extracting Indicators of Compromise (IoCs):
Analysts can identify hashes, malicious URLs, IP addresses, and registry keys used in the attack. - Real-Time Insights:
Dynamic analysis provides real-time insights into an attack vector, enabling faster incident response and mitigation. - Contextual Understanding of Attacks:
Security researchers can understand the malware’s intent, identifying whether it exfiltrates data, propagates laterally, or installs other payloads. - Enhancing Threat Intelligence:
Findings from dynamic analysis contribute to threat intelligence by profiling malware families and threat actors.
How Dynamic Malware Analysis Works
Dynamic malware analysis involves executing malware in a controlled, isolated environment to simulate real-world attack scenarios.
The process begins with setting up a virtual machine (VM) or sandbox configured to resemble an actual user environment while ensuring isolation to prevent external system compromise.
The malware is then executed using tools like ANY.RUN, Cuckoo Sandbox, or Joe Sandbox. Analysts observe and log its behavior, tracking changes to files, processes, memory, registry, and network activity.
Key indicators of compromise (IoCs), such as file hashes, malicious IP addresses, and URLs, are extracted for further analysis.
Finally, a comprehensive report is generated, summarizing the malware’s behavior, IoCs, and potential impact, which can be shared with incident response teams or integrated into security systems.
Techniques Used In Dynamic Malware Analysis
Dynamic malware analysis employs a combination of tools and techniques to reveal malware behavior:
Here’s the information structured in a table format:
| Analysis Type | Description | Example |
|---|---|---|
| Behavioral Analysis | Monitors system changes, network communications, and memory usage. | Analyzing a trojan that connects to a remote server for data exfiltration. |
| API Call Monitoring | Tracks API calls made by malware to understand system-level interactions. | Monitoring calls to APIs like RegCreateKey or CreateFileW. |
| Network Traffic Analysis | Identifies malicious activities such as DNS lookups, HTTP requests, or data exfiltration. | Using tools like Wireshark to analyze traffic to a Command-and-Control server. |
| Memory Analysis | Investigates malware that operates entirely within system memory (fileless malware). | Using tools like Volatility to extract and analyze memory dumps. |
| User Interaction Simulation | Some malware activates only after specific user actions, like enabling macros or clicking pop-ups. | Interactive tools like ANY.RUN allow analysts to simulate these actions. |
Cyber Security News Top Pick
Leading the list is ANY.RUN, a highly interactive, cloud-based sandbox that stands out for its real-time, hands-on approach to analyzing malicious samples. Let’s explore the tools in detail.
ANY.RUN is an innovative, cloud-based malware analysis service that enables users to interact with malware samples in real-time.
Unlike traditional sandboxes, which run automatically, ANY.RUN provides analysts with the option to interact with files manually, which is particularly helpful when analyzing malware that requires user input to execute payloads.
Key Features of ANY.RUN:
- Real-Time Interaction:
Users can trigger malware manually by simulating clicks, keystrokes, or other actions. This capability is perfect for analyzing sophisticated malware like ransomware or droppers that depend on user interaction to complete their attack chain. - Dynamic Visualization:
ANY.RUN offers a detailed and intuitive process tree, showcasing events like file operations, registry modifications, and network activities in real time. - Comprehensive Network Monitoring:
The tool captures and visualizes all network traffic, including DNS queries, HTTP requests, and C2 communications. PCAP files can be downloaded for deeper analysis using other tools, like Wireshark. - IoCs Extraction:
Automatically generates a list of Indicators of Compromise (IoCs), such as IP addresses, domains, dropped file hashes, and malicious URLs. - Collaborative Environment:
Analysts can collaborate in real time, making it an excellent tool for incident response teams. - Wide File Support:
Supports an extensive range of malicious file formats, including executables, scripts, documents, and URLs.
10 Best Dynamic Malware Analysis Tools
| 10 Dynamic Malware Analysis Tools | Features | Stand-alone Feature | Pricing | Free Trial / Demo |
|---|---|---|---|---|
| 1. ANY.RUN | Real-time interaction, dynamic visualizations, collaboration, network traffic analysis, and customizable environments. | Interactive, real-time malware analysis platform | Free tier available; paid plans start at $109/month. | Yes |
| 2. Cuckoo Sandbox | Open-source, API call tracking, network traffic monitoring, virtualized environments, multi-format file support. | Open-source automated malware analysis tool | Open-source; free to use. | Yes |
| 3. Joe Sandbox | Cross-platform support, deep memory forensics, YARA rule integration, IoC extraction. | Advanced multi-platform malware analysis engine | Pro cloud tiers start at $4,999/year. | Yes |
| 4. Hybrid Analysis | Cloud-based, automatic IoC generation, static and dynamic analysis combination, severity scoring. | Cloud-based malware intelligence and sandbox | Free to use. | Yes |
| 5. FireEye Malware Analysis | Enterprise-grade solution, zero-day detection, integration with threat intelligence, memory forensics. | Enterprise-grade malware detection and forensics | Pricing details not publicly available; contact for quote. | Yes |
| 6. Detux (Linux-Focused) | Open-source, Linux-specific malware analysis, modular architecture, real-time monitoring. | Linux-specific malware analysis sandbox | Open-source; free to use. | Yes |
| 7. Cape Sandbox | Payload extraction, support for packed malware, detailed reporting, extended Cuckoo Sandbox capabilities. | Cuckoo-based sandbox with process injection | Open-source; free to use. | Yes |
| 8. MalwareBazaar Sandbox | Free, scalable cloud sandbox, detailed malware behavior reporting, focus on IoC generation. | Malware sample sharing and analysis platform | Free to use. | Yes |
| 9. Remnux | Linux-based toolkit, network traffic analysis, reverse engineering capabilities, wide tool integration. | Linux toolkit for malware reverse engineering | Free to use. | Yes |
| 10. Intezer Analyze | Code reuse detection through binary DNA technology, fast analysis, complex malware family classification. | Code reuse analysis for malware classification | Free tier available; contact for premium pricing. | Yes |
1. ANY.RUN (Best Overall)
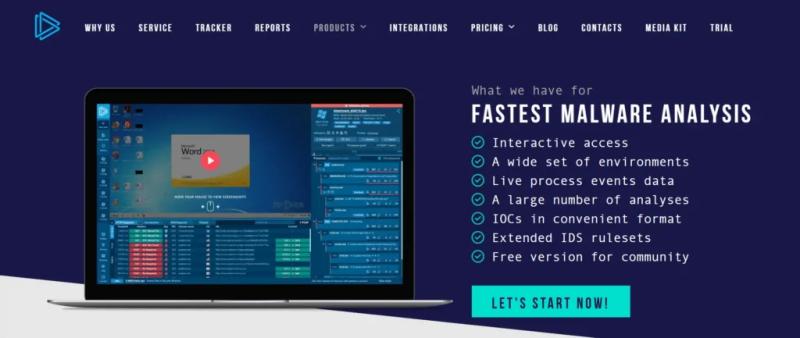
ANY.RUN is a highly interactive cloud-based sandbox designed for real-time malware analysis. Unlike traditional sandboxes, it allows analysts to manually interact with malicious files to simulate user actions (e.g., clicking, typing), which can reveal hidden behaviors.
This makes ANY.RUN ideal for analyzing ransomware, droppers, and malware that requires user input to function fully. It also supports collaborative workflows, making it an excellent choice for Security Operations Centers (SOCs).
With live collaboration features, multiple analysts can work on the same session, ensuring faster incident responses.
Its powerful suite of tools, including TI Lookup, YARA Search, and Feeds enables users to analyze threats, track malicious activity, and collaborate effectively.
With ANY.RUN, security teams can:
- Detect malware in seconds
- Interact with samples in real time
- Save time and money on sandbox setup and maintenance
- Record and analyze all aspects of malware behavior
- Scale their operations as needed
Key Features:
- Real-Time Interaction: Analysts can simulate user actions to trigger malware behaviors.
- Dynamic Visualizations: Provides detailed process trees, file manipulations, and network graphs in real time.
- IoC Extraction: Automatically generates lists of indicators of compromise (IoCs) such as file hashes, malicious IPs, and domains.
- Collaboration: Enables multiple analysts to collaborate on the same analysis session.
- Customizable Environments: Analysts can configure virtual machines (e.g., Windows 10) with specific setups to emulate real-world scenarios.
| What is Good? | What Could Be Better? |
|---|---|
| Beginner-friendly interface. | Cloud dependency may not suit organizations with strict policies. |
| Ideal for malware requiring user interaction. | Advanced features are available only in paid versions. |
| Excellent collaborative features for team analysis. | |
| Real-time execution with detailed visualizations. |
2. Cuckoo Sandbox
Overview:
Cuckoo Sandbox is one of the most recognized open-source solutions for malware analysis. It provides a flexible and extensible environment to execute and monitor malicious files across various formats, including documents, scripts, and executables.
Its modular design allows for extensive customization, enabling analysts to extend its functionality with plugins or integrate it with tools like YARA rules, Suricata for intrusion detection, or Volatility for memory forensics.
Key Features:
- Monitors API calls, file manipulations, and network traffic.
- Supports virtualized, physical, or cloud environments.
- Generates detailed JSON or HTML reports for further investigation.
| What is Good? | What Could Be Better? |
|---|---|
| Free to use and highly customizable. | Requires technical expertise for setup and maintenance. |
| Supports various file types and operating environments. | Time-consuming configuration for new users. |
| Flexible integration with tools like YARA and Suricata. |
3. Joe Sandbox
Overview:
Joe Sandbox is a commercial tool that stands out for its depth of analysis across multiple platforms, including Windows, Linux, macOS, Android, and iOS.
It supports a wide range of file formats and goes beyond basic dynamic analysis by simulating user interactions, enabling analysts to uncover hidden behaviors in malware.
With its deep memory forensics capabilities, Joe Sandbox is especially suited for investigating advanced threats like APTs or state-sponsored attacks.
Key Features:
- Multi-platform support for analyzing cross-OS threats.
- Detailed memory analysis and process simulation.
- YARA rule integration for custom threat detection.
| What is Good? | What Could Be Better? |
|---|---|
| Multi-platform support for cross-OS analysis. | High licensing costs, limiting its accessibility for smaller organizations. |
| Excellent for understanding advanced threats. | May feel overwhelming for beginners due to its feature set. |
| Advanced memory forensics and process simulation. |
4. Hybrid Analysis (CrowdStrike Falcon Sandbox)

Overview:
Hybrid Analysis, now part of CrowdStrike, is a popular cloud-based sandbox tool that automates malware analysis by combining static and dynamic techniques.
It also features a crowd-sourced malware intelligence database, allowing analysts to compare their results with others and gain insights into ongoing malware campaigns.
Its automated classification system provides severity scores for samples, making it an excellent choice for quick triaging of malicious files.
Key Features:
- Combines behavioral and signature-based analysis.
- Severity scoring for samples based on suspicious actions.
- Cloud-based with minimal setup required.
| What is Good? | What Could Be Better? |
|---|---|
| Free tier available for basic usage. | Limited customization options compared to other tools. |
| Excellent for rapid threat triaging. | Relies on third-party tools for advanced configurations. |
| Crowd-sourced threat database enhances analysis. |
5. FireEye Malware Analysis
Overview:
FireEye’s malware analysis platform is designed for enterprise environments, offering advanced capabilities to detect zero-day threats, fileless malware, and advanced persistent threats (APTs).
With its integration into the FireEye Threat Intelligence network, organizations can receive attribution data for attacks, identify threat actors, and track attack campaigns.
This makes it a go-to choice for large organizations that prioritize cybersecurity resilience.
Key Features:
- Behavioral and memory analysis of malware.
- Integration with FireEye Threat Intelligence for attack attribution.
- Supports in-depth fileless malware analysis.
| What is Good? | What Could Be Better? |
|---|---|
| Tailored for large organizations with advanced needs. | Expensive, making it inaccessible for smaller businesses. |
| Excellent at detecting fileless and memory-resident malware. | |
| Integrates seamlessly with FireEye’s threat intelligence. |
6. Detux (Linux-Focused)
Overview:
Detux is an open-source sandbox specifically tailored for analyzing Linux-based malware, making it invaluable for organizations focused on cloud, IoT, or server security.
As Linux becomes increasingly targeted by cybercriminals, Detux offers a much-needed solution for analyzing cryptojackers, rootkits, and other Linux-focused threats in real time.
Key Features:
- Captures file, network, and system-level activities.
- Supports Linux ELF binary analysis.
- Modular design for extensibility.
| What is Good? | What Could Be Better? |
|---|---|
| Designed specifically for Linux ELF binaries. | Limited to Linux malware analysis—no cross-platform support. |
| Lightweight and easy to integrate into workflows. | Requires expertise to set up and customize effectively. |
| Free and open-source. |
7. Cape Sandbox
Overview:
Built on Cuckoo Sandbox, Cape specializes in capturing, unpacking, and analyzing obfuscated or packed malware, making it a core tool for researchers who need to analyze advanced malware like Emotet or TrickBot.
By focusing on payload extraction and de-obfuscation, Cape helps analysts identify the true intent of packed or encrypted malware.
Key Features:
- Payload extraction and decryption.
- Fileless malware detection.
| What is Good? | What Could Be Better? |
|---|---|
| Exceptional for unpacking heavily obfuscated malware. | Less intuitive than GUI-based solutions like ANY.RUN. |
| Supports fileless malware and complex attack chains. | Requires a learning curve for new users. |
| Enables integration with Cuckoo plugins. |
8. MalwareBazaar Sandbox
Overview:
Part of Abuse.ch’s ecosystem, MalwareBazaar Sandbox is a free cloud-based tool designed for analyzing malware submitted to the public MalwareBazaar platform.
It is particularly useful for tracking and understanding the evolution of malware families, making it a favorite among threat researchers who want to keep up with the latest trends in malicious campaigns.
Key Features:
- IoC generation for new malware samples.
- Scalable cloud-based infrastructure.
| What is Good? | What Could Be Better? |
|---|---|
| Free and user-friendly for researchers. | Limited to analyzing public malware samples. |
| Excellent for tracking malware campaigns. | Less advanced than paid alternatives for in-depth analysis. |
| Scalable cloud infrastructure. |
9. Remnux
Overview:
Remnux is a Linux-based toolkit preloaded with a wide array of tools for malware analysis and reverse engineering.
It is highly effective for analyzing network-centric threats, such as botnets and DDoS malware, and comes with pre-installed tools like Wireshark for packet analysis, Radare2 for debugging, and Binwalk for firmware analysis.
Key Features:
- Pre-installed tools for debugging, reverse engineering, and network forensics.
- Lightweight Linux distribution.
| What is Good? | What Could Be Better? |
|---|---|
| Free and user-friendly for researchers. | Limited to analyzing public malware samples. |
| Excellent for tracking malware campaigns. | Less advanced than paid alternatives for in-depth analysis. |
| Scalable cloud infrastructure. |
10. Intezer Analyze

Overview:
Intezer Analyze focuses on code reuse analysis, mapping new malware samples to known families using binary DNA technology. By identifying similarities in reused code, it provides actionable insights into the malware’s ancestry and potential links to known threat groups.
This approach makes it particularly valuable for uncovering connections between new threats and existing attack campaigns.
Key Features:
- Identifies code similarities across malware families.
- Binary DNA technology for malware classification.
| What is Good? | What Could Be Better? |
|---|---|
| Maps malware to known families using unique DNA technology. | Limited capabilities for real-time behavioral analysis. |
| Great for connecting new malware to existing campaigns. | |
| Fast and efficient for polymorphic malware. |
Conclusion
Dynamic malware analysis tools are indispensable for cybersecurity professionals aiming to detect and mitigate advanced threats. Among the top tools, ANY.RUN stands out for its interactivity and real-time capabilities, making it an excellent choice for SOCs and independent researchers alike. Whether you need an open-source solution like Cuckoo Sandbox or a specialized tool like Detux for Linux-based threats, there’s an option here to meet your needs. Choose the right tool for your organization and elevate your malware analysis capabilities.




