Endpoint management tools simplify the management and security of an organization’s endpoint devices, such as desktops, laptops, and mobile devices.
They provide centralized control over device configuration, software deployment, and policy enforcement, thereby increasing IT efficiency.
These tools ensure compliance with security policies and help reduce risk by monitoring and managing the health and security status of endpoints.
Endpoint management solutions often include features such as remote troubleshooting, patch management, and asset tracking, helping to improve overall organizational security and operational efficiency.
Here Are Our Picks For The Top 20 Endpoint Management Tools And Its Features:
- Cynet: It provides comprehensive threat detection, response, and incident automation for endpoint security.
- FireEye Endpoint Security: Advanced threat detection with integrated intelligence and machine learning.
- CrowdStrike Falcon: Advanced threat detection and response through real-time monitoring and AI-driven analytics.
- Tanium: Comprehensive endpoint management with real-time visibility and control across large, complex networks.
- Carbon Black: Continuous threat monitoring and response through behavioral analytics and machine learning.
- ManageEngine Endpoint Central: Unified endpoint management with patching, remote control, and software deployment capabilities.
- Symantec Endpoint Protection: Powerful security suite that offers antivirus, anti-malware, and firewall protection.
- Cisco AMP for Endpoints: Endpoint protection delivered via the cloud with advanced malware analysis and threat detection.
- Forcepoint: A data-centric security platform that protects sensitive data and prevents insider threats.
- McAfee Endpoint Security: Comprehensive endpoint protection with threat prevention, network security, and device control.
- Microsoft Defender for Endpoint: Integrated threat detection and response, deeply integrated with the Microsoft ecosystem.
- SentinelOne: Autonomous endpoint protection with AI-driven threat detection and response.
- CylancePROTECT: AI-based predictive threat prevention with minimal system impact.
- Atera: All-in-one remote monitoring and management, integrated patch management and automation tools.
- Ivanti: Unified endpoint management platform with automated patching, software distribution, and compliance management.
- Sophos: Comprehensive endpoint security with real-time threat intelligence and automated response.
- BlackBerry Unified Endpoint Manager: Provides secure, centralized management for a variety of endpoint devices.
- Palo Alto Networks: Next-generation endpoint protection with AI-driven threat prevention and deep behavioral analytics.
- Citrix Endpoint Management: Secure and manage endpoints, including mobile devices, with integrated workspace solutions.
- Hexnode UEM: Unified endpoint management with support for multiple platforms and powerful security features.
1. Cynet
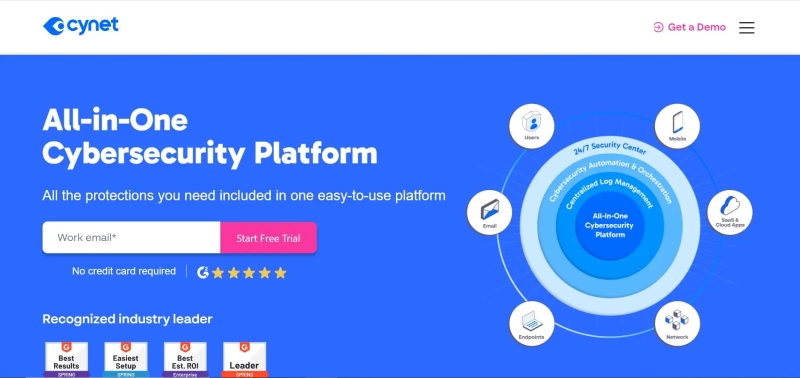
Cynet endpoint management tools combine the comprehensive security capabilities of its all-in-one cybersecurity platform provider, including endpoint detection and response, threat intelligence, and automated remediation, into a single unified platform.
Cynet provides comprehensive protection for your workstations, servers, and mobile devices against malware, ransomware, and other cyber threats.
It comes pre-installed with Next Generation Antivirus (NGAV), Endpoint Protection Platform (EPP), Endpoint Detection and Response (EDR), Device Control, and Mobile Security. Advanced AI-driven analytics improve visibility and management of network endpoints by hunting for threats and detecting anomalies.
feature
- Comprehensive threat protection, including antivirus, ransomware, and malware prevention, keeps your endpoints secure.
- Automated detection and response capabilities can quickly mitigate potential cyber threats.
- A centralized management dashboard provides visibility and control over all connected devices.
- Integration with the MITRE ATT&CK framework enhances threat detection and response strategies.
- 24/7 Managed Detection and Response (MDR) service provides continuous monitoring and support.
| What is good? | What else can be improved? |
|---|---|
| Automated threat detection and response improves security efficiency. | Simplifying the user interface can improve the user experience. |
| Comprehensive coverage includes antivirus, ransomware, and malware protection. | More flexibility is needed to customize detection rules and alerts. |
| Easy to use interface with a centralized management dashboard. | Enhancements for large enterprises will benefit growing organizations. |
2. Trellix Endpoint Security
FireEye Endpoint Security
Trellix Endpoint Security provides advanced protection for your organization’s devices against malware, ransomware, and other cyber threats. It leverages machine learning and threat intelligence to provide real-time threat detection and response.
The platform’s unified interface simplifies management and enhances visibility, ensuring your endpoints are secure and compliant.
The solution includes automated tools for rapid threat remediation and integrates seamlessly with other security systems. Trellix ensures comprehensive protection and resilience against evolving cyber threats for small businesses or large enterprises.
feature:
- Advanced Threat Detection: Use machine learning and threat intelligence for real-time protection.
- Unified management: Centralized deployment and monitoring of security policies.
- Automated Remediation: Use automated response tools to quickly eliminate threats.
- Seamless integration: Compatible with existing security tools for holistic endpoint protection.
| What is good? | What else can be improved? |
|---|---|
| Advanced Threat Detection Using Machine Learning | Resource intensive and may affect device performance |
| Centralized management simplifies policy deployment | Initial setup is complex and may require a learning curve |
| Automatic remediation reduces response time | Occasionally, there will be false positives, which may require manual review |
| Integrates seamlessly with existing security tools | Costly for small businesses or those with limited budgets |
| Scalable pricing options to suit different organization sizes | Older systems may have compatibility issues |
3. CrowdStrike Falcon
CrowdStrike Falcon
The CrowdStrike Falcon endpoint management solution is the industry standard for controlling and protecting endpoints across an organization’s network. Falcon is an endpoint analysis and monitoring solution that helps enterprises quickly mitigate security incidents by discovering and eliminating malicious activity.
The tool uses a vast threat intelligence network to proactively identify and block threats, including malware, ransomware, and other cybercrime, so users always feel safe.
Falcon integrates next-generation antivirus, anti-malware, and endpoint firewall to protect endpoints. It provides complete forensic data and allows remote investigation and cleanup to reduce reaction time and impact of security incidents.
feature
- Leverage enemy knowledge to plan and respond quickly to threats.
- Unparalleled real-time knowledge of network devices, users, and applications reduces risk.
- Centrally log data for security, IT monitoring, and compliance.
- They are blocking name-based attacks in real time.
- A marketplace for enterprises where they can search, try, buy, and install trusted partner applications to maximize their platform investments.
| What is good? | What else can be improved? |
|---|---|
| Advanced threat detection and response. | Cloud operation requires a stable internet connection. |
| Scalable and flexible cloud-native architecture. | CrowdStrike Falcon is cloud-based and requires internet. |
| Real-time endpoint visibility and monitoring. | Some customization options may require a learning curve. |
| Threat intelligence integration for proactive protection. |
4. Tanium
titanium
Tanium is one of the best endpoint management tools that automatically deploys patches and enforces security policy compliance on endpoints. This ensures that all endpoints are up-to-date, reducing potential security issues.
The tool’s comprehensive security capabilities enable businesses to proactively prevent, detect, and respond to cyberattacks targeting their networks and endpoints.
With this solution, organizations can better manage hardware and software endpoint assets. This includes inventory, licensing, and usage. This enables IT departments to maximize efficiency and maintain order with available resources.
feature
- Tanium Threat Response monitors online and offline endpoints for suspicious behavior.
- Tanium Threat Response uses remote forensic investigation to investigate suspicious workstations to help organizations analyze the situation.
- Tanium’s integration with ServiceNow improves data, workflows, and outcomes, giving you greater control, insight, and problem-solving capabilities.
- Proactive data enrichment reduces security breach costs and response times.
| What is good? | What else can be improved? |
|---|---|
| Security features for threat detection and incident response. | Large investments make switching solutions difficult. |
| It enhances patch and configuration management. | Pricing can be higher compared to some competitors. |
| Complete asset management. | Resource-intensive operations may affect network performance. |
| Proactive monitoring improves endpoint performance. |
5. Carbon Black
Carbon Black
Carbon Black is a leader in endpoint management. Its main capabilities are advanced threat detection, response, and prevention.
It uses cutting-edge threat intelligence and machine learning techniques to identify and respond to threats in real time. Features such as program blocking, file integrity checking, and device management all contribute to a high level of endpoint security.
Enforcing security policies and blocking unauthorized access can help organizations protect their endpoints from threats and keep sensitive data safe. It provides extensive forensic evidence to help analysts determine what went wrong, why, and how to prevent it from happening again.
feature
- Protect your company and your customers’ data from malware, non-malware, and “living off the land” threats.
- With a platform that can triage cyberattacks between different components, you can respond offline and minimize endpoint downtime.
- Advanced prevention means monitoring outbreak streams to block ransomware now and in the future.
- Integrate alerting and policies into a single console for endpoint and container context.
- This simplifies and secures company operations.
- Track business and external endpoints.
| What is good? | What else can be improved? |
|---|---|
| Strong endpoint security. | It requires sufficient system resources to run well. |
| Complete incident response and forensics. | Support for older systems and devices is limited. |
| Compliance and governance are critical. | The first step is to maximize the potential of the tool. |
| High performance and scalable. |
6. ManageEngine Endpoint Central
ManageEngine Endpoint Center
ManageEngine Endpoint Central provides services for managing endpoints, including remote management, software distribution, patch management, and configuration management.
Organizations that want comprehensive control over their endpoints should consider implementing ManageEngine Endpoint Central, the most powerful and feature-rich endpoint management product available.
IT administrators can quickly update software and check configurations to maintain endpoint consistency. Enforcement of security requirements, access restrictions, and compliance reporting help organizations meet industry standards.
feature
- Automatically perform operating system and third-party software patches to protect Windows and Mac computers.
- Scan endpoints regularly for security issues and patch them immediately.
- Manage IT assets such as software metering, license management, banned software, etc.
- Built-in package creation templates simplify software installation and uninstallation.
- Zero-trust security with role-based permissions and malicious application blocking.
| What is good? | What else can be improved? |
|---|---|
| In-depth endpoint management. | The UI could be clearer. |
| Security and compliance expertise. | Limited third-party software and device support. |
| Adequate inventory and asset tracking. | Advanced customization may require specialized knowledge. |
| ManageEngine products integrate seamlessly. |
7. Symantec Endpoint Protection

Symantec Endpoint Protection
Symantec Endpoint Protection is the leader in endpoint management. It provides unmatched defense against malware, ransomware, zero-day attacks, and more.
It uses machine learning, behavioral analytics, and vulnerability mitigation to quickly detect and block known and unknown threats. It enhances endpoint security through policy enforcement, software deployment, and real-time threat visibility.
With this tool, IT departments can better manage device configurations, control application execution, and limit access to sensitive data, while also helping to reduce the attack surface and the likelihood of security breaches by enforcing system hardening policies.
feature
- Analyzes all incoming and outgoing traffic and browser protection to prevent computer risks.
- Controls how processes access files and the registry and run.
- You can restrict hardware access and choose which devices can send and receive data.
- This protects against Heap Spray, SEHOP Overwrite, and Java attacks in popular software that have not yet been corrected by the vendor.
- Examine trillions of good and bad files in the global intelligence network.
| What is good? | What else can be improved? |
|---|---|
| Central management console simplifies administration. | Endpoints are resource intensive. |
| Endpoint hardening for enhanced security. | Complexity may require specialized configuration knowledge. |
| Integrate with EDR solutions. | Specific security solutions may leave loopholes. |
8. Cisco AMP for Endpoints
Cisco AMP for Endpoints
Cisco AMP for Endpoints is a comprehensive endpoint management solution that provides better threat protection and complete visibility into endpoints.
With real-time detection, prevention, and response capabilities, businesses can better protect their endpoints from malware, ransomware, and other high-risk attacks.
Thanks to its cloud-based architecture and cutting-edge analytics, Cisco AMP for Endpoints provides better insight into endpoint activity and enables proactive threat hunting and incident response.
feature
- Proper integration to automate security information sharing
- Cisco or partner technologies make policy updates simple and fast.
- You can use a tool to automate and simplify the task.
- Blocking harmful content online and preventing people from clicking on compromised links can address web and email risks.
- Easy, secure endpoint access keeps your company safe.
| What is good? | What else can be improved? |
|---|---|
| Cloud-based architecture is scalable and flexible. | Optimal performance requires adequate network bandwidth. |
| Detect and respond to emerging threats in real time. | Setup and configuration may require technical expertise. |
| Visibility into entire endpoint activity. | Advanced features may require a license. |
| Integrate Cisco security solutions to achieve unified security. |
9. Forcepoint
Power Point
Forcepoint is a data loss prevention (DLP) and endpoint security (ENS) management software. The program is designed to protect your business from sophisticated cyber attacks and safeguard your data.
Forcepoint endpoint protection capabilities include antivirus and anti-malware protection, browser filtering, and behavioral analysis to identify and block risky behavior.
Its DLP capabilities help stop breaches by monitoring and controlling data traffic between devices and channels. The tool’s unified management and reporting console makes it possible to effectively monitor and enforce security policies.
feature
- OCR can discover information in still or moving photos.
- Secure ID for personal data
- Data validity is checked in PII.
- Real names, proximity analysis, and environmental identifiers.
- Custom encrypted identities leak uncontrolled data.
- Microsoft Information Protection integration encrypts files and sets DLP rules.
| What is good? | What else can be improved? |
|---|---|
| Integrated data loss prevention and endpoint protection. | Forcepoint’s solutions can be difficult to integrate with IT tools and processes. |
| Comprehensive protection against advanced threats. | Solutions may target specific security areas, leaving gaps. |
| Central management console simplifies administration. | Handle sensitive data with care. |
| Flexible data control and policy enforcement. |
10. McAfee Endpoint Security
McAfee Endpoint Security
McAfee Endpoint Security is a valuable resource for managing and protecting your company’s endpoints. It protects against many forms of attack, such as malware, ransomware, and zero-day attacks.
The tool will use machine learning and artificial intelligence to identify evolving threats at the earliest and stop them in their tracks. Antivirus, network intrusion prevention, firewall, and application control are some of the features that help achieve a secure endpoint environment.
With McAfee Endpoint Security’s centralized management capabilities, IT can monitor all devices and consistently set and enforce security policies. The tool provides superior threat intelligence and analytics, allowing you to proactively hunt for threats and quickly respond to incidents.
feature
- It discovers new and zero-day threats, automatically adds rules to block future attacks, and remediates endpoints to their last known good state.
- Threat intelligence can detect multi-stage APTs and automate security incident response in milliseconds.
- It prioritizes suspicious processes and applications over known ones to speed up the process. Find and fix problems quickly.
- Provides network security and filtering on endpoints to ensure safe browsing.
- Protect against ransomware, grayware, and new malware.
| What is good? | What else can be improved? |
|---|---|
| Comprehensive endpoint security against multiple threats. | The user interface may be overwhelming to some users. |
| Machine learning for real-time threat detection. | Integration with existing systems can be complex. |
| Central management console simplifies administration. | It can be more expensive to license than other endpoint management tools. |
| Advanced threat intelligence and analytics for proactive threat hunting |
11. Microsoft Defender for Endpoint
Microsoft Defender for Endpoints
Microsoft Defender for Endpoint is a cutting-edge endpoint management solution that provides proactive security, detection and response capabilities, and protection against attacks.
It uses machine learning methods, behavioral analysis, and intelligence-based threat detection tools to discover and respond to emerging threats.
Antivirus, firewall, web protection, application control, and vulnerability monitoring are all integrated to provide a high level of endpoint security. In addition, Microsoft Defender for Endpoint provides comprehensive visibility into endpoint operations, giving security analysts and responders an edge in their work.
feature
- Endpoint Behavior Monitor for Windows 10 collects and interprets data using behavioral signals.
- Cloud Security Analytics collects Microsoft Optical data from online assets and Office 365.
- Third-party partners, Microsoft Search, and security teams add threat intelligence to Defender for Endpoint.
- It helps you detect and respond to endpoint attacks immediately.
- It employs a variety of methods to evaluate warnings and assess their importance.
| What is good? | What else can be improved? |
|---|---|
| Integrates seamlessly with Microsoft security solutions. | Limited non-Windows support. |
| Comprehensive endpoint visibility and insights. | Regular updates and maintenance may improve performance. |
| Real-time advanced threat detection and response. | For optimal performance, regular updates and maintenance may be required. |
| Windows, macOS, Linux, and mobile support. |
12. SentinelOne
Sentinel-1
SentinelOne is an advanced endpoint management system that protects against sophisticated malware. Protect your endpoints from cyber threats in real time with behavioral AI.
It is one of the most efficient endpoint management systems that uses AI for real-time threat prediction, detection, and response. With SentinelOne’s endpoint protection, vulnerability management, and automated threat hunting, enterprises can proactively manage and defend their endpoints.
Also included are tools for monitoring servers so administrators can monitor server activity and spot issues before they escalate. SentinelOne has vulnerability management, device control, and data loss prevention capabilities to generally improve endpoint security.
feature
- Continuously compare user behavior to a benchmark.
- Protect data at rest by storing it onsite or in a nearby cloud database.
- Evaluate security settings and infrastructure data to identify vulnerabilities and best practices.
- Study denial of access and policy enforcement data to improve authentication and security.
- Administrators can define rules to detect data misuse, system misconfiguration, lateral movement, and rule violations.
| What is good? | What else can be improved? |
|---|---|
| Behavioral artificial intelligence for advanced threat detection and response. | Deployment and configuration may require technical skills. |
| Rapidly mitigate threats with autonomous response. | Optimal performance requires constant monitoring and updating. |
| We have advanced data loss prevention and vulnerability management. | Small companies or groups with limited funds may find SentinelOne’s solution too expensive. |
| Integration with other security solutions can improve collaboration. |
13. CylancePROTECT
Cylance Protection
CylancePROTECT is a top-tier endpoint monitoring solution that uses AI and ML for threat prevention. It uses predictive analytics and pattern recognition to detect and prevent sophisticated threats and malware in real-time.
The tool runs invisibly in the background and requires no updates or signatures. Cylance PROTECT’s lightweight agent ensures optimal endpoint performance.
It allows for rapid policy management and configuration and provides complete visibility into endpoint activity. Cylance PROTECT’s sophisticated threat hunting capabilities make it easier for security teams to discover and protect against new attacks.
feature
- The desktop gives you options for dangerous or strange files.
- Desktops can handle memory attacks in a number of ways, such as process injection and escalation.
- Check for and stop dangerous scripts in your environment.
- It regulates the connection of USB mass storage devices to company equipment.
- It can detect harmful processes and alert you.
| What is good? | What else can be improved? |
|---|---|
| Artificial Intelligence and Machine Learning Threat Prevention. | Support for older operating systems and systems is limited. |
| They block known and unknown threats in real time. | Adjustments may be needed to reduce false positives. |
| Understand endpoint activity. | Lacks advanced features compared to other solutions. |
| Advanced threat hunting for proactive security. |
14. Atera
Atla
Atera is a complete endpoint management platform that helps MSPs manage endpoints for numerous customers. It handles remote monitoring, patch management, antivirus and malware protection, backup and disaster recovery, ticketing and reporting, and more.
Atera simplifies endpoint monitoring, software and patch deployment, and remote assistance for MSPs. Automated processes, remote monitoring, and patch management help administrators control endpoints from a single console.
Server administrators can leverage Atera technology to monitor performance and identify problems before they become serious. With its low cost and simple design, Atera is an excellent endpoint management solution for small and medium-sized businesses.
feature
- Remote Monitoring and Management (RMM) software allows complete access and control, transforming IT management from reactive to proactive.
- Focus on your mission by automating tedious and monotonous tasks with Atera’s all-in-one IT automation tools.
- User-friendly reporting and tracking.
- Everything you or other users do or say is automatically recorded in a central database.
- Easy-to-use help desk, billing, and reporting tools simplify work and communication.
| What is good? | What else can be improved? |
|---|---|
| Comprehensive endpoint management capabilities. | For some users, the learning curve may be high. |
| Scalable and flexible cloud platform. | Customization may be limited compared to other solutions. |
| Effective ticketing and reporting. | Not all businesses of all sizes can afford this pricing structure. |
| For hosting providers. |
15. Ivanti
Ivanti
Ivanti’s integrated platform helps IT departments automate endpoint management and gain ecosystem visibility and control. Centrally controlling and protecting endpoints with Ivanti is powerful. This includes remote control, device discovery, inventory, software distribution, patching, and security.
IT managers who want to optimize operations will love its automation and OS compatibility. It also has the most powerful server monitoring tools to help administrators spot problems before they become issues.
Ivanti’s customizable rules and procedures improve compliance and IT operations. Ivanti provides detailed endpoint and server performance metrics and reports.
feature
- Fix operating system and third-party program vulnerabilities on Windows, Red Hat Linux, and CentOS.
- Discover, inventory, and patch powered-on and powered-off physical PCs, VMs, and templates.
- Give authorized users access to applications and services without requiring IT to manage huge lists or manually restrict users.
- Apply “appropriate management” and “just-in-time management.”
- Flexible, preemptive rules can help limit system access to trusted programs.
| What is good? | What else can be improved? |
|---|---|
| Complete endpoint management. | It’s complicated to set up and configure. |
| Unified platform, simplified management. | Advanced features may require training. |
| Automation features increase efficiency. | Deployment may affect system performance. |
| Powerful threat detection and vulnerability management security. |
16. Sophos
Sophos
Sophos controls and protects enterprise endpoints through a variety of capabilities. Sophos simplifies endpoint management, security policy, and compliance for IT managers. It includes tools for device classification, software and patch management, and remote control.
To protect endpoints, it offers antivirus, firewall, browser filtering, and data encryption. Sophos lets you centrally monitor and protect your organization’s endpoints. Advanced threat detection and mitigation capabilities quickly detect and mitigate security threats.
This top-rated server monitoring system protects servers with remote server termination, application restrictions, and intrusion detection. Sophos’ simple design fits businesses of all sizes. The admin panel simplifies setup and update management and unifies endpoint visibility.
feature
- With enhanced visibility into unsafe activity, suspicious traffic, and advanced threats, you can regain control of your network.
- Next-generation security tools like deep learning and intrusion prevention keep your company safe.
- Automated threat response immediately isolates infected systems on your network to prevent the threat from spreading.
- Identity-based policies and unique user risk assessments give you the information and permissions to restore control to your users before they threaten your network.
- Policy-based email encryption, DLP and anti-spam keep your email safe from spam, hackers and data loss with our unique all-in-one protection.
| What is good? | What else can be improved? |
|---|---|
| A complete endpoint management and security suite. | Some users found the Sophos solution difficult to implement and manage. |
| User-friendly interface and management console. | Support response times vary by subscription level. |
| Effective policy implementation and compliance. | Sophos’ acquisition by Thoma Bravo may affect product direction and support. |
| The solution is scalable to suit organizations of all sizes. |
17. BlackBerry Unified Endpoint Manager
BlackBerry Unified Endpoint Manager provides comprehensive endpoint management by integrating security, monitoring and configuration across different devices, ensuring consistent protection and control across complex IT environments.
The tool provides a centralized dashboard that simplifies management of a variety of endpoints, including mobile, desktop, and IoT devices, improving efficiency and simplifying administrative tasks.
BlackBerry Unified Endpoint Manager emphasizes security with advanced threat detection and response capabilities to help protect data and maintain compliance across all managed devices and applications.
feature
- Provides centralized management for various endpoint devices, improving security and efficiency.
- Provides advanced threat protection, real-time monitoring and automatic response to potential security breaches.
- Facilitates seamless integration with existing IT infrastructure and enterprise applications to streamline operations.
- Enables remote management and troubleshooting, reducing downtime and improving overall endpoint performance.
- Provides comprehensive reporting and analytics to make informed decisions and optimize endpoint management strategies.
| What is good? | What else can be improved? |
|---|---|
| Provides comprehensive management for a variety of endpoint types, including mobile and desktop. | There are limited customization options for specific device management settings and policies. |
| Provides strong security features to prevent data breaches and unauthorized access. | Costs are high compared to some competitors, which may affect budget constraints. |
| Supports multi-platform environment and integrates well with different operating systems and devices. | It supports multi-platform environment and integrates well with different operating systems and devices. |
18. Palo Alto Networks
Palo Alto Networks
Palo Alto Networks provides endpoint management solutions that help enterprises protect their endpoints from sophisticated cyberattacks. Their platform combines Next Generation Antivirus (NGAV), Endpoint Detection and Response (EDR), and Threat Intelligence to provide comprehensive endpoint protection.
Palo Alto Networks enables effective management and monitoring of all of an organization’s endpoints by providing centralized visibility and control of these devices.
To proactively protect against sophisticated attacks, the system uses machine learning and behavioral analysis to detect and block both known and undiscovered threats.
feature
- Access control by type works well when applications are identified by multiple protocols and port numbers.
- User IDs allow administrators to create and apply firewall rules based on individuals and user groups rather than network zones and addresses.
- Threat protection services vary by program and traffic source (Object > Security Profile).
- Palo Alto Networks can replace or supplement your firewall.
- It works in switching or routing systems.
| What is good? | What else can be improved? |
|---|---|
| Complete endpoint security with NGAV and EDR. | Large investments make it difficult to switch security solutions. |
| We have centralized endpoint monitoring and control. | Legacy or uncommon endpoint operating systems are rarely supported. |
| Machine learning and behavioral analytics for advanced threat detection. | For larger companies with complex networks, scalability can be an issue. |
| Integrate into the security ecosystem to share threat intelligence. |
19. Citrix Endpoint Management
Citrix Endpoint Management
Citrix Endpoint Management allows enterprises to securely monitor and manage a wide range of endpoint devices from a central location. Desktops, laptops, phones and tablets can all be managed and monitored from one location.
Citrix Endpoint Management lets IT update security rules, configure endpoints, deploy software, and troubleshoot issues. The product uses data encryption, secure remote access, and application containerization to protect critical data.
Citrix Endpoint Management’s compatibility with other solutions helps in easy VDI setup and management. It is an effective endpoint management solution as it has an intuitive user interface and is compatible with many operating systems.
feature
- Configure it in the Endpoint Management User Console.
- Native mobile email application users can securely access their email using the Exchange ActiveSync endpoint management adapter.
- Protect your apps, data, devices, and mobile networks according to your policies.
- MDM can be used to manage company-owned computers.
- Lock apps and wipe data
| What is good? | What else can be improved? |
|---|---|
| Centrally manage and monitor different endpoint devices. | Without a dedicated IT team, implementation can be difficult. |
| Secure remote access and data encryption. | Technical support may have room for improvement. |
| Integration with Citrix solutions increases functionality. | They have different customer support experiences. |
| The interface is simple and supports multiple operating systems. |
20. Hexnode UEM
Hexnode UEM
Hexnode UEM is an excellent choice for controlling and securing a wide range of endpoint devices. Its centralized management makes it easy for IT to monitor and manage multiple electronic devices simultaneously.
Hexnode UEM allows enterprises to set and enforce security policies, distribute applications, and remotely troubleshoot and configure devices. The tool’s sophisticated features, such as application management, content control, and remote wipe, also guarantee data security and compliance.
Hexnode UEM’s compatibility with a wide range of hardware and software can streamline processes and increase the efficiency of your workflow.
feature
- The application can be easily installed on any platform.
- Businesses and technologies such as Android Enterprise, Active Directory, and Azure AD are interconnected.
- Requires registered users to send SMS messages to multiple devices at once.
- Showcase ads that reflect your brand.
- Mobile phone should be a digital store.
- Quickly deploy small, one-time-use tools.
| What is good? | What else can be improved? |
|---|---|
| Advanced capabilities for application and content management. | The interface can be confusing to newcomers. |
| Cross-platform support and integration. | Technical support could be improved. |
| Hexnode’s interface makes it easy for IT administrators to manage devices. | The size and needs of your organization determine pricing. |
| Remote lock, wipe, encryption, and compliance policies protect sensitive data on the platform. |




