Security researchers have uncovered alarming vulnerabilities in Eight Sleep’s internet-connected smart beds that could allow attackers to infiltrate home networks and compromise connected devices.
According to cybersecurity expert Dylan Ayrey, the $2,000 temperature-regulating sleep system has a Secure Shell (SSH) backdoor that allows remote code execution in addition to an exposed AWS access key, making it “a gateway device for lateral network attacks.”
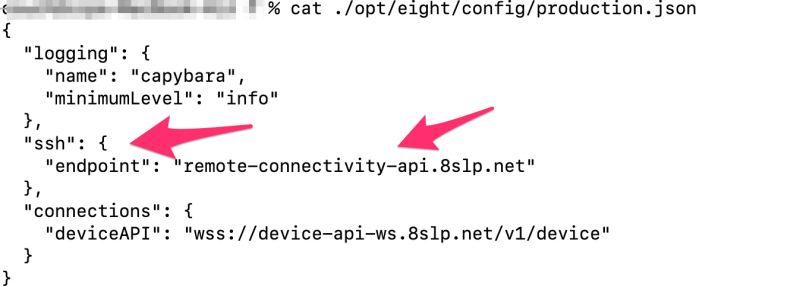
Eight Sleep’s Pod system uses a Linux-based controller running outdated firmware that maintains persistent SSH connections to remote-connectivity-api.8slp.net.
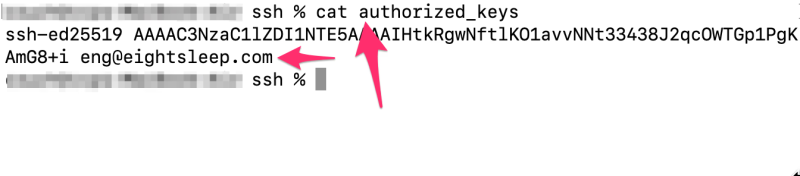
Forensic analysis of the production.json configuration files revealed public keys associated with [email protected], suggesting all engineering staff potentially have root access to customer devices.
This implementation violates basic IoT security principles by:
- Maintaining unauthenticated SSH tunnels (ssh -R 2222:localhost:22)
- Storing private keys in shared repositories
- Failing to implement network segmentation controls
The vulnerability enables threat actors to monitor sleep patterns via pressure sensors (sampling at 50Hz), disable security alarms tied to bed occupancy sensors, and execute privilege escalation attacks using sudo -i capabilities in the embedded Debian OS.
AWS Key Exposure and Network Pivoting
A live AWS access key (AKIAXXXXXXXXXXXXXXXX) embedded in firmware updates fetched from https://update-api.8slp.net/v1/updates/p1/1.
“This allows all of Eight Sleep’s engineers to remotely SSH into every customer’s bed and run arbitrary code that bypasses all forms of formal code review process,” the researcher said.
SSH exposed remotely
Public key authorized to access the device
As a result, compromised beds become pivot points for attacking other network devices.
Mitigation
Security-conscious users have developed open-source alternatives like NineSleep, a custom firmware that replaces Eight Sleep’s dac process with local control via GPIO pins on the Variscite SOM-MX8M-MINI board.
Others have physically modified their systems using $150 aquarium chillers with PID temperature controllers, completely bypassing internet connectivity.
Eight Sleep’s response has drawn criticism, with the company prioritizing DMCA takedowns of GitHub repos over patching vulnerabilities.
This incident underscores the risks of poorly secured IoT devices in critical attack paths. Until manufacturers prioritize security over features, consumers must choose between smart functionality and network integrity.




