Threat actors are actively exploiting a critical zero-day vulnerability (CVE-2024-50623.
The vulnerability stems from an unrestricted file upload and download vulnerability that allows unauthenticated remote code execution (RCE), posing a serious risk to enterprises that rely on Cleo software for secure file transfers.
The vulnerability was first disclosed by security vendor Huntress, which said it stems from an incomplete patch released by Cleo in October.
Despite subsequent patch releases, attackers found ways to circumvent them, leading to large-scale attacks. Huntress telemetry indicates that at least ten businesses were attacked, primarily in the consumer products, food industry, trucking, and shipping sectors.
A new malware family called Malichus has been identified as exploiting a zero-day vulnerability in the Cleo file-transfer software.
The vulnerability, tracked as CVE-2024-50623, affects Cleo’s Harmony, VLTrader, and LexiCom products and could allow an attacker to remotely execute arbitrary code.
Malichus malware Employs 3 Stages
The Malichus malware is divided into three distinct stages:
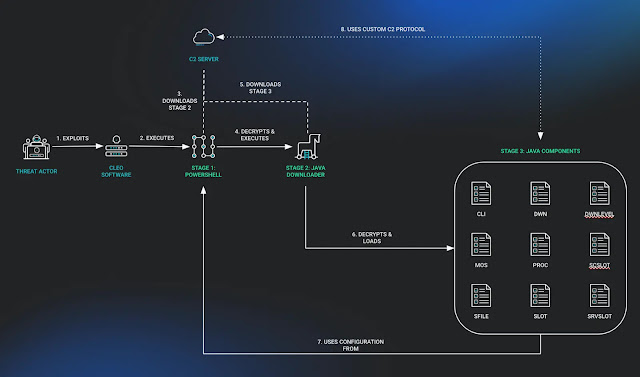
Malichus malware attack chain
Stage 1: PowerShell Downloader
The initial stage involves a small PowerShell loader that is used to prepare the host for further exploitation. This loader is stored as a base64 blob that, when decoded, executes a Java archive named “cleo.[numerical-identifier]`.
It establishes a TCP connection with the command and control (C2) server to retrieve the second stage payload.
The loader also sets a variable called “Query”, which is crucial for identifying the C2 address and the victim’s IP address.
Stage 2: Java Downloader
The second stage involves downloading and decrypting a Java archive using a unique AES key for each payload. This archive contains a manifest file that triggers the execution of the “start” class.
The backdoor retrieves the “Query” environment variable, decodes it to obtain the AES key, and uses it to download the third stage payload over TLS v3.
the downloaded data is then decrypted, revealing a corrupted zip file, which is repaired by removing the first two bytes before extraction and loading.
Stage 3: Java Backdoor / Post Exploitation Framework
The final stage is a modular Java-based post-exploitation framework consisting of nine class files. The main driver “Cli” class is loaded by the previous stage.
The framework supports both Linux and Windows environments, although Huntress found it to be used primarily on Windows systems.
It uses the parameters passed from stage 2 to communicate with the C2 server, identify the exploited system, and manage the malware’s persistence and data theft activities.
Huntress security researchers first disclosed the attack on Monday, noting that the vulnerability was exploited on a large scale to steal data from at least ten companies, primarily in the consumer products, food, trucking and shipping industries.
The attacks began as early as December 3 and increased significantly on December 8.
Cleo has acknowledged the vulnerability and published an advisory urging customers to upgrade to the latest product version (5.8.0.21) to address additional attack vectors.
However, Huntress said that even this patch is not sufficient to protect against the vulnerability observed in the wild. Cleo is preparing new CVE names and expects to release a new patch in the middle of this week
Rapid7 recommends that Cleo customers remove the affected product from the public internet and place it behind a firewall. Additionally, disabling Cleo’s autorun directory can prevent the second half of the attack chain from being executed.
The campaign mirrors previous attacks by notorious groups such as Clop, which have targeted hosted file transfer software to steal and hold customer data for ransom. While attribution of the attack remains unclear, there are unconfirmed reports that the Termite group, known for its recent attack on Blue Yonder, was involved.
The active exploitation of Cleo software highlights the urgent need for strong cybersecurity measures, especially in areas that handle sensitive data. Companies using Cleo products are advised to take immediate action to protect their systems and monitor for any signs of compromise dating back to at least December 3, 2024.
IOCs
| file name | SHA256 |
|---|---|
| cleo.2607 | 6705eea898ef1155417361fa71b1078b7aaab61e7597d2a080aa38df4ad87b1c |
| Command Line | 0c57b317b572d071afd8ccdb844dd6f117e20f818c6031d7ba8adcbd32be0617 |
| down | 429d24e3f30c7e999033c91f32b108db48d669fde1c3fa62eff9da2697ed078e |
| Lower level | f80634ce187ad4834d8f68ac7c93500d9da69ee0a7c964df1ffc8db1b6fff5a9 |
| Moss | 0b7b1b24f85a0107829781b10d08432db260421a7727230f1d3caa854370cb81 |
| process | 1ba95af21bac45db43ebf02f87ecedde802c7de4d472f33e74ee0a5b5015a726 |
| Files | 57ec6d8891c95a259636380f7d8b8f4f8ac209bc245d602bfa9014a4efd2c740 |
| Sc slot | 87f7627e98c27620dd947e8dd60e5a124fdd3bb7c0f5957f0d8f7da6d0f90dee |
| Coin slot | 1e351bb7f6e105a3eaa1a0840140ae397e0e79c2bdc69d5e1197393fbeefc29b |
| Service Slot | f4e5a6027b25ede93b10e132d5f861ed7cca1df7e36402978936019930e52a16 |




