Security researchers have released a sophisticated new kernel exploit targeting Apple iOS devices, dubbed Trigon, which leverages a critical vulnerability in the XNU kernel’s virtual memory subsystem.
The exploit, linked with “Operation Triangulation” spyware campaign that first weaponized the flaw uncovered by Kaspersky, provides attackers with arbitrary kernel read/write primitives without triggering kernel panics—a rare feat in modern iOS exploitation.
Kernel Exploit Targeting iOS Devices
At the core of Trigon lies CVE-2023-32434, an integer overflow in the mach_make_memory_entry_64 function of the XNU kernel.
Discovered in the wild during Operation Triangulation, this flaw allows attackers to create a malicious memory entry spanning 18,000 petabytes—far exceeding physical device limits—by exploiting an unchecked addition of user-controlled size and offset parameters.
The vulnerability bypasses critical sanity checks, enabling the mapping of kernel memory into userspace:
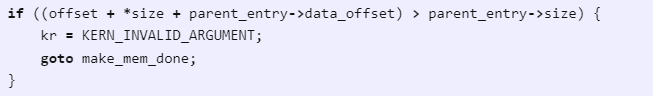
Here, supplying values like size=0xFFFFFFFFFFFFC000 and offset=0x8000 triggers an integer overflow, circumventing the boundary check.
Developed by Alfie CG with contributions from @staturnzz and @TheRealClarity, Trigon’s source is publicly available on GitHub.
Exploit Chain and Technical Mechanics
Stage 1: Privileged Memory Entry Creation
The exploit begins by forging a parent memory entry in PurpleGfxMem—a restricted memory region typically reserved for GPU operations.
By crafting an IOSurface object with the IOSurfaceMemoryRegion property set to PurpleGfxMem, attackers bypass XNU’s vm_page_insert_internal panic checks, as PurpleGfxMem entries lack the internal flag enforced for standard allocations.
This allows unrestricted mapping of physical memory.
Stage 2: Physical Memory Mapping Primitive
Using the oversized memory entry, Trigon maps arbitrary physical addresses into the attacker’s process via mach_vm_map.
By calculating offsets relative to the iboot-handoff region—a bootloader-passed data structure in DRAM—the exploit dynamically resolves the kernel slide and KTRR (Kernel Text Read-Only Region) boundaries.
On A10(X) devices, this involves reading MMIO registers storing KTRR’s lower/upper limits to locate the kernel’s Mach-O header:
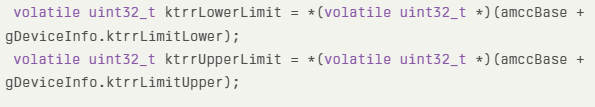
Stage 3: Kernel Read/Write via IOSurface Spray
To bypass Page Validation Hash (PVH) protections, Trigon sprays thousands of IOSurface objects into physical memory.
The exploit identifies non-page-table regions housing sprayed objects by scanning the pv_head_table—a kernel structure tracking page types.
Once located, these surfaces are manipulated to forge task_t and proc_t structures, granting root privileges and disabling sandboxing.
Trigon currently supports A10(X)-based devices (iPhone 7, iPad 6th Gen) running iOS 13–16.5.1. Arm64e (A12+) and A11 SoCs are excluded due to hardware-enforced mitigations:
- Pointer Authentication Codes (PAC) block traditional object corruption.
- PPL (Page Protection Layer) and CTRR (Configurable TRR) lockdown kernel pages, preventing physical reads.
- The iboot-handoff region resides outside mappable memory on newer devices, hindering base calculations.
The exploit’s deterministic nature—achieving success without memory corruption or race conditions—poses a unique challenge to Apple’s security model.
While patched in iOS 16.5.1, lingering risks exist for jailbroken devices and unpatched enterprise fleets.
Researchers emphasize that KTRR/CTRR, once considered unassailable, now requires deeper integration with SoC-level MMU policies to block physical mapping exploits.
The Kaspersky team, who first documented CVE-2023-32434 during Operation Triangulation, plans a detailed analysis of the arm64e-compatible chain used in the wild.




